Potentially Unwanted Application (PUA) – A Digital Nuisance

This post aims to provide an insight to our readers about programs called Potentially Unwanted Applications, about what they are and how they can be a threat to our privacy and security.
What are Potentially Unwanted Applications?
Potentially Unwanted Applications (PUA) are often bundled with genuine software that are freely available online and are usually sourced from shady, less popular or untrustworthy websites. PUAs mainly include spyware, adware, downloaders, etc. They are called so because they are often downloaded by the user erroneously or without making a conscious decision. This occurs mostly in cases where the user fails to read the software download agreement.
Why are Potentially Unwanted Applications unwanted?
PUAs are not necessarily harmful but their activities are considered so and may pose a threat to user privacy. Most of them are known to perform one or more of the following activities.
- Tracking user’s location
- Collecting user’s personal data and selling it to a third party
- Displaying ads based on the browsing habits of user
- Modifying browser settings like default search engine, home page, etc.
- Adds extensions to browser which modifies the browser settings
- Downloads malicious files from unknown and untrustworthy websites
- Misuse social networking sites data for user analysis
- Force user to complete survey which collects user’s personal information
How do PUAs infiltrate your computer?
PUAs ‘get’ installed in system when a user fails to ignore them while downloading various software from untrusted websites. Below are listed the various scenarios where a PUA can gain entry into a computer.
1. Default options asking to install toolbar or extensions
The user visits various websites to download free software, screensavers, games, etc. All such freeware are usually bunched with multiple third party software. Sometimes, they provide ‘Downloader’ which downloads intended files along with other software. Below are some examples.
Scenario 1
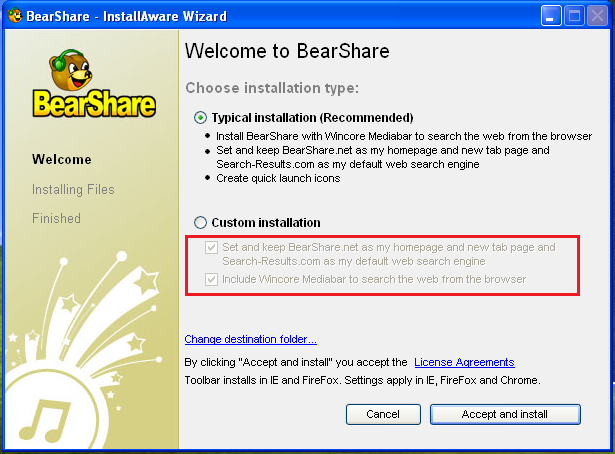
Selecting the “Recommended” option during installing a free software, unwanted third party applications are installed by default. Figure 1 shows the installation of a PUA called BearShare. Once installed in the computer, it sets Bearshare.net as the default home page and adds Wincore Mediabar to the browser. And all this is done without the user consent. This PUA belongs to the BrowserModifier.KipodToolsCby family.
Scenario 2
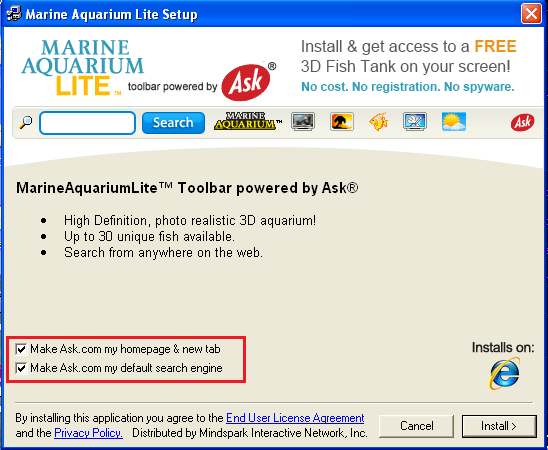
In another scenario, as shown by Figure 2, two check boxes are pre-selected to set the default homepage and search engine to ask.com. This PUA belongs to the PUA.Mindsparki.Gen family.
2. Disguised as download links
Cyber criminals take advantage of ads shown on websites by displaying several fake download options. An unsuspecting user is most likely to click on such fake ads and this results in the installation of PUAs on their computer. Below are some examples.
