QBOT – A HTML Smuggling technique to target victims

QBot, also known as Qakbot, QuackBot, and Pinkslipbot, is a Banking Trojan that was first observed in 2007. Today, Qbot is still a vicious and persistent threat to organizations and has become one of the leading Banking Trojans globally. Over the years, it has changed its initial techniques to deliver payloads like using VBA macros, Excel 4 macros, VBS files, exploits like Follina, etc. Recently in Quick Heal’s Security Labs, we have come across a new technique that QBot leverages for its attack. It is called an “HTML Smuggling attack.”
What is HTML Smuggling attack?
HTML Smuggling is an attack vector in which the attacker smuggles encoded malicious script or payload embedded uniquely. It uses HTML 5 and JavaScript to accomplish its task. There are multiple ways to attack with this technique. Some common techniques are:
- Use of anchor tag
The HTML anchor tag “<a>” defines a hyperlink that links one page to another. It can create a hyperlink to other web pages, files, locations, or any URL. Also, if we want to download any file hosted on any server, we can use an anchor tag. For example,
- Use of JavaScript Blob
JavaScript blobs are objects that are a collection of bytes that contain data stored in a file. Blob data is stored in the user’s memory. This collection of bytes is used in the same places where an actual file would have been used. In other words, blobs can be used to construct file-like objects on the client that can be passed to JavaScript APIs that expect URLs.For example, the bytes of the file payload.exe can be provided as input in JS code as a JS blob; it can be compiled and downloaded at the user end. - Use of embed element
It is used for embedding external applications, which are generally multimedia content like audio or video, into an HTML document. It is used as a container for embedding plug-ins such as flash animations.
Why is this technique used?
When the victim opens the HTML attachment, it decodes embedded files and saves them locally. Due to encoded patterns, no malicious content passes through the network, bypassing network filters and firewalls; hence this attack method is gaining popularity among cybercriminals.
QBot Attack Flow:
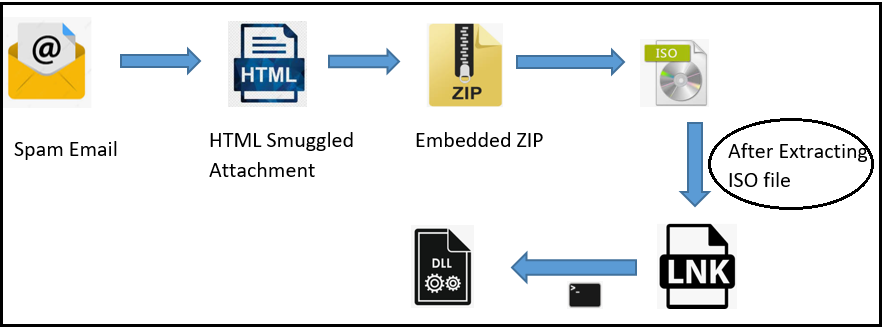
In one of the documents we analyzed, an embedded HTML element was found to be created with the “document.createElement” method. Attackers took advantage of this tag to distribute payloads in zip archives. We can see in the below image base64 encoded data for the zip file:-
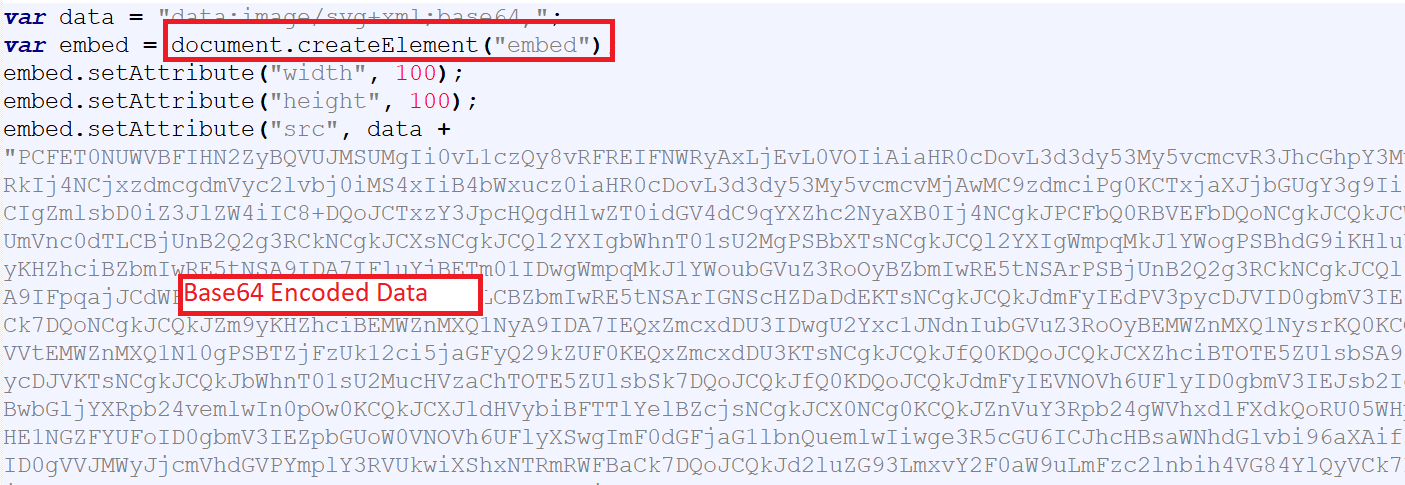
Fig.1- HTML Smuggling Template
While opening an HTML file, it tricks the user as if it is downloading a zip file, whereas the zip is already embedded in an HTML file. The password is highlighted in the image below, “abc555”.
