WARZONE RAT – Beware Of The Trojan Malware Stealing Data Triggering From Various Office Documents

Warzone RAT is part of an APT campaign named “Confucius.” Confucius APT is known to target government sectors of China and a few other South Asian countries. This APT campaign was quite active around January 2021. Warzone RAT first emerged in 2018 as malware-as-a-service (MaaS) and is known for its aggressive use of “.docx” files as its initial infection vector. The initial payload is known as “Ave Maria Stealer,” which can steal credentials and log keystrokes on the victim’s machine. The advanced version of this malware is currently sold in the underground market for $22.95 per month and $49.95 for three months. The Warzone creators have an official website where it’s up for sale.
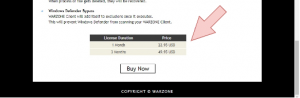
Figure 1: Warzone website showing selling price
These are the various features of the RAT mentioned on the website:
- Remote Desktop & Webcam
- Privilege Escalation – UAC Bypass
- Password Recovery
- Download & Execute.
- Live Keylogger
- Remote Shell
- Persistence
- Windows Defender Bypass
We came across a cracked version of Warzone RAT on GitHub. Here is the screenshot of that repository:
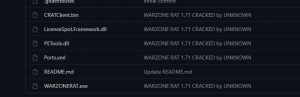
Figure 2: A cracked version of warzone on GitHub
Based on our research, we confirmed that the threat actor is trying to circumvent attacks with a decoy and manipulate users, delivering the next stage payload via template injection technique. In this blog, we are going to talk about “.docx” used as an initial attack vector and how it’s delivering its final payload -Warzone RAT.
Technical Analysis:
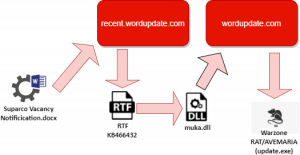
Figure 3: Attack Chain
The various phases of the attack are:
- The victim opens the word document.
- This document further downloads an RTF exploit (CVE-2017-11882).
- Exploit in RTF is triggered and muka.dll is dropped and executed.
- Muka.dll downloads Warzone RAT.
Phase 1:
Here the infection chain starts with a “.docx” file. We can see below the decoy document (Hash: 59ccfff73bdb8567e7673a57b73f86fc082b0e4eeaa3faf7e92875c35bf4f62c). This decoy document was crafted by attackers to induce the victims.


Figure 4: Screenshot from the “Suparco Vacancy Notification.docx”
While executing, it uses the template injection technique to download the next stage RTF exploit. This exploit delivers a dll embedded final payload that connects to the domain to connect to the CNC to download payload Warzone Rat. We can see from the below image.
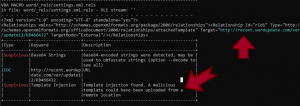
Figure 5: Using Template Injection Technique
The RTF exploit is downloaded through “\word\_rels\settings.xml.rels” file present in document structure using template injection technique as shown below.
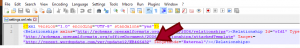 Figure 6: settings.xml.rels containing a link to the template
Figure 6: settings.xml.rels containing a link to the template
Phase 2:
The downloaded RTF file (Hash: 686847b331ace1b93b48528ba50507cbf0f9b59aef5b5f539a7d6f2246135424) contains code that exploits an old vulnerability “CVE-2017-11882”. The flaw resides within equation editor (EQNEDT32.exe), a component in Microsoft office that inserts or edits object linking and embedding (OLE) Objects. We found that muka.dll is embedded in an OLE object.
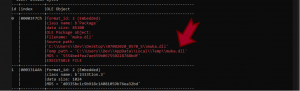 Figure 7: muka.dll embedded in an ole object
Figure 7: muka.dll embedded in an ole object
Phase 3:
The embedded muka.dll file (Hash: 1c41a03c65108e0d965b250dc9b3388a267909df9f36c3fefffbd26d512a2126) contains export function zenu and this dll is used to provide functionalities to other programs. Here is an image showing this:
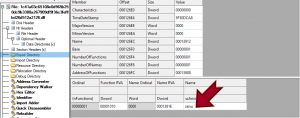
Figure 8: Export directory containing export function zenu
Phase 4:
Upon successful exploitation, the dll connects to a malicious domain (wordupdate.com) which is active nowadays also and downloads the final warzone payload.
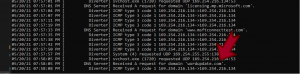
Figure 9: Requesting access to the malicious domain
The Warzone payload is saved as update.exe (Hash: 7dd1dba508f4b74d50a22f41f0efe3ff4bc30339e9eef45d390d32de2aa2ca2b).
Conclusion:
Warzone RAT exploits a pretty old but popular vulnerability, “CVE-2017-11882,” in Microsoft’s equation editor component. This RAT works as an Info stealer malware. Attackers typically spread such malware through document files as email attachments. We recommend our customers not to access suspicious emails/attachments and keep their AV software up-to-date to protect their systems from such complex malware. We detect the initial infection vector as well as the final Warzone RAT as XML.Downloader.39387 and Trojan.GenericRI.S16988580 respectively.
IOCs:
- DOCX:59ccfff73bdb8567e7673a57b73f86fc082b0e4eeaa3faf7e92875c35bf4f62c
- RTF:686847b331ace1b93b48528ba50507cbf0f9b59aef5b5f539a7d6f2246135424
- DLL:1c41a03c65108e0d965b250dc9b3388a267909df9f36c3fefffbd26d512a2126
- EXE:7dd1dba508f4b74d50a22f41f0efe3ff4bc30339e9eef45d390d32de2aa2ca2b
Domains:
- recent.wordupdate.com
- wordupdate.com

No Comments, Be The First!