What is Phishing? A Deep Dive into the Phishing Attack Mechanisms with Tips

Phishing is a technique used to steal credentials, personal information & financial details of a user. The attacker sends email or text to spoof the target, luring them to open malicious links or attachments.
The most prevalent ways attackers attempt phishing attack are through social networking sites, SMS, and email notifications. We see a sudden uptick in phishing emails used for credential harvesting, which users should be aware of.
Phishing Attack Techniques:
The following are phishing scams techniques along with examples:
1. Spoofed Email Mechanism:
In this technique, the attacker sends a phishing email to the victim containing malicious documents as an attachment, legitimate links, and content in the mail body to spoof the targeted users. This technique is often used for spear phishing attack where targeted users are specific with email IDs known to the attackers.
Example 1 – Targeted victims get an email with the subject “New fax document from Xerox scanner” and an attached document. To view the attachment, it asks for the Microsoft Office credential of the targeted user. Phishers try to spoof the target by adding legitimate content in the email.
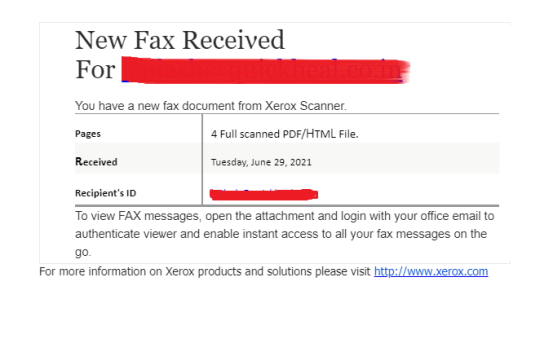
Example 2 – Targeted users get spoofed by an email containing malicious documents but legitimate links and content in the mail body.
The below figure shows one such fake email with a scanned document attached and a message in the Indonesian language.
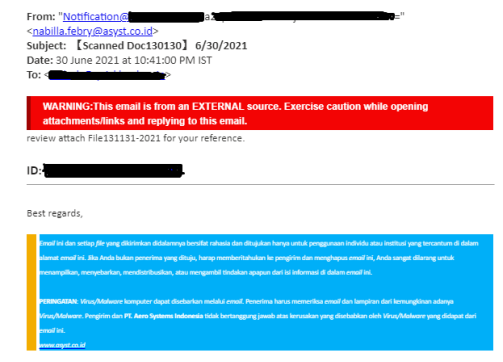
2. Hidden text in Phishing Emails Technique:
Attackers can embed text or phishing links in the hidden fields of the email, which are invisible to the targeted user. The below example shows an email with hidden malicious code in the back-end, and the email appears legitimate to the user.
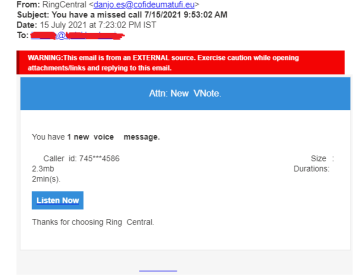
The below image shows an email with some text and links hidden. Typical email security mechanisms might not be able to detect these attacks.
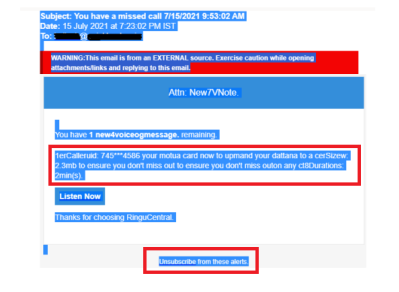
3. Smishing Mechanism:
In this technique, the attacker sends an SMS to the targeted user with malicious links redirecting them to a fake website designed to steal personal information. These malicious links tend to download malicious apps onto the victims’ devices automatically.
Example 1 – In the below example, the attacker tries to steal personal information by using the Covid Vaccination registration. The portal asks to deposit money in advance for vaccination, promising a refund after it gets done, thus creating havoc due to shortage.
