Stay Away from all these Apps on Google Play

This is a precautionary advisory for all our readers who use Android smartphones. A Trojan detected by Quick Heal as Android.Xynyin.C, is known to have been injected into more than 60 gaming apps available in the Google Play Store.
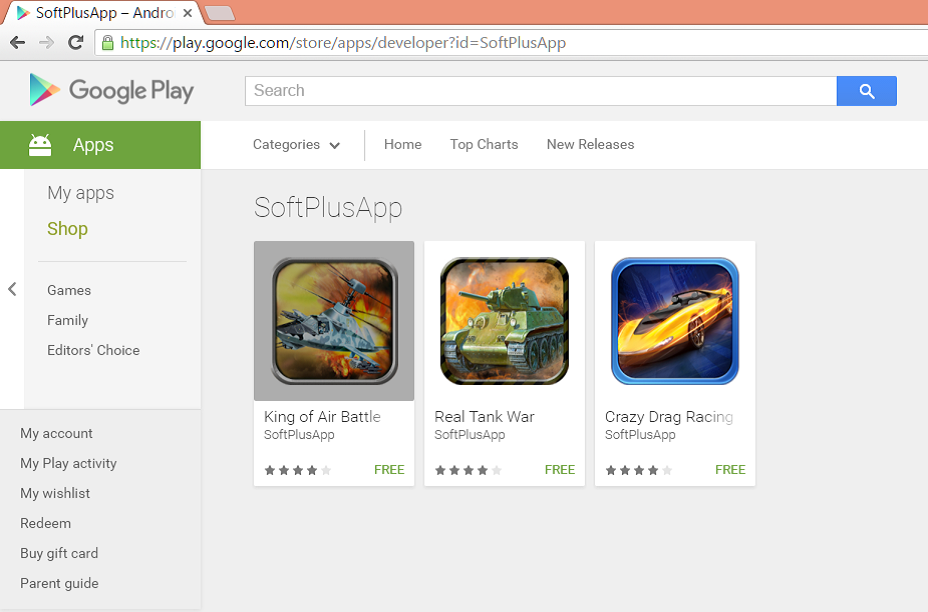
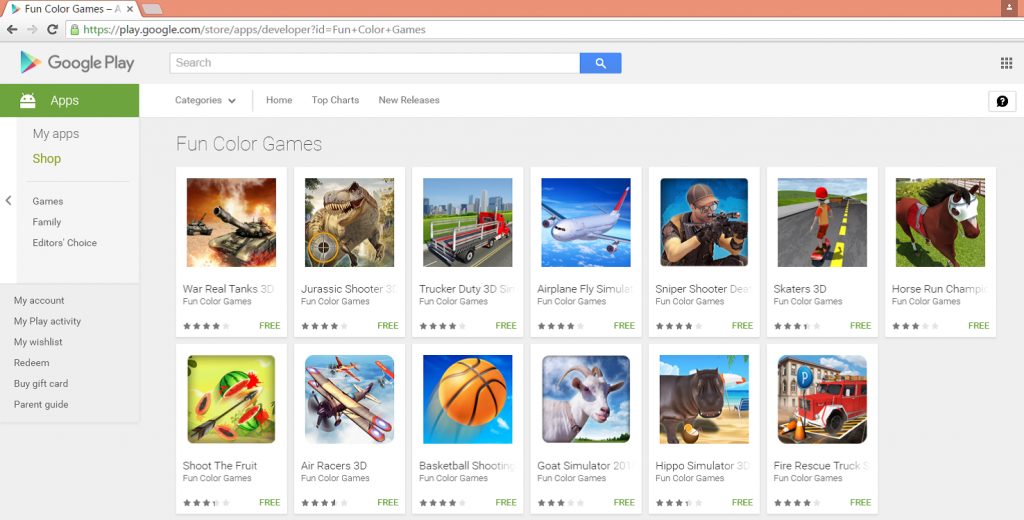
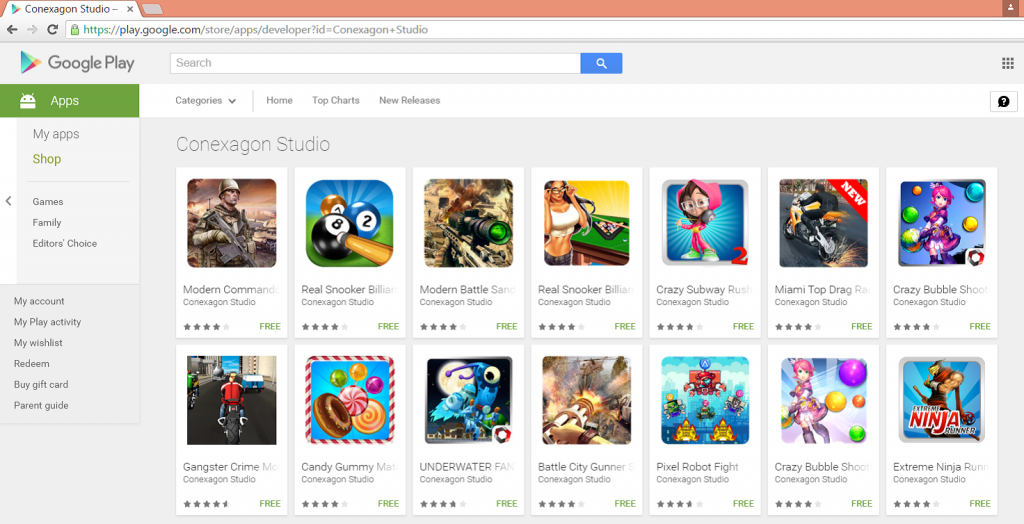
According to the intelligence reports received from our Malware Analysts, the apps that were compromised with this Trojan, belong to over 30 game developers including BILLAPPS, Conexagon Studio, Fun Color Games, SoftPlusApp, and Luckystudio to name a few.
