The Curious Case of Upatre

What is Upatre?
Upatre is a piece of malicious software that downloads and executes other malware.
The name ‘Upatre’ comes from User Agent string “UPdATes downloadER” used by the malware. We have been observing Upatre infections since 2013 at the Quick Heal Threat Research lab. The curious thing here is that, attackers running Upatre campaign have compromised routers globally and are using them to deliver the payload.
Infection Mechanism
Upatre is distributed using 2 techniques:
- As a malicious attachment in spam emails.
- As a specially crafted malicious MS Word document.
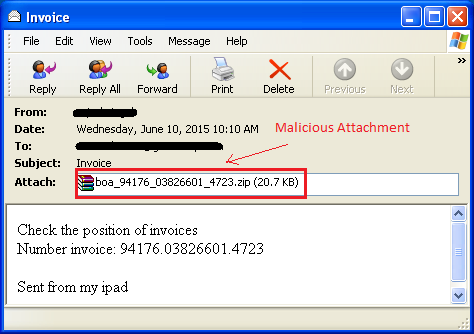
In the first technique, the malware is sent inside a ZIP file as an attachment in the email.
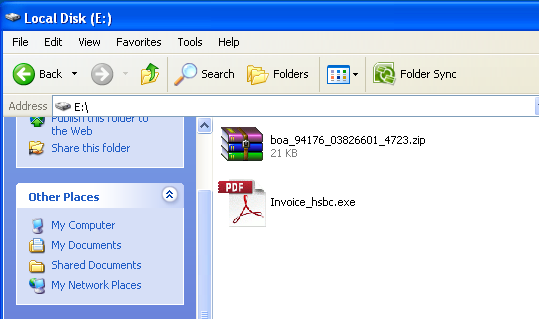
The email asks the recipient to open the attachment; when opened the file appears with a PDF icon. Most users would think that this is a PDF file and will not think twice before opening it.
As soon as the user clicks on the file, the malware gets executed.
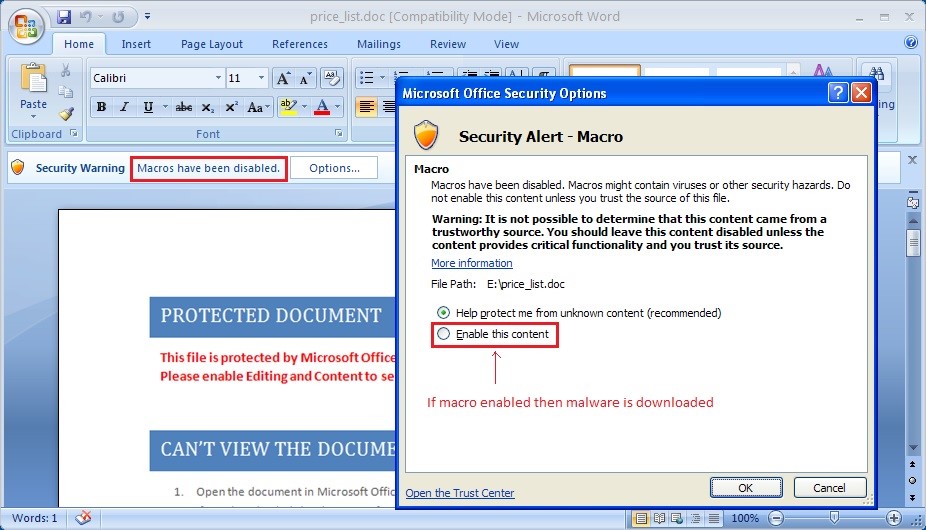
In second technique, attackers use a specially crafted malicious MS Word file as an attachment. The file contains a macro – which when opened, the user is prompted to enable the macro. This macro contains the code to download and execute Upatre. Thus, if the user enables the macro, the code runs in the background and Upatre gets downloaded and executed in the targeted machine.
Once Upatre gets executed in the infected machine, it downloads another malware. In our findings, we have seen it downloading a malware known as TrojanPWS.Dyzap / Dyre – a banking Trojan. It steals user’s banking credentials and relays the information to the attacker.
Technical Details
We have been observing many variants of Upatre. And all those variants can be classified into 2 major categories based on their behavior:
Variant 1 – Drops a copy in %temp% directory and executes it.
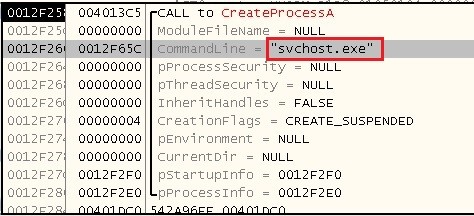
Variant 2 – Creates a process “svchost.exe” and injects a code into it.
