Cerber Ransomware Exposed: A Comprehensive Analysis of Advanced Tactics, Encryption, and Evasion

Cerber is a strain of ransomware that was first identified in early 2016. It is a type of malware that encrypts a victim’s files and demands a ransom for the decryption key needed to unlock the files. Cerber, like many other ransomware variants, typically targets individuals and organizations by encrypting their files and demanding a ransom payment, (usually in cryptocurrencies like Bitcoin), for the decryption key.
Technical Analysis:
The Cerber ransomware’s main payload is a custom-packed sample, so the code is initially unreadable at first. After unpacking the sample, we can find the actual payload 376165CCD556CD74658AFEA9F6F428F9. As shown in Fig 1.
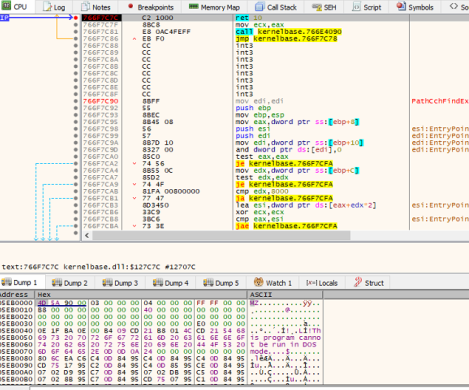
Fig.1: Unpacking of Cerber
When the payload is executed, it checks for a specific mutex. If any of these mutexes are found to be present, the malware will stop its execution. This validation mechanism, involving mutex strings, is built into the ransomware code to prevent it from re-infecting the same machine.
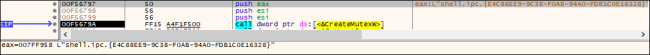
Fig.2: Creating Mutex
Further, it decrypts the data using CryptoAPI, which contains the following information:,
- Blocklisted files, extensions and folders
- Excluded country based on Language ID
- Targeted Extensions
- Base64 encrypted Public RSA key and Ransom Note in HTML format
- Ransom Note in TXT format
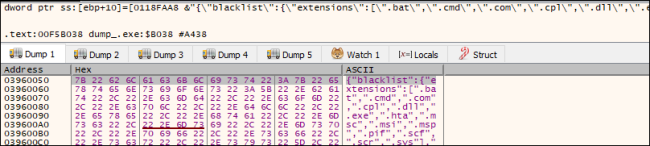
Fig.3: Decrypted Data
The Ransomware has decided to exclude several countries from the attack (namely, Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia, Turkmenistan, Tajikistan, Ukraine, and Uzbekistan).
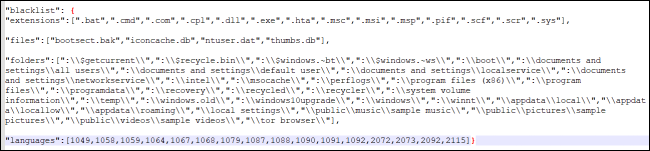
Fig.4: Excluded Extensions, folders and country codes
Then it traverses the decrypted data and uses its value for further encryption processes.
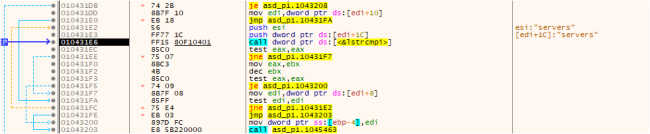
Fig.5: Traversing the Data
Evasion Technique:
Cerber exhibits advanced capabilities by identifying and configuring Windows firewall rules to obstruct outbound traffic from the executable binaries of installed firewalls, antivirus, and anti–spyware products. This tactic aims to impede the communication and functionality of these security tools, potentially enhancing the ransomware’s ability to persist on the compromised system and evade detection. This sophisticated maneuver underscores the evolving nature of Cerber, posing a significant challenge for cybersecurity measures seeking to counteract its impact.