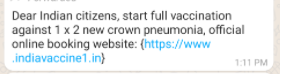
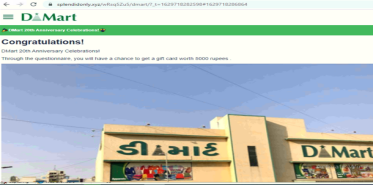
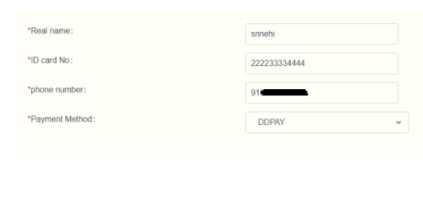 Example 2 – Another example of the Dmart WhatsApp message, where scammers try to fool users with free gift cards. The message claims that DMart supermarket is distributing gifts for free to mark its 20th anniversary.
Example 2 – Another example of the Dmart WhatsApp message, where scammers try to fool users with free gift cards. The message claims that DMart supermarket is distributing gifts for free to mark its 20th anniversary.

The scam message also includes a link to the website, which redirects to a phishing site where users must spin a wheel to win a prize. To claim the award, users are required to share the message with other WhatsApp users.
4. Mail with attached encoded script document:
In this technique, the attacker shares the encoded script to the targeted user that is not readable until decoded, and the code is difficult to understand for regular users. The malicious link is hidden in an encoded code. In some cases, the attached script document contains multiple layers of encoding or obfuscation to bypass the security filters.
The ‘unescaped’ command is a JavaScript function used to decode string data in the example below.
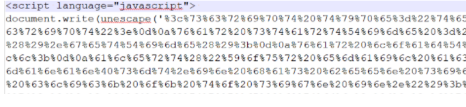
The victim’s email address is already embedded, sometimes in plain text or encoded.
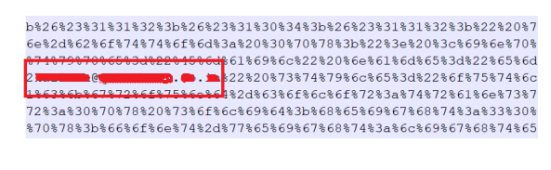
Another example of the embedded script as an attachment in phishing mail contains plain text in the script, but the malicious URL is obfuscated using Base64 encoding.
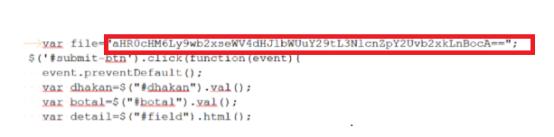
What happens if you fall for the phishing attack?
If the victim is accessing the phishing link from the Mail, it will redirect to fake pages which look similar to the legitimate ones.
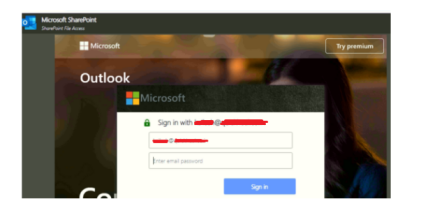
An example is shown below as the Microsoft SharePoint page, which looks legitimate where a targeted email ID is already present and asking for a password.
Another example is Authentic-look fake Adobe Sign-in page. The PDF attachments in the phishing attempts do not contain any malware or exploit code.
Instead, attackers utilize social engineering to mislead victims into visiting phishing pages, to ask for personal information.
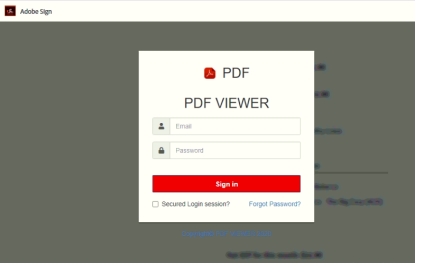
PDF files are distributed through email with a request to provide your email credentials to read or download the file. Aside from a link to a phishing site, PDF files do not contain malicious code. A legitimate Adobe service does not need email and password.