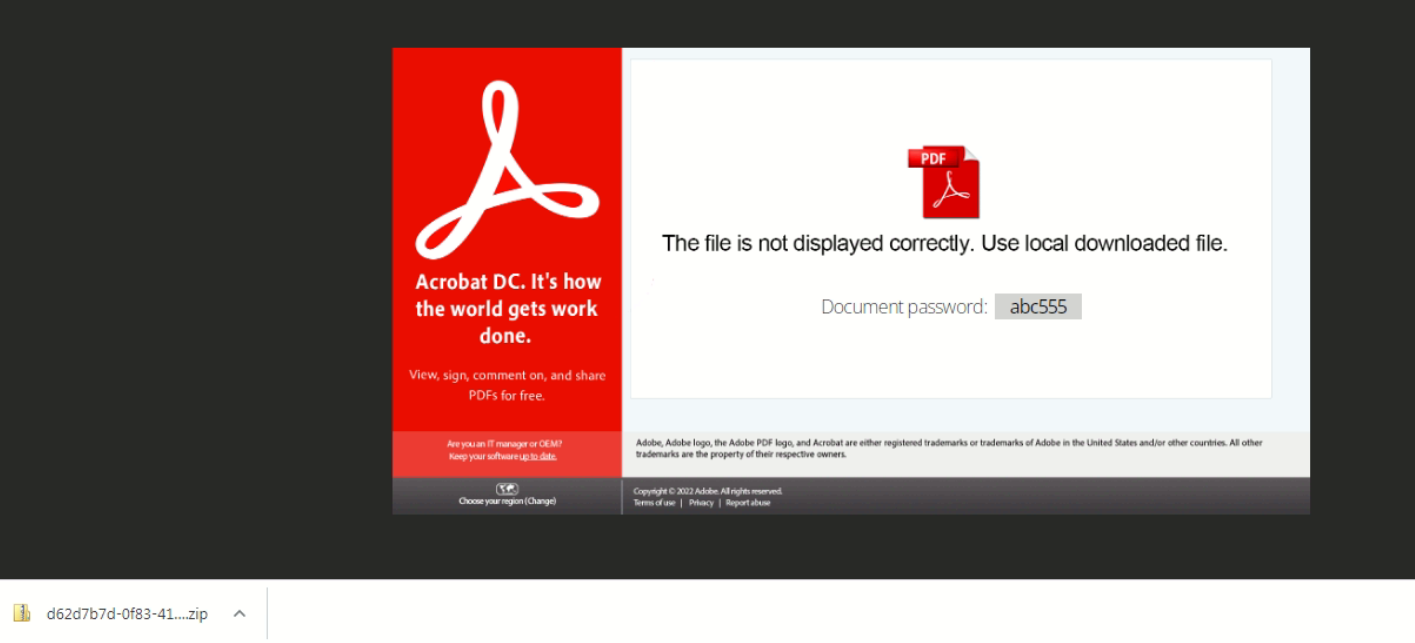
Fig.2 – Zip Download
After extracting the zip file, we get the”REJ_2975” disk image file, which again contains several files.
