Beware: SOVA Android Banking Trojan emerges more powerful with new capabilities

SOVA is an Android banking Trojan with significant capabilities like credential theft, capturing keystrokes, taking screenshots, etc., that can inflict acute harm to the devices that become victims of this malware. This malware has been on sale in the underground market since last year & is suspected of having been bought by some bad actors to harvest critical information from unsuspecting users. Its creators gave the name Sova on an underground forum.
Since last year, SOVA has been targeting Russian and Philippine banks. Since its inception, we have seen its three versions wherein it had 2FA interception, cookie stealing, and injection capabilities. These versions can steal credentials and session cookies through overlay attacks, keylogging, hiding notifications, and manipulating the clipboard to insert modified cryptocurrency wallet addresses.
SOVA relies on the open-source project of Retrofit for its communication with the C2 server.
In the latest version which we have seen recently, SOVA malware seems to have evolved with some new features: –
- It can operate screen clicks, swipes, and copy/paste remotely using commands, i.e., the latest version has VNC (Virtual Network Computing) capability.
- Ransomware capabilities of encrypting files.
- Capability to show an overlay screen on other apps.
- Communicate with a C2 server to exfiltrate a list of installed applications.
- Targets crypto wallets like Binance exchange and the Trust Wallet.
- Steals cookies and keylogging.
- Intercepts multi-factor authentication (MFA) tokens.
This latest SOVA version mimics Amazon and Google Chrome icons to trick users into downloading. At the launch time, it asks for accessibility permission and forces the user to allow it.
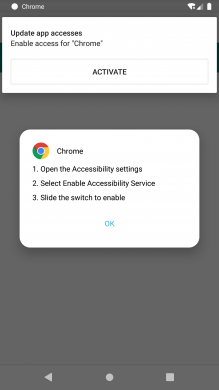
Fig.1 Launch screen of malware Application
SOVA version IOCs with Quick Heal detections:
| SOVA Version | MD5 | Detection Name |
| V1 (2021) | 03f51334546586d0b56ee81d3df9fd7a | Android.ScytheSCF.QJ |
| V2 (2021) | 1698651d6b8fd95574f62b046b4f68e5 | Android.Agent.GEN45035 |
| V3 (2021) | b1101bb941285fc54a21c271ee7bf60e | Android.Agent.A65a4 |
| V4 (2022) | 0533968891354ac78b45c486600a7890 | Android.Agent.GEN50857 |
| V4 (2022) | ca559118f4605b0316a13b8cfa321f65 | Android.Agent.Ad536 |
| V5 (2022) | 74b8956dc35fd8a5eb2f7a5d313e60ca | Android.HqwarSCF.EH |
Quick Heal users are already protected from such threats, including above mentioned SOVA versions.
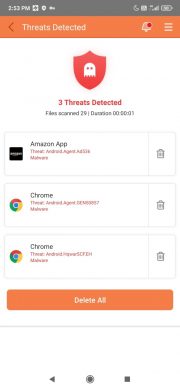
Fig.2 Quick Heal Detecting the malware applications
TIPS TO STAY SAFE
- Download applications only from trusted sources like Google Play Store.
- Do not click on any links received through messages or other social media platforms, as they may be intentionally or inadvertently pointing to malicious sites.
- Read the pop-up messages you get from the Android system before accepting/allowing any new permissions.
- Malware authors spoof original applications’ names, icons, and developer names. So, be extremely cautious about what applications you download on your phone.
- Always use a good antivirus like “Quick Heal Mobile Security for Android” for enhanced phone protection. A trusted antivirus will mitigate all such threats and protect you from downloading malicious applications on your mobile device.
CONCLUSION:
As illustrated above, banking malware uses new techniques to lure users using icons of legitimate applications. These Trojans can cause much harm to the infected devices and are sold in underground markets. They tend to spread via smishing as well as phishing attacks. Users should be aware and not download and install applications from untrusted sources.
Subject Matter Expert
Digvijay Mane
Akshay Singla


No Comments, Be The First!