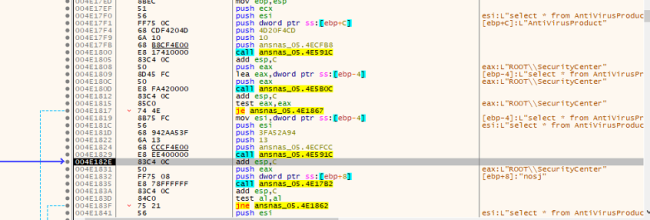
Fig.6: Disabling AV Services
C2 connection:
Cerber ransomware establishes connections to port 6893 on IPs specified by CIDR in the configuration. The communication packet initiation involves a hash prefixed with the Machine GUID (MD5_KEY). The packet concludes with parameters such as PARTNER_ID, OS details, IS_X64 (indicating whether the system is 64-bit), IS_ADMIN (reflecting administrative privileges), COUNT_FILES (the count of files on the system), STOP_REASON (reason for stopping), and STATUS (status information). This communication protocol serves as a method for exchanging data with the specified IPs, illustrating the ransomware’s sophisticated approach to interaction and control within the compromised system.
The communication packet starts with a hash consisting of the Machine GUID: {MD5_KEY} and ending with {PARTNER_ID}{OS}{IS_X64}{IS_ADMIN}{COUNT_FILES}{STOP_REASON}{STATUS}.
With Ip varying form ip”:[“93.107.12.0/27″,”95.1.200.0/27″,”87.98.176.0/22”]
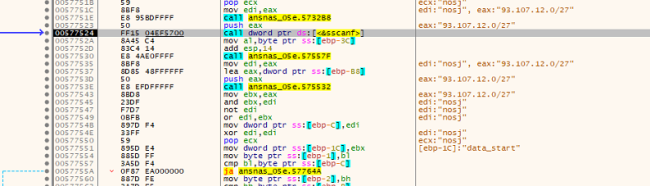
Fig.7: C2 Connection
Encryption:
It drops two files containing the RSA key, which is further used for the Encryption process.
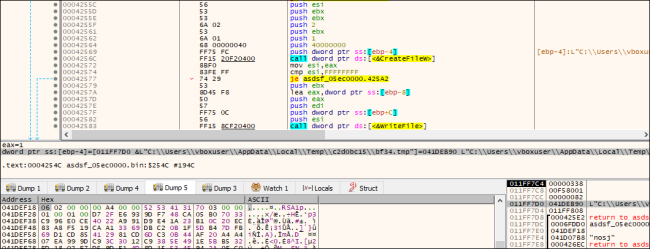
Fig.8: Adding part of the Key in the Temp File
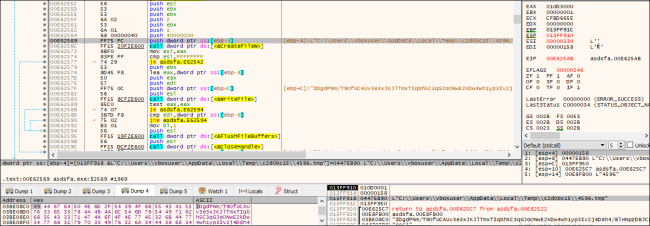
Fig.9: Adding part of the Key in Temp File
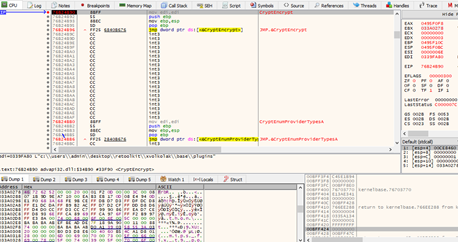
Fig.10: Use of Crypto API
It implements RSA and RC4 algorithms in its encryption routine and the use of CryptoAPI – a separate function that reads and skips the first 1800 bytes, encrypts the rest of the content, and writes back to the file, as mentioned in Fig. 12.
Following the encryption process, the ransomware appends a “.a769” extension and renames the file with a randomly generated string with pattern [0-9a-zA-Z_-]{10}. The figure below illustrates the files that have undergone this encryption and changes in file names and extensions.