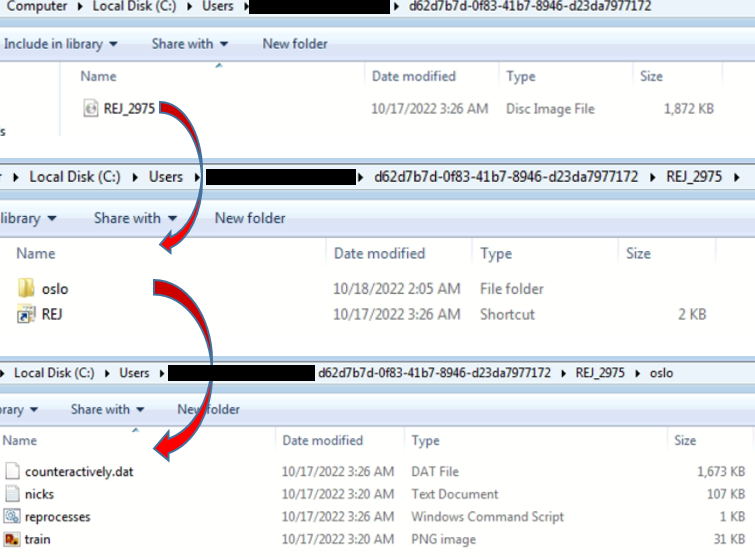
Fig.3 – Extracted files from iso
Shortcut file “REJ” is then responsible for conducting the further attack. This file’s task is to execute the “reprocesses” command script in the “oslo” folder. Subsequently, the command script will execute the final QBot loader DLL file having the name “counteractively.dat” as shown in the following figure:-
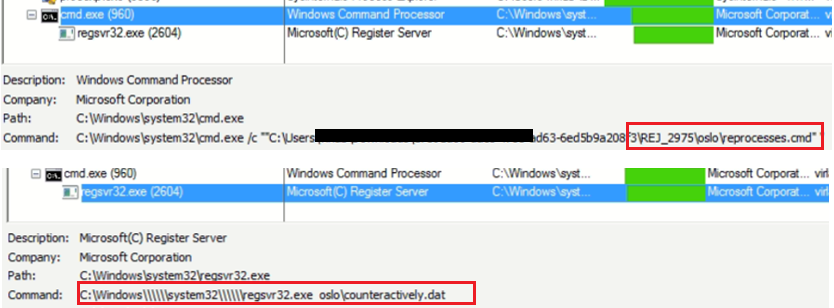
Fig.4 – Execution Commands
Later, the payload is injected in wermgr.exe via process hollowing:-
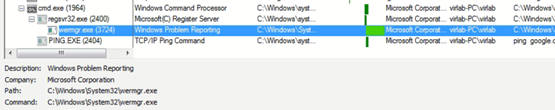
Fig.5 – Execution Commands
DLL Analysis:
This Qbot loader DLL is an x32 bit Delphi compiled binary with no export functions.
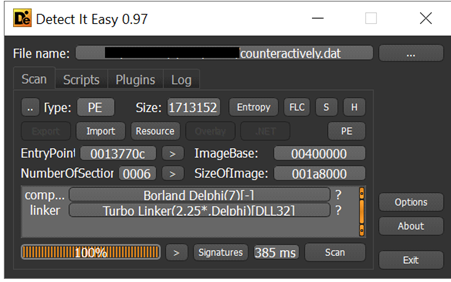
Fig. 6- QBot loader information
Defense Evasion checks are being used by Qbot; in this case, it is for windows defender simulation by checking the file “C:\INTERNAL\__empty.”
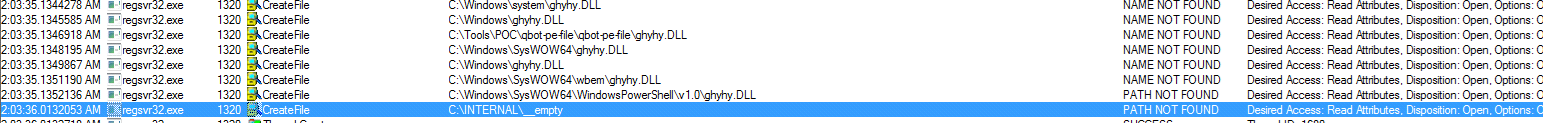
Fig. 7 – QBot checking Windows Defender
Gaining Persistence:
Qbot uses registry entries and self-replication to attain persistence. As the payload gets executed, the Qbot gains its persistence in 2 steps:
- Copying itself to the below-mentioned folder:
%AppData%\Roaming\Microsoft\{RandomStrings} - Creating a registry value pointing to the above payload
Folder Creation and Dropped DLLs are loaded via regsvr32.exe, as shown below:
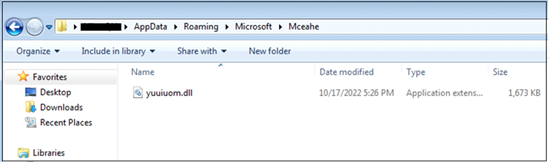
Fig. 8- Folder Creation with a random name
Dumping config data in Registry. In the latest payload versions, Qbot has moved from creating its config file in “.dat” format. Now, it writes its cloned DLL entry in the victim as encrypted registry keys to the ‘HKCU\Software\Microsoft\[RandomString]’ Hive.
