Pop-up Ad Alert! Beware of Unrealistic Claims on your Smartphones
- What are pop-up advertisements?
- How can these pop-up ads infect your phone?
- What danger can this cause to the victim?
- How to stay safe from such a threat?
As an unsuspecting smartphone user, you could be unknowingly inviting deceptive pop-up apps, and risking your device’s privacy and financial security. In this blog, we’ll be answering all the above questions and also breaking down a ‘pop-up ad’ to reveal how it works. Plus, we’ll share important safety tips so that you can keep your devices protected from these malicious apps.
Beware of Deceptions that ‘pop-up’:
Our daily reliance on smartphone apps can lead to hidden dangers. A tempting ad pop-up, urging you to download it, with the promise of revealing secrets can often hide a serious threat.
Most of the time, such deceitful apps, posing as something useful, can find entry into your device without your knowledge. Disguised as authentic app icons, it can steal private SMS messages and more. This stolen data can be misused to create fake social media accounts, putting your privacy and your financial security at grave risk. Situations can worsen if stolen SMS data contains sensitive financial information like bank verifications and login credentials. In the wrong hands, this can lead to unauthorized access and identity theft, causing great harm to your finances.
Let’s explore a pop-up case that we came across:
Recently, we encountered a website that displayed pop-up advertisements. A website pop-up appears on its own as a window on the website interface, without any intentional action from the user. Generally, these pop-ups are used to show advertisements.Among these ads was one promoting an “xxx Scanner,” illustrated below.
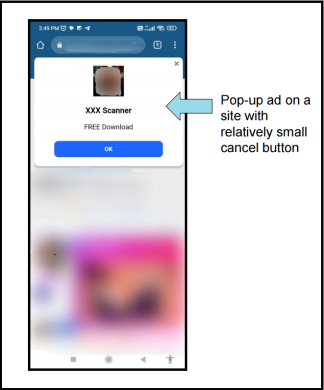
Fig 1: Pop-Up Ad on Site
After clicking this advertisement, it redirected to another website, opening in a separate window. This new site displayed adult images and presented itself as “Thermal 18+.” It showcased the app’s name, icon, and offered an option to update the application. The site aimed to convince users that the earlier pop-up ad for the xxx Scanner app was outdated, and a new version was available.
The image in the figure displayed a text stating: “You have downloaded the old version, update the Thermal camera.” Upon clicking the “update APK” button on this site, the user inadvertently downloaded an app named “Thermal Cam Scanner 6.” (refer Figure 2)
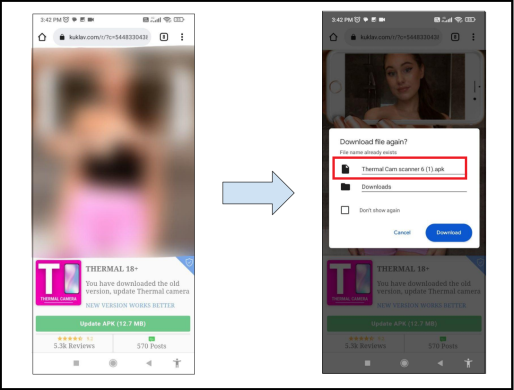
Fig 2: Website Used to Deliver Malicious App
We examined an app obtained from the website.
- After downloading the apk file, users must manually install it, allowing installation from unknown sources.
- When launched, the app asks for the user’s phone number for free access.
- The app requests permissions, including sending and receiving SMS (considered risky).
- It also seeks permission to be the default SMS app for system notifications and receivers.
Application running flow is shown in Figure 3.
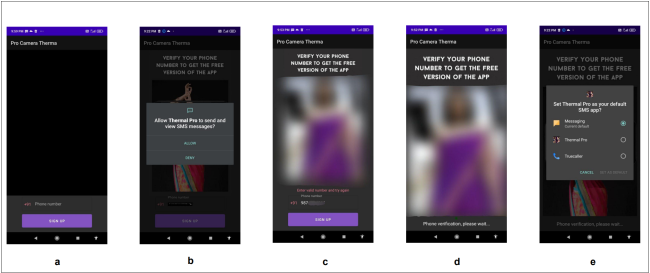
Fig 3: Application running flow
Once the threat actor obtains all necessary permissions, they can create multiple accounts on social media and websites using the victim’s phone number. The malware then by utilizing SMS access, easily retrieves One-Time Passwords (OTPs) sent by these platforms. This enables the threat actor to replicate the victim’s social media accounts and access personal data. Figure 4 displays an OTP received on our phone number upon executing the application.