Scenario 1
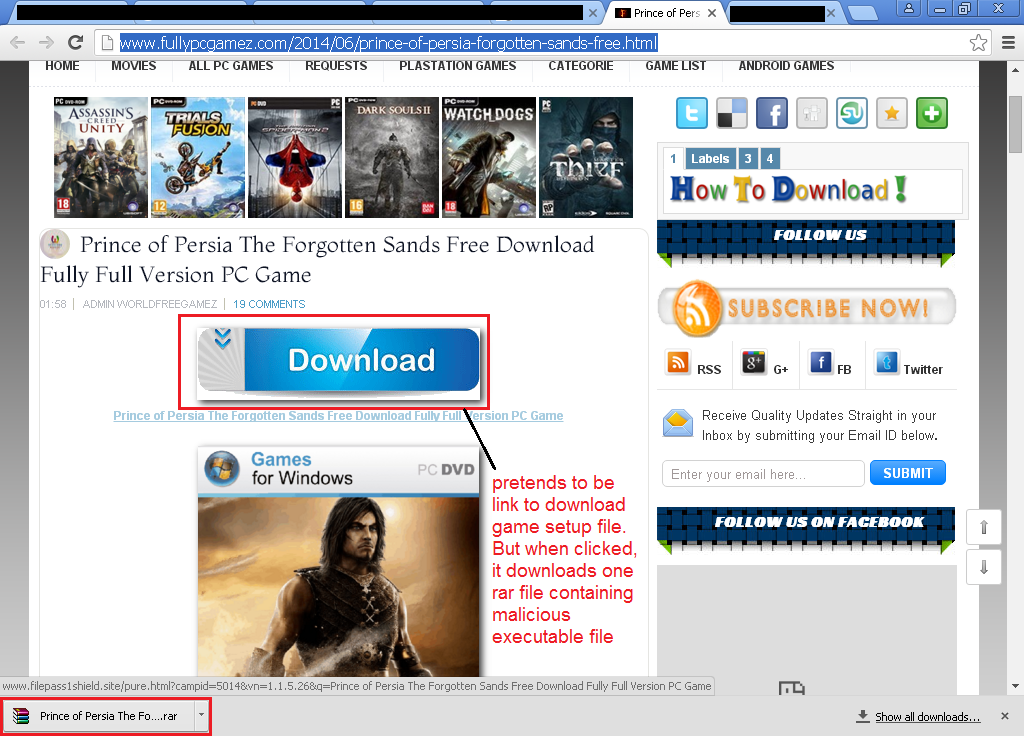
The ‘Download’ link highlighted below masks itself as an actual link to download a game. But, when the user clicks on it, a compressed executable file containing PUAs gets downloaded on the computer.
Scenario 2
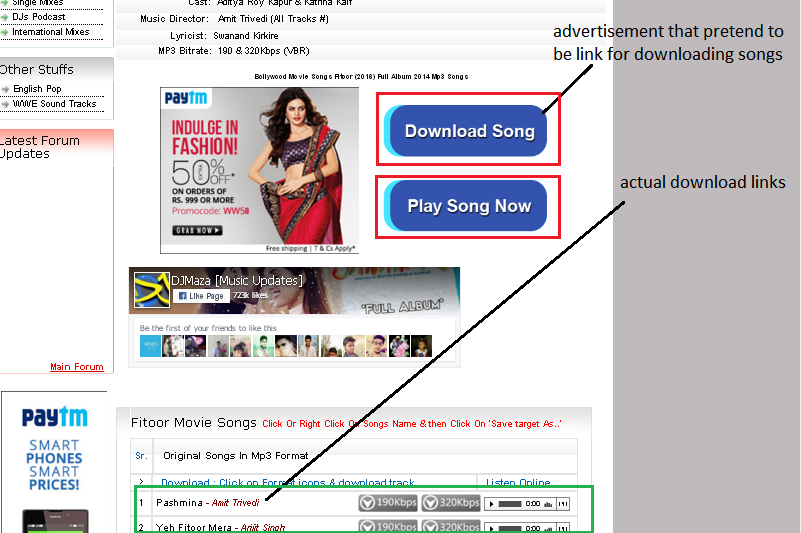
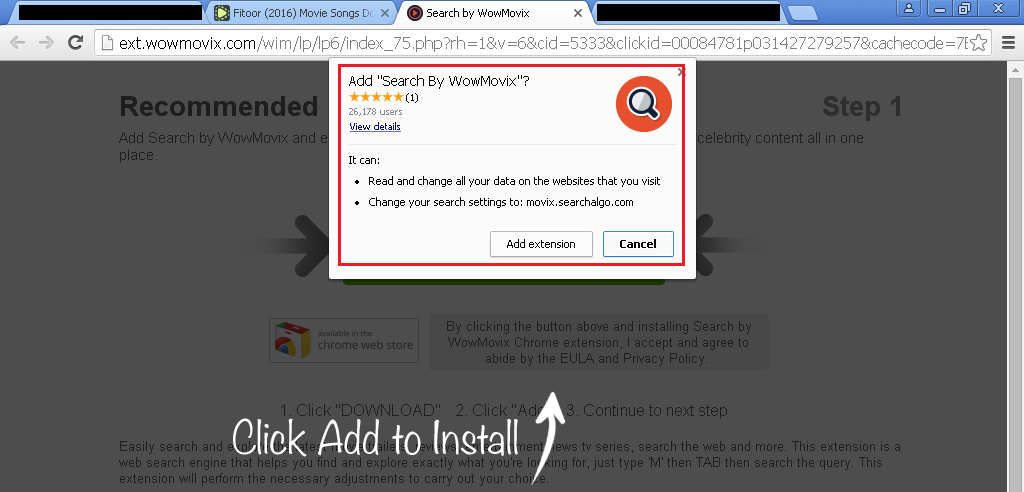
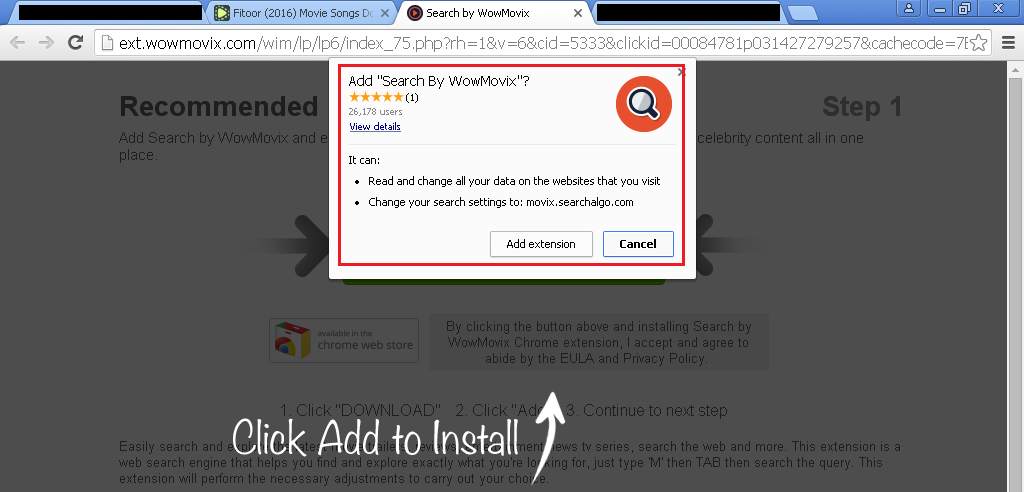
In another scenario, similar to the above one, when a user searches for downloading free MP3 songs, the site displays multiple ads that appear as actual download links that confuse the user.
When the user clicks on the fake download button, they get redirected to another site, which prompts them to download a PUA. If the