You might get hacked before getting vaccinated
COVID-19 is a stark reminder of longstanding inequities in our societies, and how policies need to pay specific attention to protect and lift the less advantaged in society. It also applies to the privacy policy, device protection and general awareness before installing any application. Such awareness is crucial because miserable people out there are still looking to take advantage of such a pandemic that has already turned our lives upside down.
A renowned mobile application Arogya Setu launched by Government of India for easy contact tracing of people during the Covid-19 pandemic has more than 100 million downloads now. Malware authors could not sit back and let this opportunity slip out of their hands. They misused the name ‘Aarogya Setu’ to plant malicious apps into the end user’s phone. Quick Heal collected many applications from various sources that impersonated the original Aarogya Setu App as mentioned in a previous Quick Heal blog.
Many fake Arogya Setu apps that we found were Spyware using Spynote RAT.
Another set of applications which we came across were patched versions of the official Aarogya Setu application version 1.04, created by patching the official app with the package name “xrcpryfabq.peotrafpop” that contains Metasploit code.
Similarly, much other malware could be put inside the official Arogya Setu app to create a look-alike, such as Droppers, Bankers, Fakeavs, Key-loggers, Spyware, Ransomware and many more out of which one more group found and detected by Quick Heal was a Trojan-Dropper.
For detailed information visit https://blogs.quickheal.com/sure-right-aarogya-setu-app-phone/
We have been hearing about many vaccines out of which few are potentially effective. Now when people have started talking about vaccination, scammers started sending fake messages wherein, they send links that take users to fraudulent websites, or they ask for personal details and payment information, or they just lure people into replying to that text message that may cost them a fortune.
Whereas India is running down a different phase.
Get yourself registered on CoWIN
It feels like we have been fighting Covid-19 since ages, but now we have come to the point where potential vaccines are approved by WHO. The USA has already started vaccinating from December 14, 2020, and India is about to start vaccinating its people in different phases. The online space is rife with lots of speculations around how this phase-wise vaccination would work for masses in India. Few claim that Indian Govt is planning to launch a new app named CoWIN to record data of individuals and use this data later during vaccination. The CoWIN app will be a free downloadable mobile application that will help record vaccine data.
Though CoWIN is not yet ready and not launched, malware authors have already rolled up their sleeves to put their malware inside this upcoming application or impersonate it. We found a fake app named “CoWIN App” with the package name “mobi.androapp.co.c9160”, the developer is “PuzzlersWorld”.

Fig.1 CoWIN App
It has different tabs, but none of them has any functionality. The tabs only show news thread as shown in fig.7 on every tab, but when it is installed on rooted device and the user clicks on “Android app” tab it opens the URL “xxxx://androapp.mobi/appCreator//apk/1872658795fd87db658b8d3.66541642.apk” in chrome that asks to download that application as a new app or as an update to the existing app, for which we will have to enable chrome to install unknown apps as discussed earlier.

