Spear Phishing targets Microsoft to amass large numbers of credentials

We observed a considerable uptick in Phishing Attacks during the COVID-19 pandemic. During our analysis, we came across a Spear Phishing Campaign targeting high-profile individuals for credential harvesting. The emails that we analysed link to fake login pages mimicking Office 365 logins for the victim organizations.
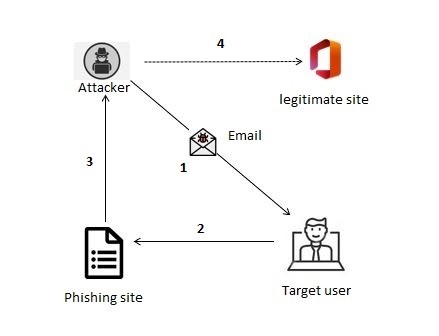
Fig. 1 – Phishing attack flow
Here is the technical analysis of a few of these Spear Phishing emails:
Tax-invoice mail
Instances of malicious emails sent to high-value targets consisting of genuine-looking Tax-invoice(s) marked as confidential were observed in this campaign. This communication includes COVID-19 related information and senders’ details — the latter pretends to be CEO of a bank from an east African country. However, the corresponding domain name is spoofed as the targeted user’s organization’s finance department (blurred in red) in an attempt to make the email appear as legitimate as possible.
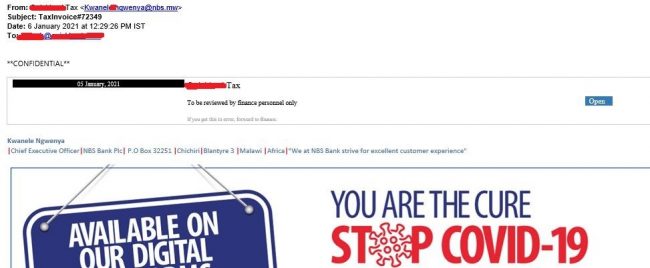
Fig. 2 – Fake Tax Invoice email
In the image above, the domain ‘tld’ in the ‘sent from’ indicates that is related to the African country of Malawi.
A malicious URL is embedded in the call to action in this email as seen below –
https[:]//AAAA[.]israelandamerica[.]com/95125?[base64-encoded-targetID]=&&mic#73747?xxxx=xxxx=
This URL contains the targeted user organization name (AAAA) as sub-string & target victim email ID in base64 encoded format.
When the targeted user clicks on open, it will redirect and land on a fake page with a different URL as shown below. The fake phishing page looks exactly like Microsoft Office’S Login Page. Redirected URL can have targeted user organization’s sub-string to make the user believe about the legitimacy of the website.
Targeted email Id is rendered from embedded URLs as base64 encoded.
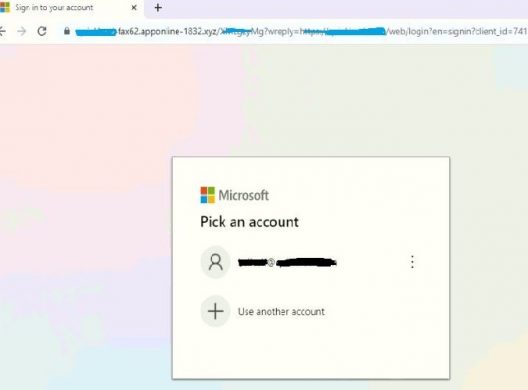
Fig. 3 – Fake Landing Page
In the below image, organizational (blurred) sub-string are present along with the logo of the organization with the target’s email ID.
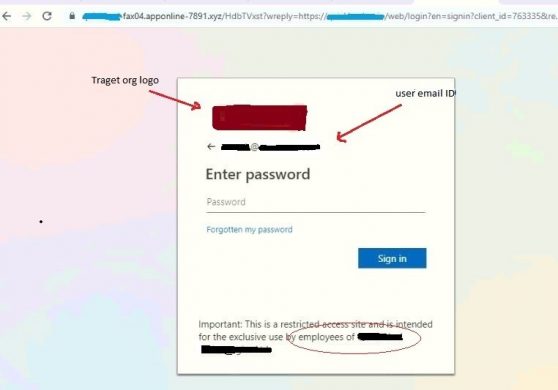
Fig.4 – Password field
To make this look all the more genuine, the attacker also displays an important message for the targeted user.