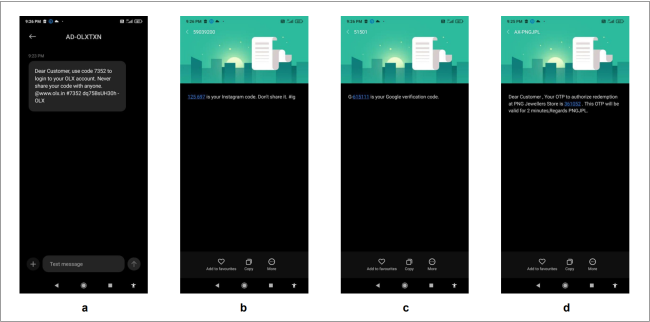
Fig 4: OTP received by our number
In addition to the mentioned risks, the app can hide its icon, making it challenging for victims to find and uninstall. It also gathers SIM-related details, potentially accessing information linked to the mobile network provider.
The application presents a significant threat to both the privacy and financial security of individuals. By accessing victims’ SMS messages, it creates proxy accounts on social media, where sensitive financial information is often shared. With this data, threat actors can easily cause substantial financial harm.
Technical Workings of the Pop-up App.
As mentioned earlier, the pop-up ad for scanner app. redirect the user to another site. The URL of the newly opened site, in the new window of browser is:
hxxps://kuklav[.]com/r/?c=544833043&sub_id {sub_id}&click_id=0be95u3fnbzu3dz7c3#.
We checked for details about “kuklav.com,” and found that this website was recently created in September 2023. Interestingly, its registration is set to expire on 5th September 2024, indicating a relatively short-term registration period, which can be considered unusual as domain registrations commonly span longer durations. (Refer Fig: 5)
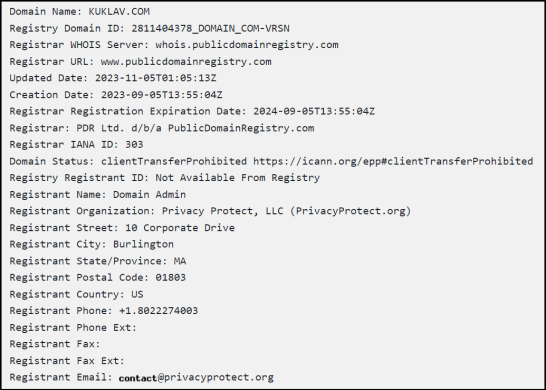
Fig 5: Website Info (Source: whois.com)
Key Observation points about traffic directed to this site (refer Figure 4)-
- 80% of website traffic is from India, with additional traffic from countries like Egypt, Iraq, and Brazil.
- Mobile devices constitute almost 100% of overall usage.
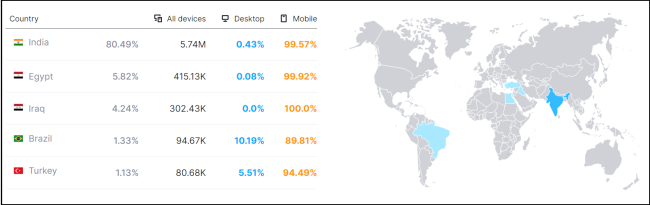
Fig 6: kuklav.com Website Traffic (Source: semrush.com)
Consequently, it’s apparent that this campaign primarily targets mobile users from countries like India, Egypt, Iraq, Brazil, and others.
Additionally, during our investigation, we found GitHub account under the username “Hubasd.” This account hosted similar APK files to the previously mentioned thermal scanner apps. The repository contains files with the name – “Thermal-S7.apk” and “Thermal-S6.apk.”
As we have seen earlier, this application was asking to be set as the default SMS application. If the application is set as default SMS app, it gains the ability to register a broadcast receiver, enabling it to intercept system notifications associated with SMS messages. Figure 7 shows the code for the broadcast receiver. This code runs whenever the malware app receives a broadcast about SMS notifications. In this code, the malware quickly retrieves incoming SMS data and sends it to the Command and Control (C2) center.
