Ouroboros: Following A New Trend In Ransomware League

Ransomware authors keep exploring new ways to test their strengths against various malware evasion techniques. The ransomware known as “Ouroboros” is intensifying its footprint in the field by bringing more and more advancements in its behavior as it updates its version. This analysis provides the behaviour of version 6, few earlier variants of it and some insights on the recent Version 7. This Ransomware not only applies conventional methods but also adopts some new techniques making it very difficult to analyze.
Infection Vector
Ouroboros has been around from a year now and it spreads through RDP Bruteforce attacks, deceptive downloads, and through Server Message Block (SMB), which is generally used for file sharing and some administrative tasks on Windows endpoints connected over a network.
Technical Analysis
During analysis, we found that initially, it stops SQL process ( SQLWriter, SQLBrowser, MSSQLSERVER, MSSQL$CONTOSO1, MSDTC, SQLSERVERAGENT, MySQL etc ) in order to encrypt those files which are open in a database by creating process cmd.exe with “net stop” command as shown in fig below.
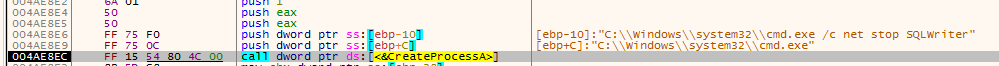
Fig.1 Code snippet for stopping SQL process through cmd
It also stops some other sql process like sqlserver.exe, sqlagent.exe etc but uses another method to terminate.
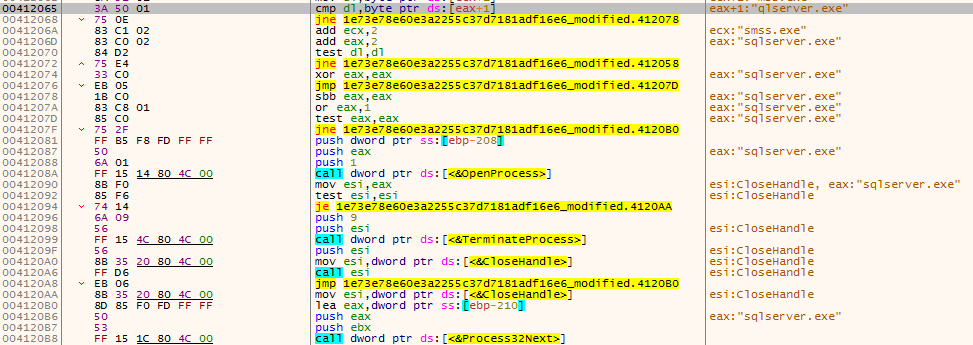
Fig.2 Adopting different method to stop other SQL processes
Resemblance To LockerGoga
It forms 0x40 bytes key stack consisting of 0x20 key bytes generated from CryptGenKey Crypto API and combines it with 0x20 bytes which are already present in the file. Then it performs AES operations on them similar to LockerGoga. Ouroboros and LockerGoga use crypto++ library which makes the analysis difficult. While steps for encrypting the data is same, both use different encryption modes. LockerGoga uses AES in CTR mode, while Ouroboros uses AES in CFB mode.
Both the samples are using aesenc/aesenclast instructions, which are part of the AES-NI Instruction Set introduced by Intel around 2009.
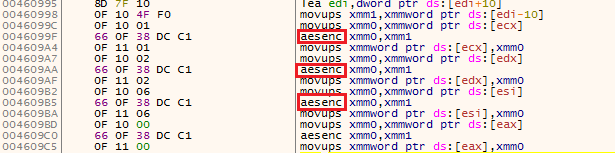
Fig.3 Instruction set used by malware
Encryption Procedure
As explained above, after making 0x40 bytes key stack, it expands the key using Rijndael key expansion from 0x20 (256 bit) to 240 bytes by performing 15 rounds of various mathematical expressions.
