A DEEP DIVE INTO NEW 64 BIT EMOTET MODULES

Emotet is usually delivered by SPAM campaigns containing document files. This self-propagating Trojan is a downloader malware that typically downloads and executes additional payloads. Around Jan 2021, Emotet’s operations were reportedly shut down. However, it has shown its appearance again by the end of 2021. In recent months, Emotet seems to have shifted to 64 bit. This blog will focus on analyzing the new variant and its differences from the previous cosmetic versions.
ANALYSIS (Latest variant) and Differences from previous versions:
Let us analyse the latest variant of Emotet having MD5 da045fce83afdcb9920a0a38b279d33d. Here, we can easily find that the first export function is being used.
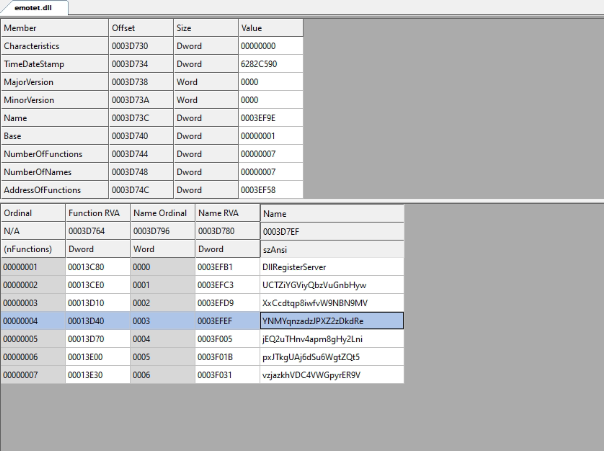
Fig: 1 DLL export functions (64bit latest)
The below image shows a Delphi compiled file having high entropy in the resource section having encrypted data.
Fig: 2 Resource encrypted data
Given below is an image containing data stored in variables. These values are copied onto the stack.
Fig: 3 Encrypted Data stored as variables
This data is decrypted into shell code in the virtually allocated memory, as shown in the image below:
Fig: 4 Decryption loop
Decrypted shell code
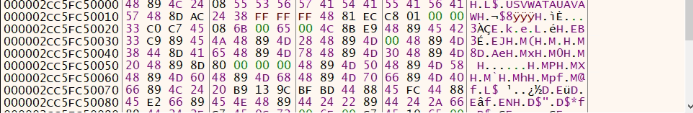
Fig: 5 Decrypted shell code
This shellcode loads the DLL and APIs to be used further.
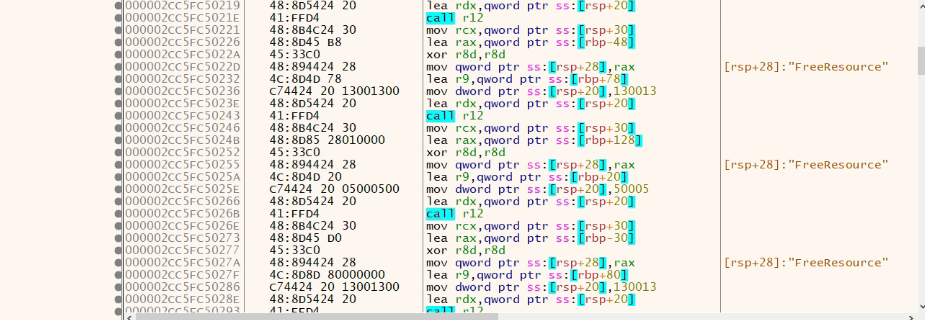
Fig: 6 shellcode loads the DLL and APIs
The encrypted data in the resource section is now decrypted and forms a PE file. Given below is the decryption loop related to the same.