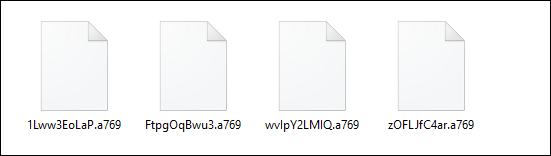
Fig.11: Encrypted Files
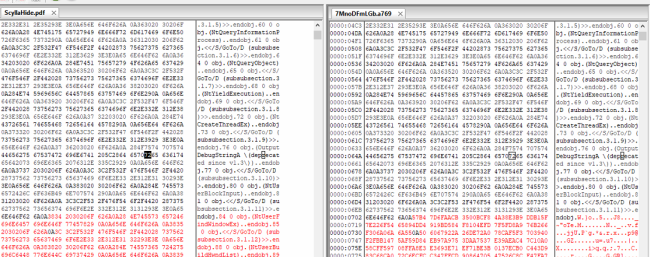
Fig.12: Skipping 1800 bytes from the Header
Ransom notes:
It drops the ransom notes in the folders with the encrypted files, with the name “__R_E_A_D__T_H_I_S__.html” and TXT form. In this ransom note, the threat actors (TAs) instructs the victims to contact them via their TOR website. Furthermore, the TAs issue a warning that if the victims fail to contact within 30 days following the ransomware attack, they will disclose the victim‘s confidential data on public news outlets and websites.
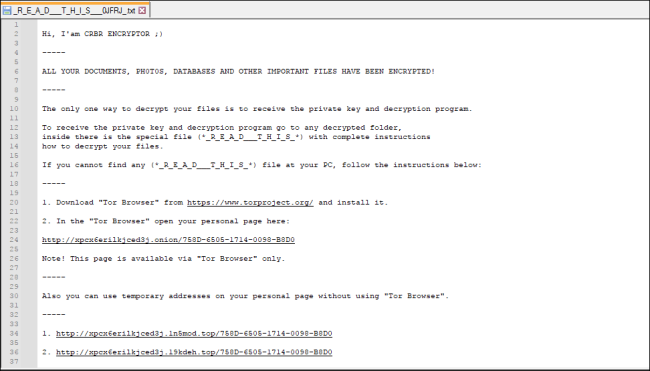
Fig.13: Dropped Ransom Note in TXT Format
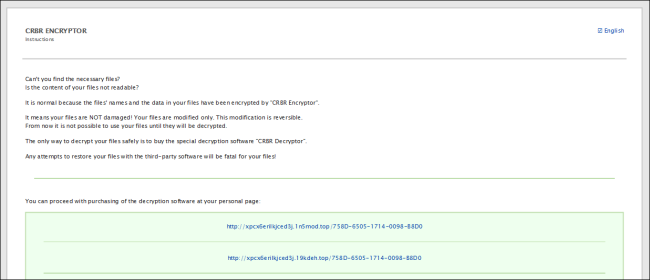
Fig.14_Dropped Ransom Note in HTML File
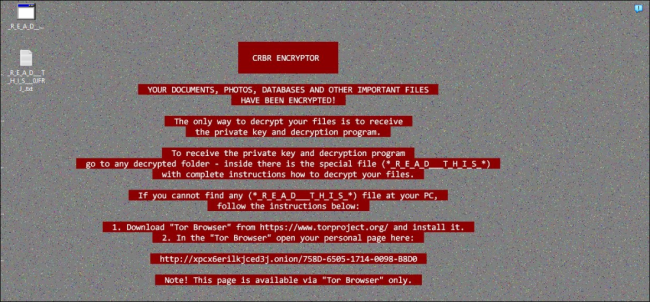
Fig.15: Changed Desktop Wallpaper
Post Encryption:
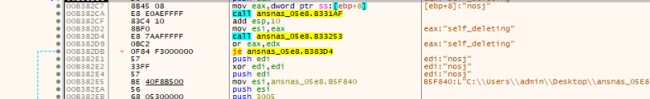
Following infection, the ransomware employs the ShellExecuteA() API function with specific arguments to eliminate its own file from the compromised system. Through this action, the malware orchestrates the removal of its executable, leaving behind solely the encrypted files and the accompanying ransom note. This deliberate self-deletion mechanism indicates an attempt by the ransomware to conceal its presence, complicating post-infection analysis and removal efforts while ensuring the persistence of the encrypted files and the associated ransom demand.