user proceeds further and clicks on the download link, the browser shows a prompt to add a browser extension which ultimately modifies the browser settings.
3. Executable files downloaded instead of the intended media file
In some cases, users download PUAs instead of what they intended to, such as a movie or a song. While the user is under the impression they have downloaded a file with extensions .MP3, .MP4, .FLV, .WAV etc., they actually end up downloading a .EXE (executable) file.
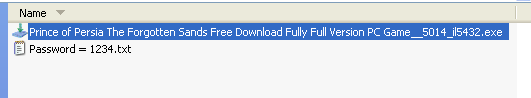
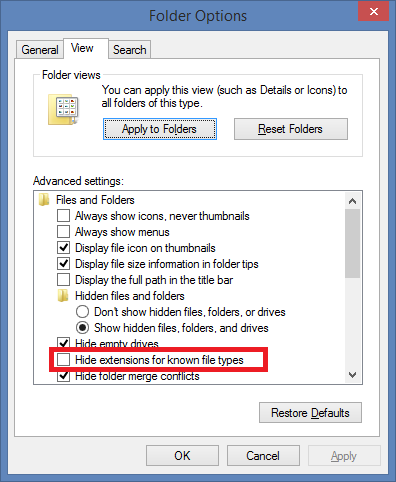
If the ‘Hide extension of known file types’ option is selected, then the executable file may appear as a media file as shown in figure 6.