Users are strongly recommended not to download the following apps from Google Play or any third party app store:
Figure 1
Figure 2
Figure 3
Figure 4
What does Android.Xynyin.C do?
Once inside your device, the Trojan covertly sends the following information to the attacker(s):
- IMEI, IMSI (International Mobile Station Equipment Identity, The International Mobile Subscriber Identity)
- MAC address (Media Access Control address – your device’s unique hardware number)
- Current language of the device’s operating system
- Name of the mobile network operator
- Name of your country
- Whether or not an SD-card is present in the device
- Version of the device’s Operating System
- Package name of the malicious app and its version number
- Name of all the apps installed on the device
- Name of all the apps running in the background
Other activities performed by Android.Xynyin.C
- An app compromised with this Trojan, displays unwanted ads to the user. Clicking on any of these ads can trigger the download of other malicious apps.
- The Trojan downloads other apps and prompts the user to install them.
- In rooted Android devices, the malware can silently install and uninstall apps without the knowledge or consent of the user.
What’s more interesting about Android.Xynyin.C?
The Trojan makes use of a unique technique of steganography to evade anti-virus engines. It can download an image file from its Command and Control server. This image file will look like an ordinary file except that it hides some additional encrypted data in it. When a malicious app decrypts the data, a .dex file is retrieved which can be loaded and executed on the fly. And this decrypted code has the capability to install/uninstall other apps silently on rooted device.
Read more about Steganography from this post.
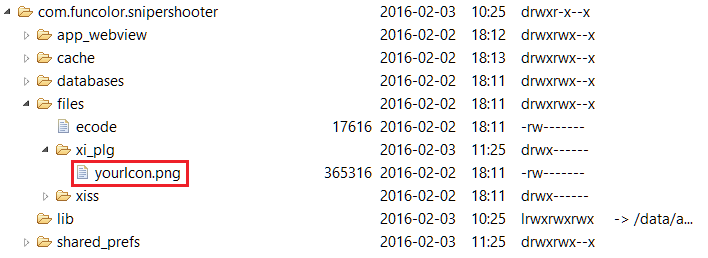
Upon analysis, one of the malicious apps revealed its file structure as shown below (figure 5).
Figure 5
The below image is a snapshot of the image downloaded by the malware, which contains the encrypted data (figure 6).
Figure 6
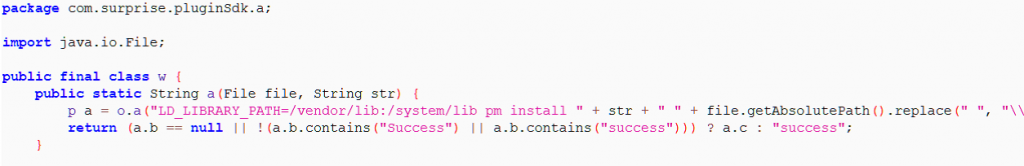
Code snippet which is responsible for silent installation of APKs is shown below. This code is retrieved from “yourlcon.png” which was downloaded from C&C server (figure 7).
Figure 7
It cannot be denied that app developers can add different exploits to the code stored in the image file to get root access. They only need to change the code from the image located at the server without changing the code of the application itself. Such techniques are increasing day by day to evade the detection mechanism of antivirus software. While genuine app developers are using techniques like these to protect their code, malware authors are misusing it as a backdoor to infiltrated targeted devices.
Our readers may like to note that, at the time of writing this post, many of the above listed apps were removed from the play store, but apps from the same developers are still available and they use the steganography technique to extract data from image files. It won’t be a difficult task for these developers to re-embed the code required to execute the code sent from the server. Quick heal detects these less dangerous apps as Potentially Unwanted Program by the name ‘Android.Xynyin.C (PUP)’. Such incidents only cement the fact that even official app stores are not hackproof and users must protect their devices with an extra layer of protection.
ACKNOWLEDGMENT
Subject Matter Expert: Gaurav Shinde, Quick Heal Threat Research & Response Team.


3 Comments
How to uninstall these,, my phone has been affected by these virus,it’s automatically downloading any apps, specially porn apps ,, advertising,, and secretly consuming my data and leave my phone empty of load,,,
Hi Randy,
Thanks for writing in. Our support engineers would gladly help you with this issue. Please visit https://bit.ly/QHChat to chat with us online. You can also raise a ticket at https://bit.ly/Askus and we will get back to you at the earliest.
Regards,
hlw.sir this app not doit