In spear phishing or whale phishing, the victim is not prompted to input their email address as it is already embedded. The victim is asked for their password before being redirected to the legitimate page.
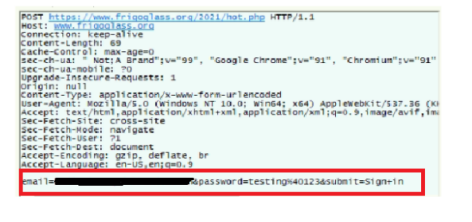
Generally, when a password is provided, it will not throw an error for the first time. Instead, it accepts the entered password. After clicking on the sign-in option, it again redirects to the legitimate page, but in the background, captured traffic is shown below where targeted email ID and entered password is sent in POST request to phishing URL. As a result, the victim has no idea that they entered their password on a fake site. In this way, attackers harvest credentials.
How to keep yourself secure and protected?
1. Check Email Sender details – Check the sender’s account information, email addresses and name, among other things.
2. Verify the Links and suspicious attachments – Always double-check the links’ URLs/domains. Do not access any connected links or attachments in Mail until it has been validated.
3. Content & Spelling mistakes – Always read the message content carefully and double-check the email format. Look for any grammatical errors.
4. Request for personal information– If the message asks to share personal information, don’t give any important information until you validate.
5. Offers that look too good to be true – Before you click on any such link to claim your reward, think the offer that seems too good to be true could be a trap
IoC’s:
Malicious URLs & IPs:
- http[:]//splendidonly[.]xyz/
- http[:]//experiencepo[.]top/
- https[:]//www.frigoglass[.]org/2021/hot[.]php
- https[:]//jsonip[.]com?callback=?
- https[:]//pollyextreme[.]com/service/old[.]php
- https[:]//firebasestorage[.]googleapis[.]com/
- https[:]//lecuris[.]com/invoice/apple[.]php
- https[:]//objectstorage[.]us-sanjose-1[.]oraclecloud[.]com/
- https[:]//i[.]gyazo[.]com/049bc4624875e35c9a678af7eb99bb95[.]jpg
- http[:]//media[.]fc2[.]com/
- https[:]//aysinturpoglucelik[.]com/jr/actions[.]php
- http[:]//f0570529[.]xsph[.]ru/okp/actions[.]php
- https[:]//alergybegonesucks[.]com/tfx/dhl[.]php
- http[:]//www[.]bammsind[.]com/af/UZIE/actions[.]php
- https[:]//mayhutsuahanoi[.]com/
- http[:]//svetpoljoprivrede[.]rs/wp-includes/certificates/login-chk[.]php
- https[:]//loginmicros0ft0nl1newebserver[.]cf/xor/policy[.]php
- https[:]//ttraff[.]link/123
- https[:]//grupodionisio[.]com[.]br/yn/cat[.]php
- https[:]//ceramnegar[.]co[.]ir/bb/barhty[.]php
- http[:]//memorialgarden[.]com[.]br/sureboy/logz[.]php
- https[:]//www[.]chicksinfo[.]com/wp-includes/js/dist/nuru/actions[.]php
- https[:]//lingaly[.]pl/agda/UZIE/actions[.]php
- https[:]//sharemybucketlist[.]com/lie/dhl[.]php
- https[:]//abacus[.]edu[.]np/lastman/accttion[.]php
- https[:]//purplespiritmassage[.]com/send[.]php
- https[:]//rustless-networks[.]000webhostapp[.]com/bebe/Obago[.]php
- https[:]//omuniz[.]com[.]br/omwp/wpcontent/themes/TakedaSan/css/chk
- office[.]php
- https[:]//worldfreeware[.]co/wpcontent/plugins/ygynxqjpyo/mills/
- cald[.]php
- 167[.]172[.]146[.]28
- 3[.]139[.]50[.]24


No Comments, Be The First!