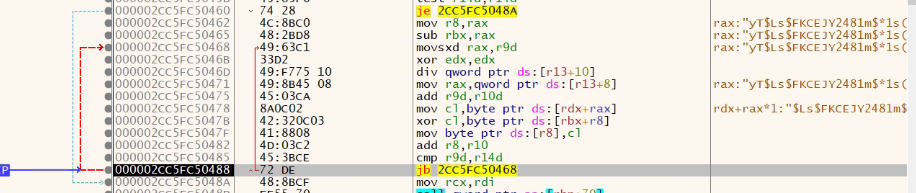
Fig: 7 Decryption loop
Given below is the decrypted inner file
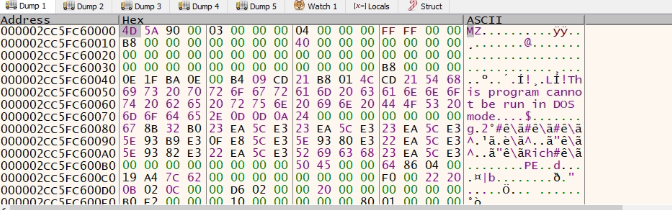
Fig: 8 Decrypted inner file
This decrypted inner file is moved to another virtually allocated memory without PE Header. This memory is virtually protected.
Fig: 9 File without PE header
Let us now explore the inner DLL. This has only one export function.
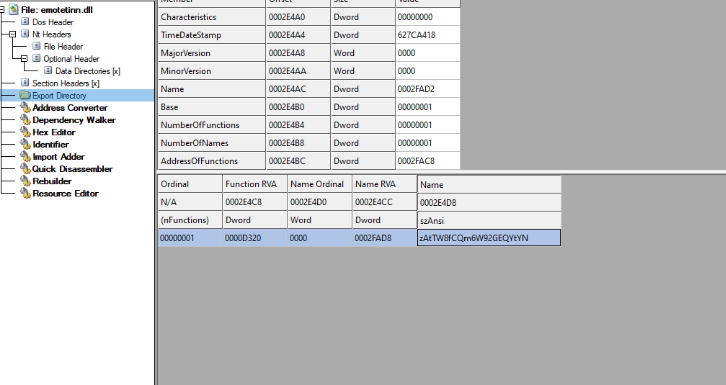
Fig: 10 Inner DLL
This Dll is executed by calling the loader Dll’s 1st export, which indirectly calls the inner Dlls 1st export function.
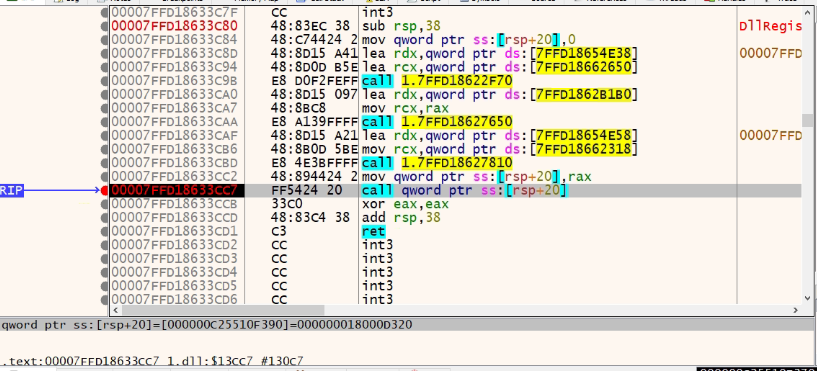
Fig: 11 Dlls 1st export function.
Here we witness that the highlighted statement [rsp+20] points to Inner DLL’s 1st export, showed in the above figure (Function RVA from CFF)
This DLL uses Control Flow flattening and API hashing to make reverse engineering difficult.
In this technique, the code is flattened by several instructions placed inside a loop within a single switch statement that controls the program flow.
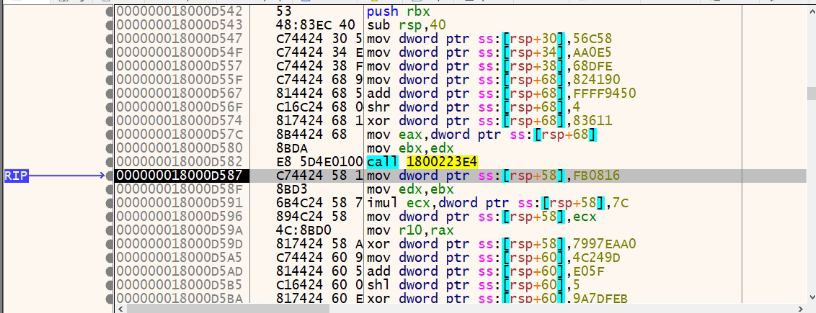
Fig: 12 Control Flow Flattening Technique
It creates the copy of the loader dll (MD5:da045fce83afdcb9920a0a38b279d33d) with a random name in %Appdata% inside a random named folder and subsequently executes from that location.