No matter what password is inputted, this step will always error out tricking the user into clicking ‘reset password’. Once, reset password clicked, It will open a similar login page with a new URL which includes encoded email ID to render.
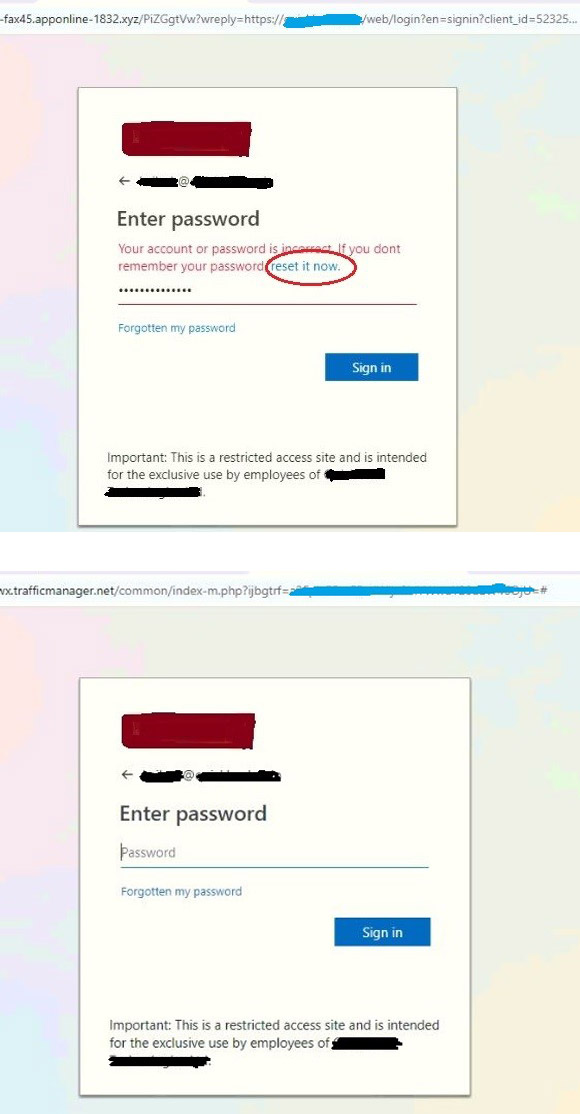
Fig.5 – Password reset page
During traffic analysis, we found that entered password along with email ID is posted to a remote server in background traffic.
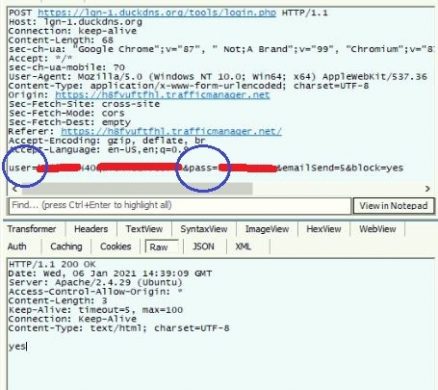
Fig.6 – Posting Credentials to the remote server
Targeted user’s email/password is sent with user/pass parameters in POST request.
TLS certificate for this domain has a short-term validity from 30-Dec-20 to 30-March-21 —IPs 199.19.225.191 & 20.37.247.74 are found & associated with domains during analysis. The domain lifespan was short & it also identified the multiple browser/user agent after some attempts and redirects to normal websites with domain numerical sub string changes in each attempt.
It is also identified that attacker to be targeting top-level officials from various organizations with encoded email Ids which appear like the attacker’s ‘Hitlist’
Phishing email with Voice mail as an attachment
Similar phishing attempt was identified with embedded script in audio message emails as below. In this type of attack, the email contains a Japanese domain, mapped with the target organization’s name which is ‘CALLER’ in this instance.
