Surviving PDF “/Launch” attack
After Didier Stevens revealed about PDF “/Launch” Social Engineering Attack that could be used to launch applications from PDF files, we have received malicious PDF files which use this technique -doc.pdf, Royal_Mail_Delivery_Invoice_[].pdf. These PDF files modify Adobe’s Launch File warning which is prompted to the user before opening embedded non-pdf attachment. As Adobe has mentioned, default option shown is to not execute the file.
If user clicks on “Open” options, it drops and executes embedded VBScript and malicious file.
Below image shows the script from doc.pdf file which drops and executes game.exe.
Quick Heal detects doc.pdf as Exploit.PDF.Pidief and dropped file game.exe as Trojan.Agent.pack.
Users are advised to configure Adobe to disable execution of JavaScript files and opening of non-PDF file attachments with external applications.
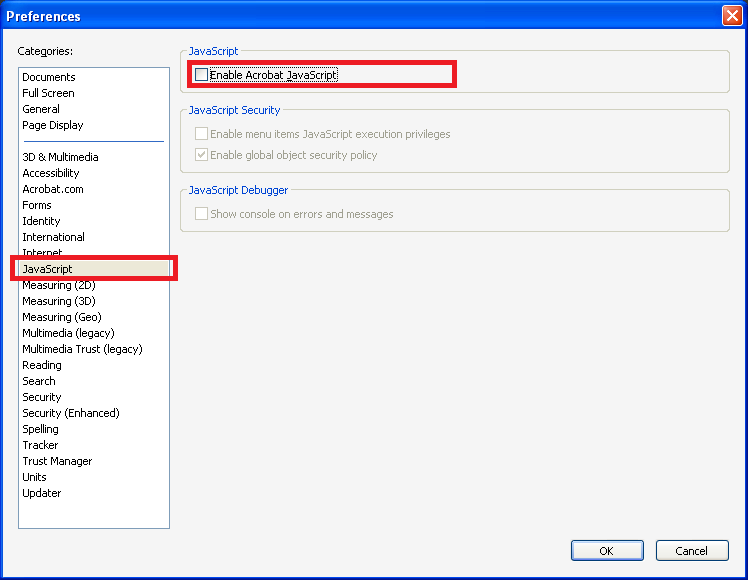
From the Preferences panel, select “JavaScript” and uncheck the “Enable Acrobat JavaScript” option as shown below.
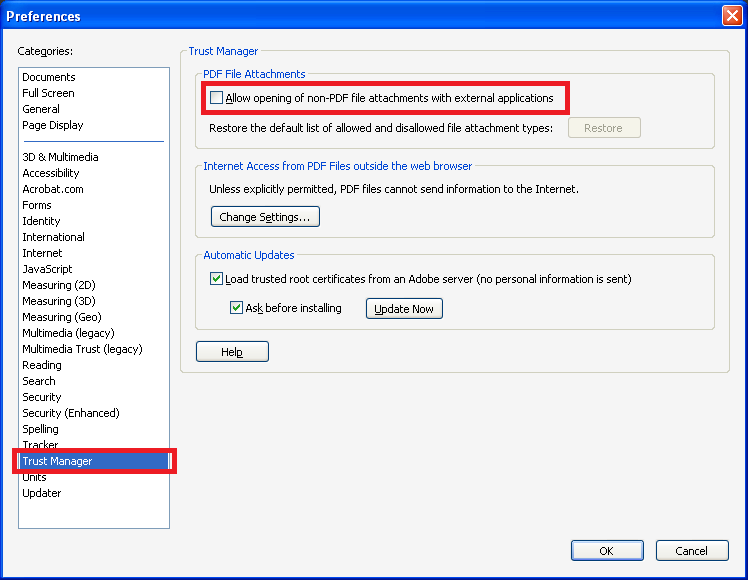
From the Preferences panel, select “Trust Manager” and uncheck the “Allow opening of non-PDF file attachments with external applications” option as shown below.
References:
No Comments, Be The First!