PowerShell: Living off the land!

Trend of PowerShell based malware is increasing. General trend observed shows that malware authors use new techniques for infection and propagation of malwares along with open source tools. PowerShell gets executed with high privileges and that’s why it easily performs its activity and propagates through network.
Quick Heal Security Lab has observed that some malwares are using file-less techniques. A file-less malware is sometimes considered synonymous with in-memory malware, as both perform their core functionalities without writing data to disk during the lifetime of their operation. File-less malware attacks are typically very difficult to prevent and detect by any AV, as file-less malware are not present on disk.
In many cases we found that, infection vector is through RDP. If password is weak, by using brute force method, attacker can easily get access to machine. Attacker sends a PowerShell script and after execution, it downloads second stage of PowerShell payload which is obfuscated, and it checks whether system is already infected or not. If not, it enters a persistence entry and downloads third stage of payload, which contains different modules embedded in it.
At each stage, obfuscation level and its techniques get more complex.
Following is the image of entry/first level PowerShell script which executes with parameter “-nop” (Does not load the Windows PowerShell profile), “–ep” (Sets the execution policy) and “-e” (Accepts a base-64-encoded string) with Base64 parameter.
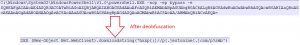 Fig.1: First level PowerShell script
Fig.1: First level PowerShell script
After decoding script, it shows information which requests on URL to download and executes script present on that website. Following is image of second level PowerShell script containing Base64 encoding with Deflate Stream compression.
 Fig. 2: Second level PowerShell script
Fig. 2: Second level PowerShell script
This script has multiple purpose. Basically, it is used to create global mutex, to check whether system is already infected or not and it also creates persistence entry.
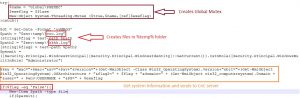 Fig. 3: De-obfuscated Second level PowerShell script
Fig. 3: De-obfuscated Second level PowerShell script
This script creates a Global mutex of name “Global\PSEXEC”. After that, it creates two log files and checks whether those log files are already created or not. If files are already created, then further execution of script gets stopped. If files are not there, it creates two files at “%temp%” location having name “ccc.log” and “kkkk.log”.
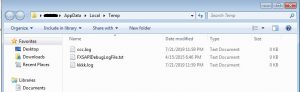 Fig. 4: Log files created at %temp% location
Fig. 4: Log files created at %temp% location
This script also creates a persistence entry in Task Scheduler.
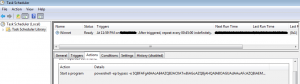 Fig. 5: Task Scheduler entry
Fig. 5: Task Scheduler entry
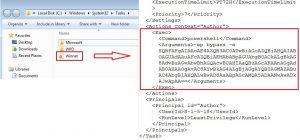 Fig. 6: Task Scheduler entry
Fig. 6: Task Scheduler entry
This entry contains same code which is entered at first level and this will execute after every 45 minutes.
After that, the script will collect system information and send to CnC server:
hxxp[:]//134[.]209[.]103[.]152/updatev1?<system_info>
from which it downloads third stage PowerShell script.
The third level PowerShell script is heavily obfuscated, having size more than 3 MB.
After 3 levels of de-obfuscation, we found that this script uses many open source tools to perform its malicious activity.
In first step, it checks for privilege of running script and according to privilege of PowerShell script, it downloads a PowerShell script and adds its persistence entry into schedule task which triggers after every 45 minutes.
In next step, it executes PowerDump tool which is used to dump the hashes from local system. Using these hashes, PowerShell performs lateral movement.
This script is responsible for dumping credentials using Mimikatz utility. This script embeds two Mimikatz dlls (32 bit and 64 bit) and it loads according to system configuration. The dll is loaded by PowerShell script using reflective dll loading. By getting these hashes, PowerShell will append these hashes to predefined commonly used username and password list.
Following is list of some NTLM hashes.
 Fig. 7: Users Hash
Fig. 7: Users Hash
 Fig. 8: Commonly used password list
Fig. 8: Commonly used password list
Till now, PowerShell script had hashes and using passthehash technique, it tried to get access of another system within network. And hence, to discover network, it uses PingCastle utility. This is basically used to assess quickly Active Directory security level.
After getting network information, using passthehash attack, it tries to create an authentic session within a network. If it gets system access successfully, then using SMBEXEC tools, it creates a task scheduler entry in remote system having name “Sync” which is different from previous file and it also adds new rule in firewall and open port on tcp having port number 65353 in listening state. Task scheduler entry triggers after every 40 minutes.
![]() Fig. 9: “Sync” Task Scheduler entry
Fig. 9: “Sync” Task Scheduler entry
The task scheduler service creates entry in TaskCache which can also be triggered for this scheduler task.
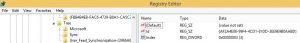 Fig. 10: “Sync” entry in Registry
Fig. 10: “Sync” entry in Registry
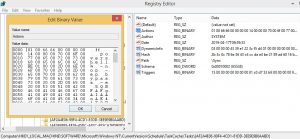 Fig. 11: PowerShell entry in Sync task
Fig. 11: PowerShell entry in Sync task
If passthehash attack gets failed, this script also has SMB exploits in it. It starts to check the SMB version (SMBv1, SMBv2) of system in network and for SMBv1 PowerShell tries to enter in another system using SMB exploit.
After lateral movement, PowerShell goes in infinite loop in which it checks if any Anti-Virus product is installed on system. If found, then that information will be sent to its CnC server.
 Fig. 12: Check for AV products
Fig. 12: Check for AV products
As per activity done by PowerShell, by opening a tcp port on 65353, we suspect that it can be used to perform bot activity in future.
Quick Heal has successfully detected the PowerShell malware by our Behavior based detection.
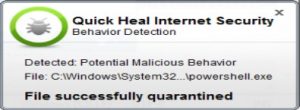 Fig. 13: Behavior Detection
Fig. 13: Behavior Detection
Conclusion
Quick Heal security labs analyze new trends of malware containing number of open source tools with fileless activity. From our analysis only we found that PowerShell is performing all malicious activities and executes payload in memory, spread in network using exploits and along with it opens a listening port on tcp having port number 65353 like a backdoor malware. The malware are still active, so we recommend updating systems and anti-virus product with available patches.
IOCs:
C6C4220DA03351645FADC33F6F985CFC
500A3B178AF4D066A88A27EDF1A278C0
Subject Matter Expert:
Aniruddha Dolas, Nagesh Lathkar
No Comments, Be The First!