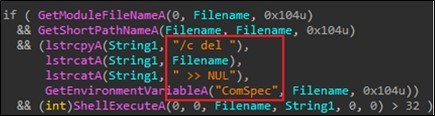
Fig.16: Self-delete using Shell ExecuteA function
Precaution of Cerber Ransomware
Cerber Ransomware is a type of malware that encrypts a victim’s files and demands a ransom for the decryption key. To protect yourself and your computer systems from Cerber Ransomware, or ransomware in general, it is important to take various precautions. Here are a few some steps measures you can take to minimize your risk:
Regularly Backup Your Data:
Back up your important data regularly to an external device or a cloud service. This way, if your files are encrypted, you won’t have to pay a ransom to recover them.
Keep Your Software Updated:
Ensure that your operating system and all software, including your antivirus program, are up to date. Ransomware often takes advantage of known vulnerabilities in outdated software.
Use Strong, Unique Passwords:
Use strong and complex passwords for all your accounts and devices. Consider using a reputable password manager to generate and store strong passwords.
Enable Two-Factor Authentication (2FA):
Enable 2FA whenever possible for your online accounts. This provides an extra layer of security, making it more difficult for attackers to access your accounts.
Exercise Caution with Email:
Be wary of email attachments and links, especially if they come from unknown or unexpected sources. Ransomware can be delivered through phishing emails.
Install a Reliable Antivirus Program:
Install and regularly update a reputable antivirus or anti-malware software. Make sure it includes real-time scanning and ransomware protection features.
Use a Firewall:
A good firewall can help block incoming threats and reduce the likelihood of a malware infection.
Regularly Update and Patch:
Keep your system and software updated. Many ransomware attacks exploit vulnerabilities in outdated software, so patching these vulnerabilities is essential.
Network Security:
Implement network security measures, such as intrusion detection systems, and regularly audit network traffic for unusual activity.
Monitor for Suspicious Activity:
Keep an eye out for any unusual or suspicious activity on your computer or network, as early detection can help stop an infection from spreading.
Regularly Test Backups:
Periodically test your backups to ensure that they can be successfully restored.
Quick Heal Protection:
Ransom.Cerber.S443347
Ransom.Cerber.S126609
Ransom.Cerber.S22591
Ransom.Cerber.S1538045
Conclusion:
Cerber ransomware, first identified in 2016, represents a highly sophisticated threat with advanced evasion techniques. It can configure Windows firewall rules, exclude specific countries from attacks, and employ persistence on compromised systems. It combines RSA, and RC4 algorithms in the encryption process, and uses the self-deletion mechanism post-infection.
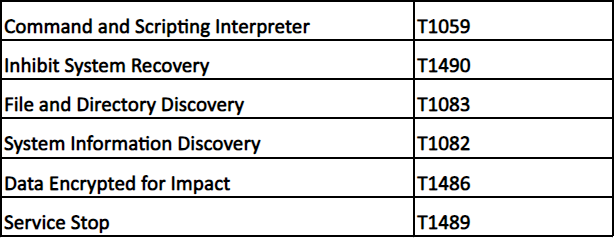
MITRE ATTACK TTPs:
IOCs:
FE1BC60A95B2C2D77CD5D232296A7FA4
376165CCD556CD74658AFEA9F6F428F9
Authors:
Soumen Burma
Vaibhav Krushna Billade



No Comments, Be The First!