Fig.2 Downloading apk file
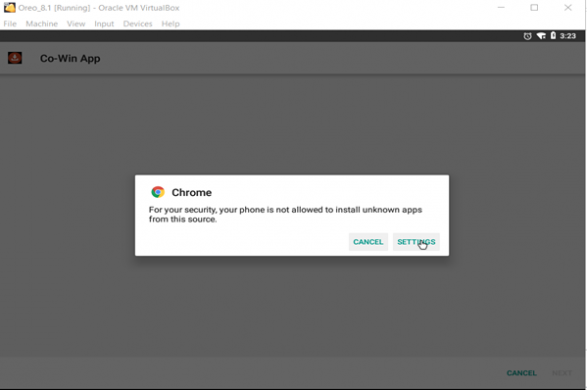
Fig. 3 Asking for permission to install unknown apps
There are many reasons for creating fake apps elaborated in Quick Heal’s technical paper, one of which is a mobile advertisement. Many fakeapps show ads aggressively to generate more revenue in less time. This app is no exception, we found ad modules that create the Ad URL.
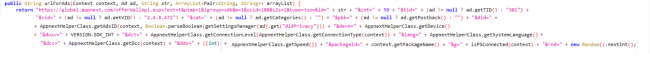
Fig. 4 Creating ad URL
It is downloading the video of specific resolution and length.
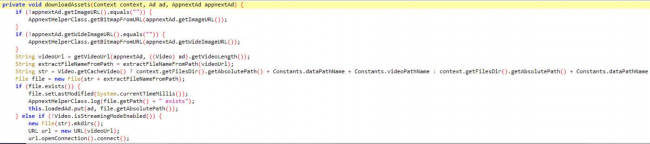
Fig. 5 Downloading ad video.
It also keeps updating the list of ads, that it uses to show to the user.
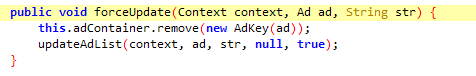
Fig. 6 Force updating the ad list
Arogya Setu app and CoWIN App falls under the category of “FakeApps follow Social Trends” where they are making use of the current situation and deceiving people.
This is just the start, several malicious apps are about to come along with the launch of official CoWIN app, and they might use several other tricks to get into target device either via Google Play Store, Appstore or any other means such as websites, clickjacking, sharing of links via instant messaging apps, emails or SMS, or via direct file transmission. But we need to be aware of tricks that are already discovered and follow certain instructions before installing any application on our system.
Indicator of compromise
| Package Name | MD5 |
| mobi.androapp.co.c9160 | 52f21a04e4deba639863bd8e277698b4 |
Most people install applications from Google Play Store on Android devices and Appstore in iOS devices, and they [Google Play store, Appstore] do apply some security measures to prevent these malicious applications from entering their store. However, one way or another malware authors find their way to reach their targets either through these platforms or any other website, and how people reach those websites is another story among which sharing link via WhatsApp, email, SMS are common ways. Complete application files could also be shared directly through instant messaging apps like Whatsapp, Facebook messenger, Hike and many more. In such cases, the user is prompted for permission to install apps from unknown sources, which the user needs to allow from the settings as shown below.
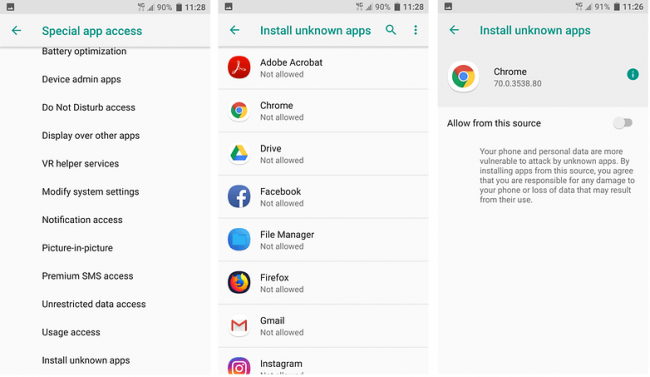
Fig.7 permission to install apps from website
On devices running Android 7.0 Nougat or earlier: Settings->Security->allow installation from unknown sources.
And this is where the user becomes prone to a myriad of exploits, as malicious applications that could have been detected malicious and filtered by Google Play Store policy has now found its way to enter the end user’s device. Hence by mentioning all those tricks used by threat actors and motto that drives their actions to deceive people by preying on their fears, this blog here is trying to help understand how a simple application that looks so benign could be so monstrous, how malware is put even inside official apps like Arogya Setu and CoWIN. We intend to keep our fellow citizens aware and safe by helping them inculcate sanitary practices before installing any app and following certain tips to stay safe, mentioned below.
How to stay safe
1.Download Applications only from trusted sources like Google Play Store.
2.Learn how to identify fake apps in Google Play Store
3.Do not click on alien links received through messages or any other social media platforms.
4.Turn off installation from unknown source option
5. Read the pop-up messages you get from Android system before Accepting/Allowing any new permissions.
6. Malicious developers spoof original Application names and Developer names. So, make sure you are downloading genuine apps only. Often app descriptions contain typos and grammatical mistakes. Check the developer’s website if a link is available on the app’s webpage. Avoid using it if anything looks strange or odd.
7. Reviews and ratings can be fake but still reading user reviews of the app and the experience of existing users can be helpful. Pay attention to reviews with low ratings.
8. Check download count of the app — popular apps have very high download counts. But do note that some fakeapps have been downloaded thousands or even millions of times before they were discovered.
9. Avoid downloading apps from third-party app stores or links provided in SMSs, emails, or WhatsApp messages. Also, avoid installing apps that are downloaded after clicking on an advertisement.
10. Use a trusted anti-virus like Quick Heal Mobile Security to stay safe from Android malware.

No Comments, Be The First!