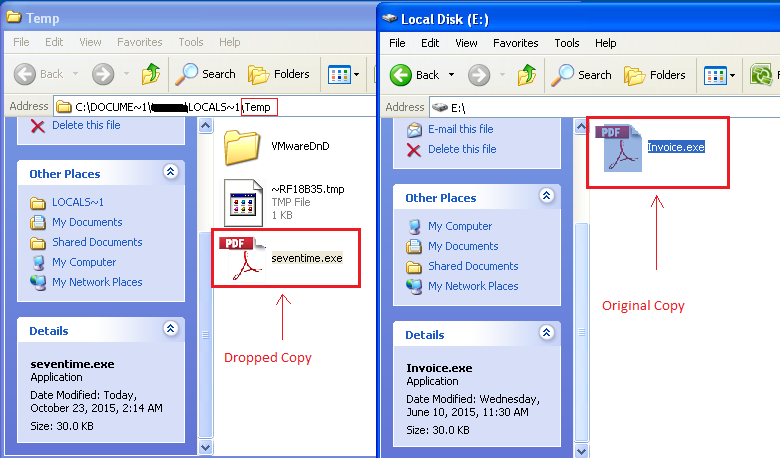
In case of variant 1, the malware first checks if it is running from %temp% directory or not. If not, it will first drop itself in the %temp% directory with a random name, deleting the original file.
In case of variant2, the malware creates the process “svchost.exe” and injects its malicious code into it using a stealthy technique.
The injected code then performs the task of Upatre.
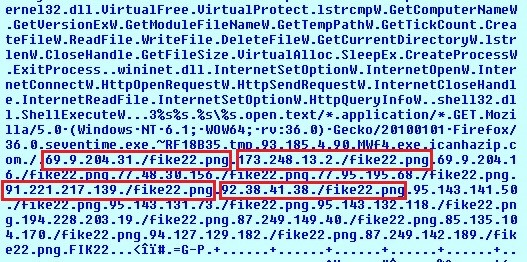
Upatre also brings malicious URL/IP’s in encrypted form and decrypts them at run time.
It then connects to these URLs one by one and downloads another malware. The downloaded malware is kept in an encrypted form. Upatre decrypts this malware and executes it. We are observing that it is downloading a banking Trojan which we detect as TrojanPWS.Dyzap / Dyre.
TrojanPWS.Dyzap / Dyre
The Trojan steals the victim’s banking credentials and sends the information to the attackers. Once executed in the system, it first checks if it is running from %system% directory. If not, it drops its copy in the %system32% directory with a random name and executes from there. It also adds a scheduled task and thus keeps running at fixed intervals. Some variants also inject their code into genuine processes like explorer.exe and svchost.exe to hide their presence from the user.
Dyzap is an advanced banking Trojan which uses the Man-in-the-Browser technique to steal online banking user names and passwords. It monitors the following web browsers to intercept banking transactions so that it can send the stolen credentials to the attacker:
- Google Chrome
- Internet Explorer
- Mozilla Firefox
Also, we have seen it targeting major banks such as ICICI, CITI, HSBC, and other major financial institutions.
Network Communication
There is a typical pattern in which Upatre’s network communication takes place. It consists of 3 stages:
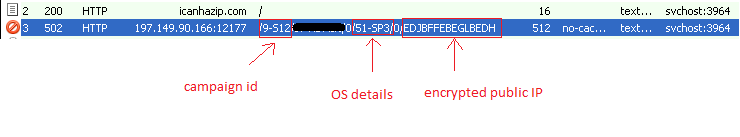
- Getting public IP of the targeted victim
- Sending the infected machine’s information to the attacker
- Downloading another malware
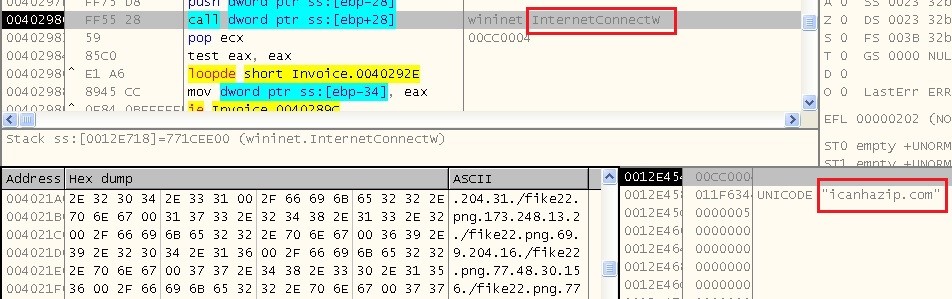
Upatre abuses legitimate websites to retrieve the victim’s public IP address. In most cases, the malware is able to retrieve this information from “icanhazip.com“.