On the other hand, if this option is unchecked, then the file shows up as an executable instead of a movie file (Figure 7).
In another example, the user intends to download a game setup but instead, ends up downloading an executable file of a smaller size.
Clicking on the file then installs other unwanted software.
4. Taking advantage of users’ neglect towards the Privacy Policy and License Agreement
Each software is bound by an End User License Agreement (EULA) – an agreement between the software publisher and user of the software,. The agreement establishes the user’s right to the use of software. In most cases, users ignore to read the agreement thoroughly and proceeds to the installation of the software. EULAs are lengthy documents and that is what deters users from reading it. Taking advantage of this, software publishers add unusual clauses to agreements which clearly specify the security risks involved in installing a particular software. And this makes the user solely responsible for any drawbacks of using the software. Below is an example that explains this scenario.
Scenario 1
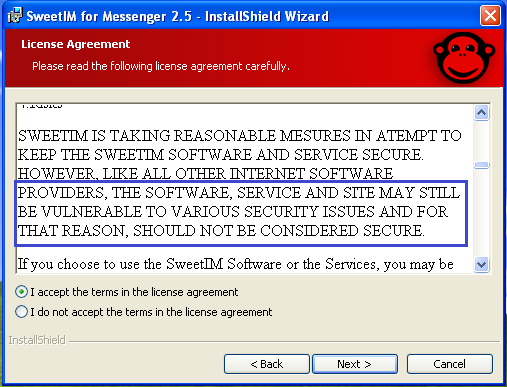
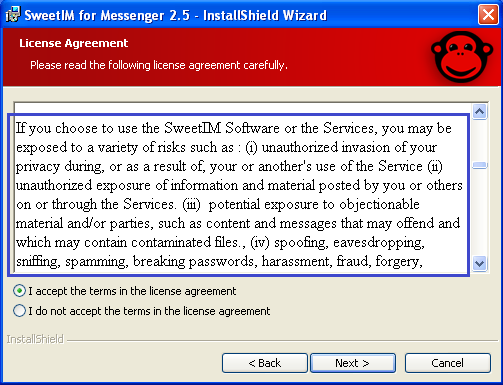
The below License Agreement clearly states that the software is vulnerable to security risks and should not be considered secure. It further mentions issues about privacy and potential exposure to malicious attacks like spoofing, spamming, breaking passwords, harassment, forgery, etc.
Unwanted activities of PUAs
Following are various examples of activities performed by various PUAs.
Scenario 1
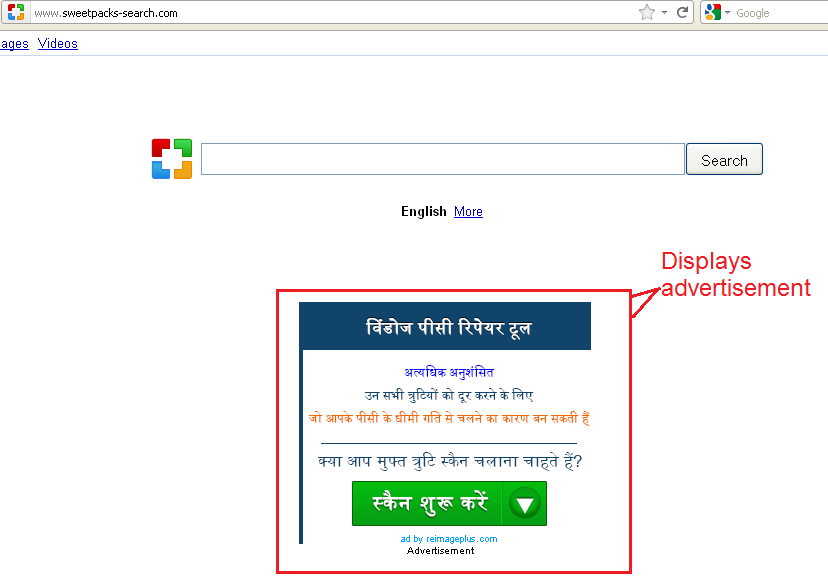
A PUA modifies the default home page to home.search.com which gets redirected to sweetpacks-search.com. The site shows unwanted ads, clicking on which triggers the download of another rogue application.