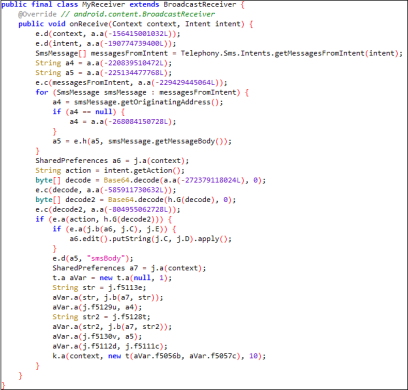
Fig 7: Broadcast Receiver Code
Furthermore, the app has code allowing it to access the device’s location during runtime. Please refer to figure 8 illustrating the code snippet extracted from the application.
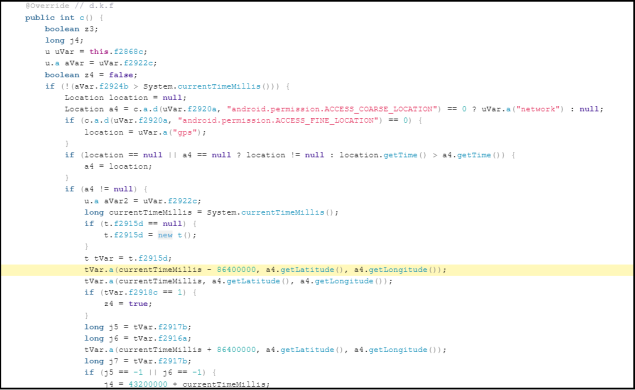
Fig 8: Code to Access Location
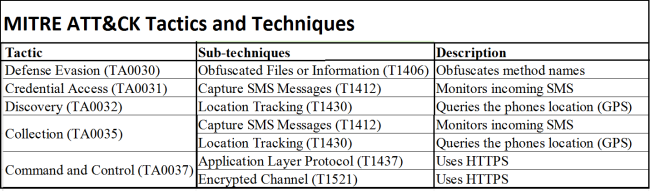
Quick Heal Detection of Deceptive Pop-up Ads.:
Quick Heal detects such malicious applications with variants of “Android.Agent.DCe5a1.”
It is recommended that all mobile users should install a trusted Anti-Virus like “Quick Heal Mobile Security for Android” to mitigate such threats and stay protected. Our antivirus software restricts users from downloading malicious applications on their mobile devices. Download your Android protection here
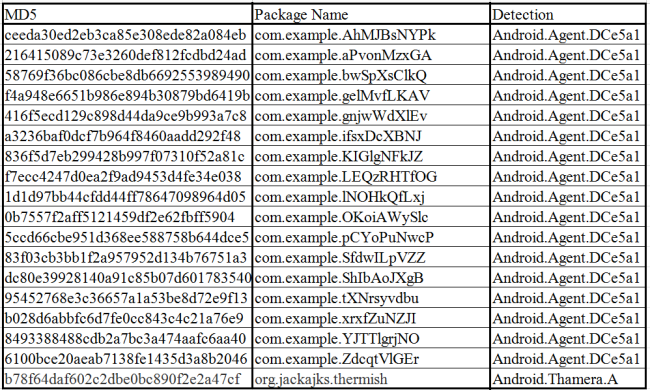
IOCS:
CONCLUSION:
In the world of cyber threats, attackers use various techniques to get into our devices, because of which innocent users become victims of personal and financial risk. One such tactic takes advantage of our browsing habits, where we unknowingly click on links and apps that promise unrealistic benefits in areas like dating, gaming, or gambling. These apps may seem harmless at first but downloading them could seriously compromise privacy and financial security. While not every case leads to harm, it’s always a good idea to stay cautious.
TIPS TO STAY DIGITALLY SAFE from Deceptive POP-UP Ads:
- Download applications only from trusted sources like Google Play Store.
- Do not click on any links received through messages or any other social media platforms as they may be intentionally or inadvertently pointing to malicious sites.
- Read the pop-up messages you get from the Android system before accepting or/allowing any new permissions.
- Be extremely cautious about what applications you download on your phone, as malware authors can easily spoof the original applications’ names, icons, and developer details.
- For enhanced protection of your phone, always use a good antivirus like Quick Heal Mobile Security for Android.
Don’t wait! Secure your smartphones today with Quick Heal Total Security for Mobiles & Smartphones – Buy or Renew Today!
Co-author: Akshay Singla


No Comments, Be The First!