However, we have also seen some variants abusing “checkip.dyndns.org” and other similar services. Thereafter, Upatre encrypts the attained IP address and sends it to C&C server along with other machine details such as username, OS version, Service Pack, etc.
Upatre then connects to the malicious URLs/IPs one by one to download another malware. The malware is kept in an encrypted format on these URLs to avoid getting detected by any network level scanning systems. After successful download, Upatre decrypts this malware, executes it and deletes itself.
C&C communication and Payload Distribution
Malware often use compromised websites to host and distribute malicious software.
However, this time, attackers have gone a step further by hacking wireless routers to deliver its payload, mainly Trojan.Dyre or Trojan.Dyzap.
There are thousands of compromised routers – particularly routers powered by MikroTik and Ubiquiti, communicating with the botnet and distributing other malware.
Possible reasons behind the compromised routers can be:
- Exploiting routers with default login credentials: There are two separate logins to consider. One is for linking over WiFi to access the Internet and the other is for logging into the routers’ internal software for making settings changes. Most people seem to forget about the second one.
- Exploiting known vulnerabilities in the firmware.
Although, the focus of Upatre is mainly on MikroTik and Ubiquiti routers, any router could be compromised to carry out this attack, if it is left in a state that can be easily exploited by hackers.
Safety Measures to Take
- Ensure that the default administrative login credentials are changed.
- Follow best password practices. Read more about this here.
- Submit your Router Username and Password when login page is prompted by the browser.
Default credentials observed in case of Ubiquiti router:
| Username | Password |
| Ubnt | ubnt |
Default credentials observed in case of Mikrotik router:
| Username | Password |
| admin | blank |
Infection Statistics
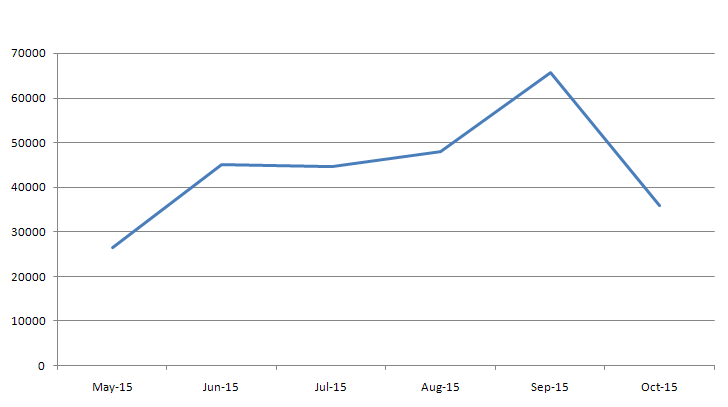
The following graph shows Upatre’s detection over the last 6 months – it shows that the malware was on the rise in the month of Aug to Sep 2015.
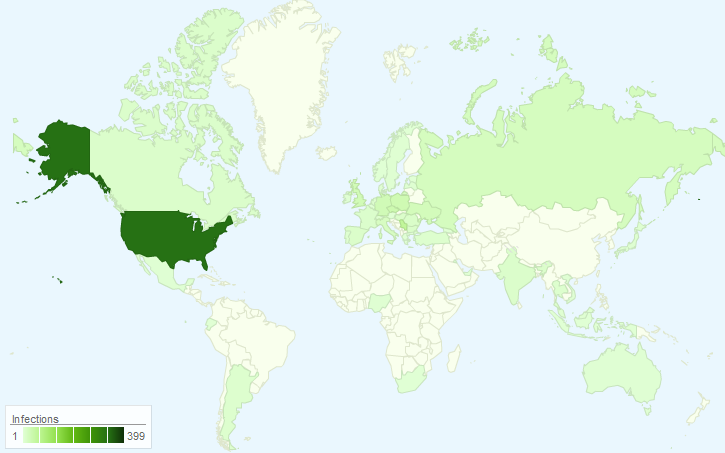
At Quick Heal, we have captured around 18,000 unique URL strings till date. Since multiple files are hosted on a single router, we have 900 unique IP addresses. The following map shows the statistics of compromised routers in the most affected countries.
Conclusion
Upatre is a serious threat to both businesses as well as individuals. And with the use of compromised routers, it can be seen how complex and advanced cyber threats have become. Best security practices and awareness can help us stay protected from such threats. Although the main payload of the malware is Dyre/Dyzap, we have seen it downloading other malware in the past such as Zbot/Zeus and Gameover, which are banking Trojans.
We strongly recommend users to use Quick Heal Safe Banking feature to stay protected from this malware and other such banking related threats. Also, it is essential that you keep all your passwords safe and updated, including those of the devices that are connected to the Internet.
Content Source:
Quick Heal Threat Research and Response Team.
Contributing Subject-matter Experts:
Preeti Kulkarni | Indrajeet Kavitake | Swapnil Patil



1 Comment
Nice information.