By setting up a breakpoint on jmp rax, we could fetch all the C2s and the APIs, which are decrypted runtime (present hardcoded inside the file) used in the entire communication.
These new Emotet samples use Bcrypt cryptography functions, which are part of bcrypt.dll. The earlier variants used advapi32.dll Crypt functions.
The malware collects information such as Computer name, Volume ID, Version info, Execution path, etc., and sends it to C2. This data transmitted is encrypted via ECC (Elliptic Curve Cryptography) Algorithm. In the earlier samples, RSA was used.
Looking at the key, we identified that this sample belongs to Epoch5, which has a common key for encryption in all the samples. Let us now look at the encryption process and C2 Communication:
- BCryptFinalizeKeyPair: Keypair of ECC is finalized
- BCryptExportKey: Generated key is exported to the memory blob
- BCryptSecretAgreement: AES key is generated based on the Secret agreement between malware and C2
- BCryptDeriveKey: Derives a key from secret agreement value using SHA256 as KDF
- BCryptGetProperty: Retrieves a property for a CNG object
- BCryptImportKey: To import the key from the memory blob
- BCryptCloseAlgorithmProvider: Closes the handle of the Algorithm provider
- BCryptDestroySecret: Secret is destroyed generated from BCryptSecretAgreement
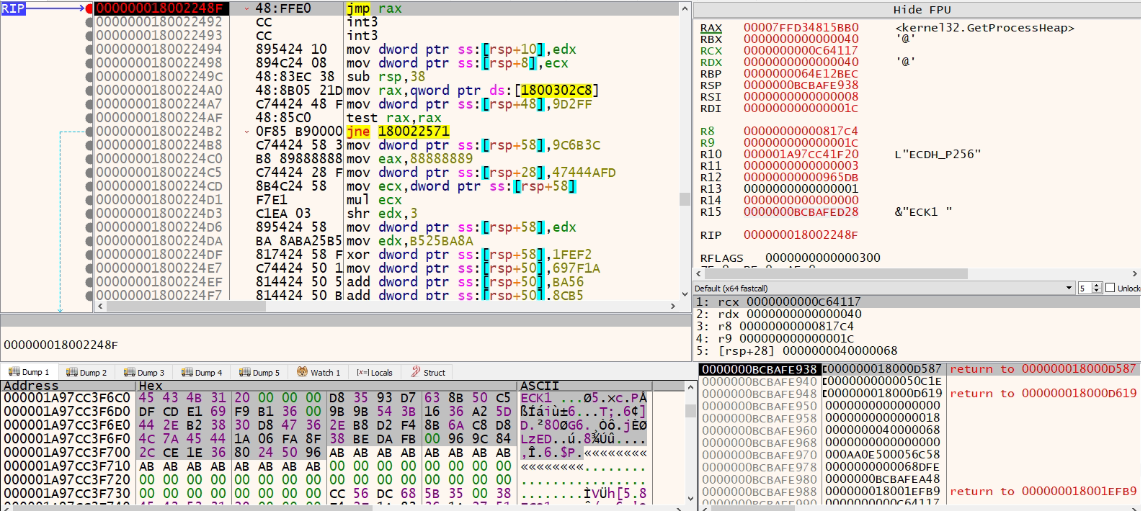
Fig: 13 ECDH Public key
Summarizing the steps:
- EDCH(ECK1 Curve) public key is decrypted and used for encryption of data sent, and ECDSA(ECS1 curve) is used for data verification
- A secret agreement is generated between malware and C2. This agreement value is created from the Public and private key of ECDH
- AES key is derived from a secret agreement value by using SHA 256 as KDF
- Now the message to be sent is constructed, and a hash value is generated.
- The hash value, along with the message, is then encrypted by AES256
- The data consisting of ECK1 public key, AES data, and random bytes are then base64 encoded and sent.