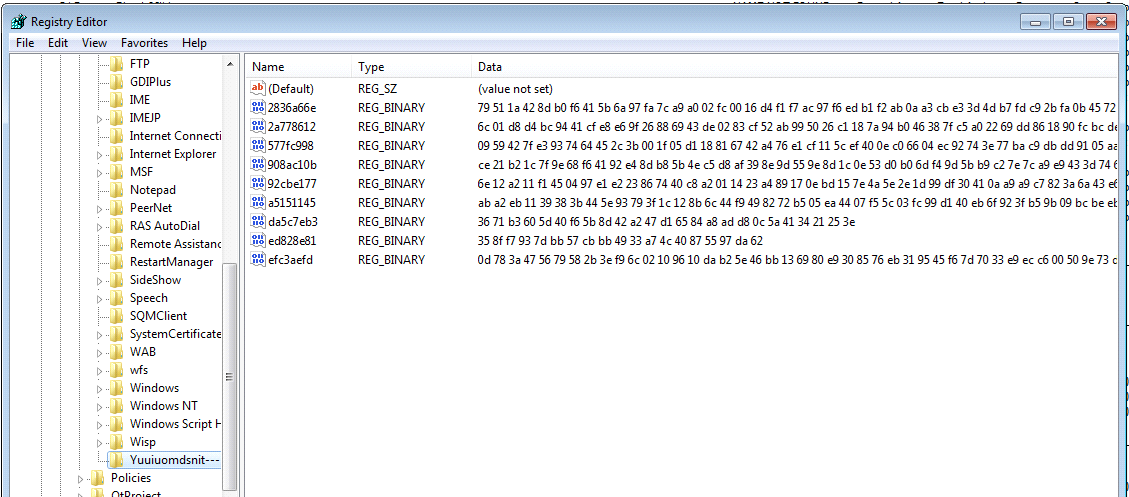
Fig. 9 – Registry Entries
C2 Communication:
As shown in the following figure, injected process “wermgr.exe” is making a connection to hardcoded Ips:-
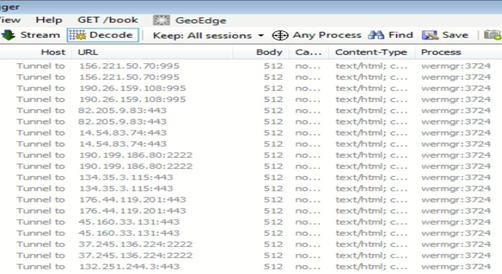
Fig. 10 – C2 Communication IPs
Conclusion:
Disabling JavaScript in most environments is not feasible as too many legitimate systems and web applications require its use. In addition to that, many legitimate JavaScript frameworks make use of obfuscation techniques in order to minimize file sizes and improve the speed of web applications. Hence blocking obfuscated JavaScript is not a practical option. Therefore, users are advised to take utmost care while handling suspicious emails with HTML attachments. Quick Heal customers are already protected from these types of attacks.
IoCs:
Html attachment
Md5: 6783003a0737331c66a0b8fc0a35754d
Detection name: HTML.QBot.47153
QBot loader DLL
MD5: 52EC63A6F7F089862E648112FE8E9F1D
Detection name: Trojan.Qakbot
URLs:
http://156.221.50.70:995
http://190.26.159.108:995
https://82.205.9.83
https://14.54.83.74
http://190.199.186.80:2222
https://134.35.3.115
https://176.44.119.201
https://45.160.33.131
http://37.245.136.224:2222
https://132.251.244.3
http://206.1.216.174
https://1.20.185.200
http://196.89.213.210:995
http://182.183.211.179:995
https://163.182.177.140
http://190.26.159.29:995
https://197.205.161.175
http://91.171..72.224:32100
http://101.109.135.92:995
https://41.97.56.148
https://14.246.151.165
https://94.36.5.99
https://186.18.210.235
https://79.155.159.202
http://190.204.112.15:2222
MITRE Mapping:
| MITRE ID | Technique |
| T1566 | Phishing |
| T1027.006 | HTML Smuggling |
| T1553.005 | Mark of the web bypass |
| T1574.002 | DLL Sideloading |
| T1055 | Process Injection |
| T1112 | Modify Registry |
| T1027 | Obfuscated Files or Information |
| T1218.010 | System Binary Proxy Execution: Regsvr32 |
| T1010 | Application Window Discovery |
| T1082 | System Information Discovery |
| T1071.001 | Application Layer Protocol: Web Protocols |
Subject Matter Experts:
Anjali Raut
Nihar Deshpande
No Comments, Be The First!