Scenario 2
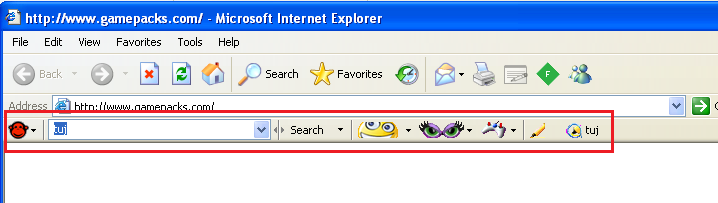
A PUA adds a toolbar to the browser to provide emoticons (smileys) for Instant Messaging applications
Scenario 3
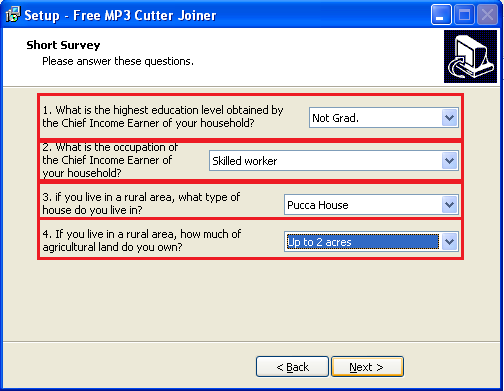
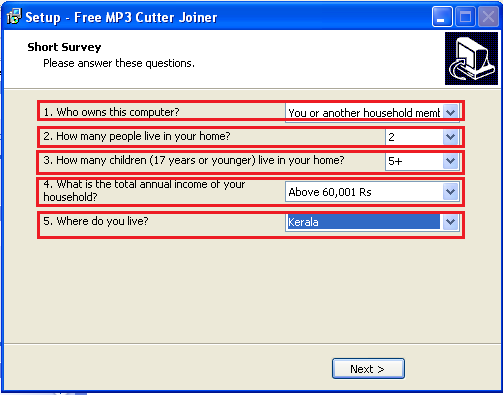
Before letting the user install the “MP3 cutter and joiner” application, the PUA asks for personal information related to income, education, and other irrelevant data. This information could be sold in online black market for malicious purpose.
Scenario 4
A PUA adds an extension to the browser to monitor its activity. This occurs when the user clicks on a fake download link intending to download a song or a video from a website.
Detection Statistics
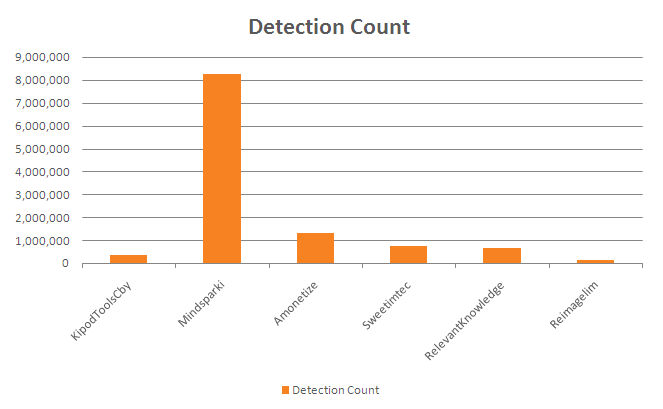
Figure 16 represents the Quick Heal detection statistics for some of the interesting PUAs discussed above, from January 2015 to January 2016.
Preventive Measures
1. While downloading applications or files from untrustworthy and unknown websites, verify whether the downloaded application installs what you had intended to.
2. Read and understand the privacy policy and risks involved in downloading any software.
3. Be careful while clicking on download links.
Read all browser extension permissions carefully. If they seek any unwanted or suspicious permissions, avoid them. Below is list of permissions that you need to be careful of:
- Access to all data on your computer and the websites that you visit
- Access to read, request or modify data from every page you visit
- Access to browsing history and your physical location
4. Never respond to online surveys that ask for personal or financial information.
5. Verify file extensions after downloading to avoid running executables assuming that they are a media file. Disable “Hide extensions for known file types” option in Tools menu > Folder Option > View Tab from Explorer.
Quick Heal’s Antimalware mechanism detects and cleans most PUAs. To start an AntiMalware scan on your PC, right click on Quick Heal Antivirus icon in the quick launch tray and select “Launch Antimalware”. Click on “Scan Now” to start scanning.
ACKNOWLEDGMENT
Subject Matter Experts:
- Tejas Girme
- Bharat Kale
– Threat Research and Response Team.


3 Comments
Great article and amazingly simple language…!
Wow nice article regarding the PUA. Note to keep in mind while regarding installation of softwares…..
Yes its really Nuisance.