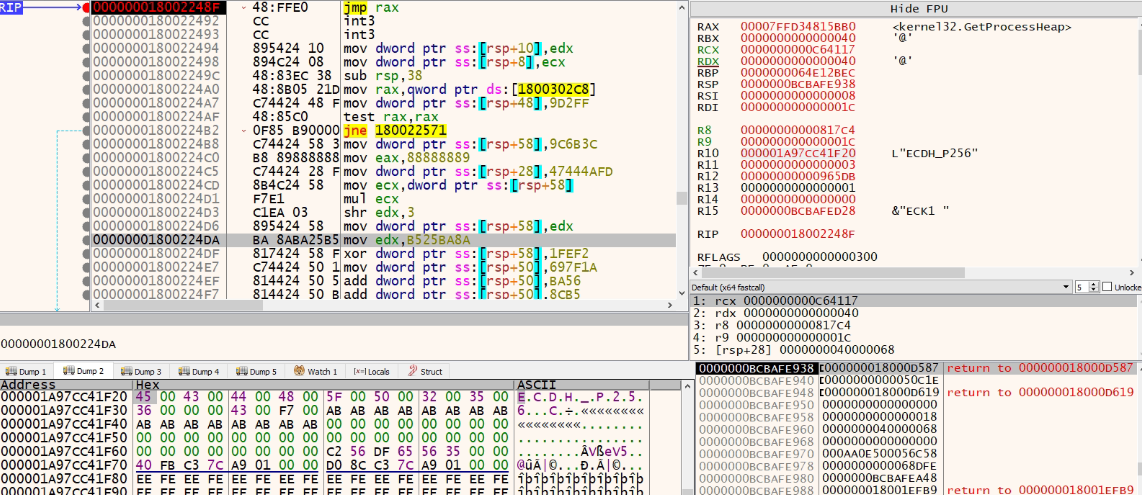
Fig: 14
Decrypted C2 List:
103[.]8[.]26[.]17
134[.]122[.]119[.]23
103[.]133[.]214[.]242
93[.]104[.]209[.]107
37[.]44[.]244[.]177
196[.]44[.]98[.]190
116[.]124[.]128[.]206
88[.]217[.]172[.]165
62[.]171[.]178[.]147
185[.]148[.]168[.]220
103[.]85[.]95[.]4
195[.]77[.]239[.]39
159[.]69[.]237[.]188
190[.]90[.]233[.]66
85[.]214[.]67[.]203
217[.]182[.]143[.]207
203[.]153[.]216[.]46
103[.]42[.]58[.]120
59[.]148[.]253[.]194
68[.]183[.]91[.]111
110[.]235[.]83[.]107
54[.]38[.]242[.]185
85[.]25[.]120[.]45
37[.]59[.]209[.]141
54[.]37[.]106[.]167
103[.]41[.]204[.]169
66[.]42[.]57[.]149
175[.]126[.]176[.]79
54[.]37[.]228[.]122
87[.]106[.]97[.]83
45[.]71[.]195[.]104
195[.]154[.]146[.]35
139[.]196[.]72[.]155
36[.]67[.]23[.]59
5[.]56[.]132[.]177
202[.]134[.]4[.]210
78[.]46[.]73[.]125
202[.]29[.]239[.]162
210[.]57[.]209[.]142
118[.]98[.]72[.]86
207[.]148[.]81[.]119
68[.]183[.]93[.]250
103[.]56[.]149[.]105
178[.]62[.]112[.]199
54[.]38[.]143[.]246
51[.]68[.]141[.]164
104[.]248[.]225[.]227
78[.]47[.]204[.]80
202[.]28[.]34[.]99
188[.]225[.]32[.]231
194[.]9[.]172[.]107
IOC
da045fce83afdcb9920a0a38b279d33d
Detections
Trojan.Emotet.S28135758
Conclusion:
Emotet has now evolved and has become more potent after its comeback. Among other things, it has switched from 32 bit to 64 bit, used CFF along with API hashing, and changed its encryption mechanism from RSA to ECC. It has also used Crypt APIs from bcrypt.dll, whereas earlier, it was using ADVAPI.DLL. It is one of the top malware that path to further additional malware.


No Comments, Be The First!