Cosmos Bank website compromised with RIG Exploit Kit which drops Cerber Ransomware

Update: The incident has been taken care of by Cosmos Bank and its website (URL) is now clean and safe to use.
Compromising popular websites has become a common strategy for attackers to spread infection in a widespread fashion. Attackers exploit unpatched vulnerabilities present on web servers in order to compromise websites. In addition to this, brute forcing login credentials for web admin consoles or FTPs (File Transfer Protocol) is also a preferred way for attackers to gain illegal access to web servers. By using all such techniques, attackers compromise websites and redirect users to other malicious websites.
This blog post discusses how the website of a popular bank in India, the Cosmos Bank, was compromised with the infamous RIG Exploit Kit. The bank’s website ‘https://www.cosmosbank[.]com’ was infected with the RIG Exploit Kit which was delivering the Cerber Ransomware. At Quick Heal Threat Research Labs, we were able to reproduce the series of events that lead to this attack on 20th March 2017. Also, upon tracing back to the recorded logs, it was observed that the infection has been present on the website from 17th March 2017 till date. The bank was notified about the infection on 20th March 2017.
Here’s how it all happened
The below diagram represents a graphical explanation about how this infection took place.

Fig 1. Infection Cycle
- Compromised domain: www.cosmosbank[.]com (port 443)
- RIG EK Landing Page domain: rew.bdwtesting[.]net (185.158.153.111)
- Cerber Post Infection domain: p27dokhpz2n7nvgr.1js3tl[.]top (104.232.37.30)
The infection was spotted on the index page of the Cosmos Bank website. An iframe was injected at the top of the web page, which was redirecting it to a RIG Exploit Kit landing page. The RIG Exploit Kit domain was “rew.bdwtesting[.]net”. The infection is a part of the pseudo-Darkleech campaign (a long-running campaign that uses exploit kits (EKs) to deliver malware).

Fig 2. Cosmos Bank’s compromised web page
The landing page was found to contain heavily obfuscated JavaScript. The RIG Exploit Kit launches the exploits for the targeted vulnerabilities in the browser and its installed components. In this particular case, Adobe flash vulnerability was exploited.

Fig 3. RIG Exploit Kit landing page
After de-obfuscation of the landing page, the exploit kit launches an Adobe Flash exploit.

Fig 4. De-obfuscated RIG Exploit Kit landing page
The Flash exploit payload looks like this.

Fig 5. Flash exploit payload
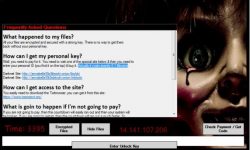
Upon successful exploitation of Flash, the exploit code drops the Cerber Ransomware on the victim’s machine, which is followed by a ransom note as shown below.

Fig 6. Cerber Ransomware’s ransom note
The post-infection activity of the ransomware is shown below.

Fig 7. Cerber ransomware post-infection activity
The Anti-Ransomware and Behavior Based Detection features of Quick Heal and Seqrite products successfully detected the Cerber Ransomware discussed in this blog post.
Indicator of Compromise (IOCs)
rew.bdwtesting[.]net (RIG Exploit Kit)
p27dokhpz2n7nvgr.1js3tl[.]top (Cerber CnC)
8B778E29C7651404A39117B61C4EC8B6 (SWF, Adobe Flash Exploit)
08B921E9749B2C0EF720F84BBB0E5CF5 (EXE, Cerber Ransomware)
Conclusion
Unpatched web servers (web servers that are not applied with the latest software updates) are being targeted by cybercriminals who launch complex attacks where they make use of exploit kits as shown in this particular incident. The RIG Exploit Kit is being heavily used to compromise websites in order to deliver ransomware. We strongly recommend users to update their Windows Operating Systems with the latest security patches and use security solutions such as Quick Heal or Seqrite which has multiple layers of security to fend off such threats.
ACKNOWLEDGMENT
Subject Matter Experts
- Vishal Singh
- Vishal Dodke
- Pradeep Kulkarni
– Threat Research and Response Team


3 Comments
Hi Pradeep,
Thanks for update. Does new Quick heal updates has any prevention measures for this cerber-3 ? And what prevention techniques you would suggest to avoid the risk. I am user of the Quick heal total security.
Hi Mrunmay,
Yes, we do release frequent updates to detect known variants of Cerber 3 ransomware’s. In addition to this we have released Anti-ransomware tool which detects ransomware’s based on their activity. Also we have released Backup tool which helps to take backup of users critical data. Please visit the blog https://blogs.quickheal.com/how-to-prevent-ransomware-from-locking-your-pc/ for prevention techniques.
Very good