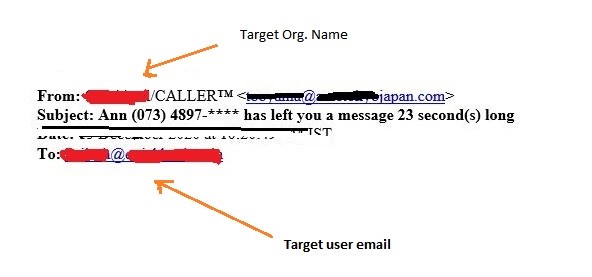
Fig.1 – Email from the attacker
The script embedded in the mail had hex-encoded code with an URL that lands to a phishing site. Hidden parts contain base64 encoded in targeted user email ID.
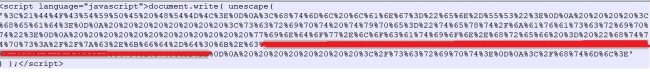
Fig.2 – Hex encoded script
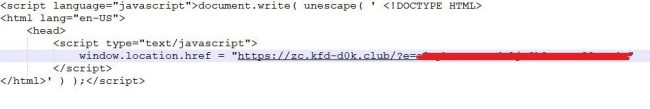
Fig.3 – Decoded script
In the above-decoded script, phishing URL can be seen wherein the parameter “e” contains the base64 encoded value of the target user’s email id. Once the above script is executed, the user gets redirected to a phishing page.
Fig.4- reCaptcha validation
In the image below, we can see a fake Office 365 landing page with the organization’s logo. Email ID of the target user is rendered from encoded script URL parameter value.
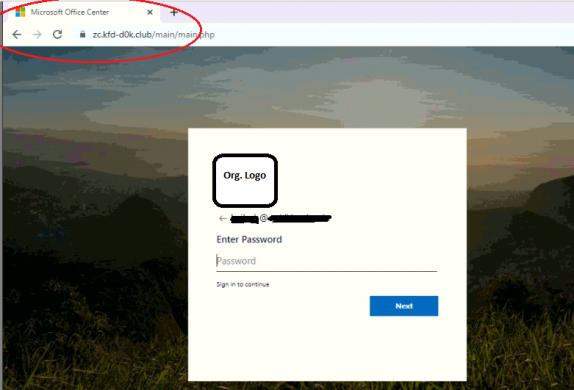
Fig.5 – Fake credential input page
After entering the password, It gives an error for the 1st attempt — it would show validation success message then redirect voice audio clip. The credentials would be posted to a remote server.
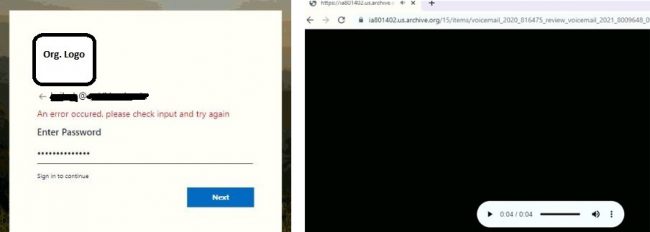
The audio clip is a short mp3 message regarding a request to call. Re-attempt for main kfd-d0k[.]club may lead to normal websites. Subdomains are related to Latin America with a short lifespan and TLS certificates are also valid for a few months.
“To execute spear phishing attacks, malicious vectors would have the list of target email Ids and organizational details. Exploitation attempts can be initiated via emails/IM or any other methods with embedded scripts/URLs. The end goal of attackers is to harvest the credentials of the high-value individuals to disturb the organizations, lead to scams, steal critical information, etc.
Tips to spot phishing attacks
Validate Email Sender details: Validate the sender’s email ID & names to check Impersonation.
Check Subject Line: Check for words like urgency, Important & financial nature in the subject line.
Verify the Links and Attachments: Check legitimacy by hovering over the links, scan the attachments.
Message Content & Email format: Carefully read the nature of the email, intention, check grammatical errors & visual style and verify email signature.
Subject Matter Experts
Prashant Tilekar
Shiv Mohan

No Comments, Be The First!