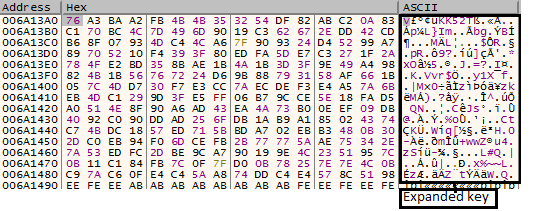
Fig.4 Expanded key Using Rijndael Expansion
It builds initial block cipher using the instruction set shown in (fig.3) by using expanded key and IV.
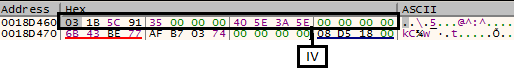
Fig.5 Initialization Vector
After forming the initial block cipher of 0x40 bytes, it is used to encrypt file data by reading bytes from a file and performing operations on them. These encrypted bytes are stored in memory and then copied to file by using WriteFile API.
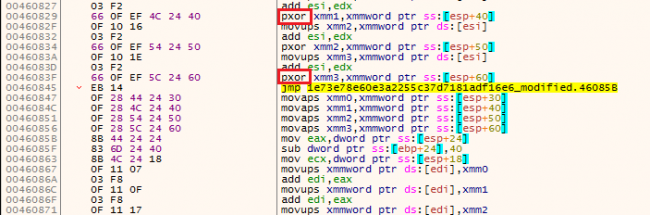
Fig.6 XORing block cipher bytes with file bytes and storing them
This ransomware keeps 0x100 bytes PEM encoded RSA public key in a file. It encrypts AES key with this RSA public key and appends it at the end of the file as shown in (Fig.7).
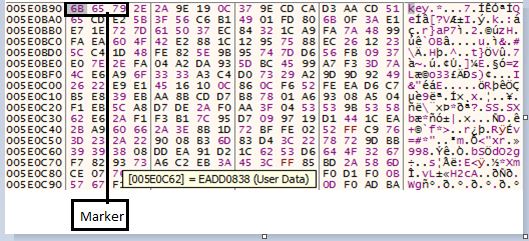
Fig.7 Appending key at the end of file
Ransom Note
On host machine, files are encrypted with extension [original file name].Email= [*.com]ID=[XXXXXXXXX].odveta
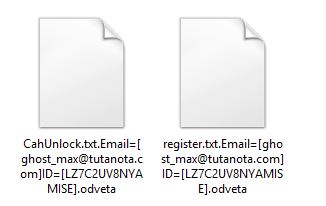
Fig.8 Extension Format
After encryption, it drops Unlock-Files.txt in each folder as a ransom note.
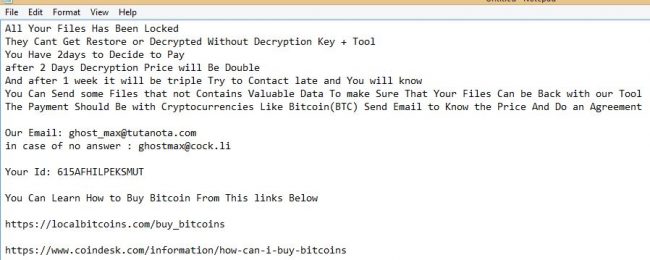
Fig.9 Ransom note
Network Analysis
Before connecting to CnC server, it performs DNS query on sfml-dev.org and makes HTTP Get Request to url /ip-provider.php and receive victim’s host/system public IP in response as shown in below figures.
Fig.10 DNS query to get the public address of sfml
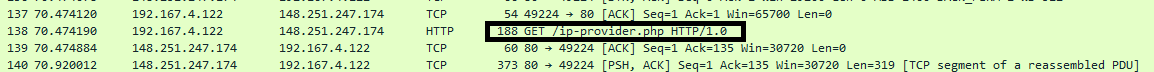
Fig.11 Query to get public of host
It then initiates a connection to CnC (IP: 92.222.149.118) over port 18 but may not connect due to a closed port.
“There was no response from the server when we tried to connect via telnet over port number 18, but as we were trying to connect over other ports, it gave successful response for port number 22 (SSH) .”
The network connection happens before encryption starts and in earlier versions, it was not clear what malware intends to achieve. But in version 7, we have observed that after a successful connection to CnC (though IP address is different), it sends locally generated RSA private key over CnC which might be the case of version 6.
Evoloution of Ouroboros
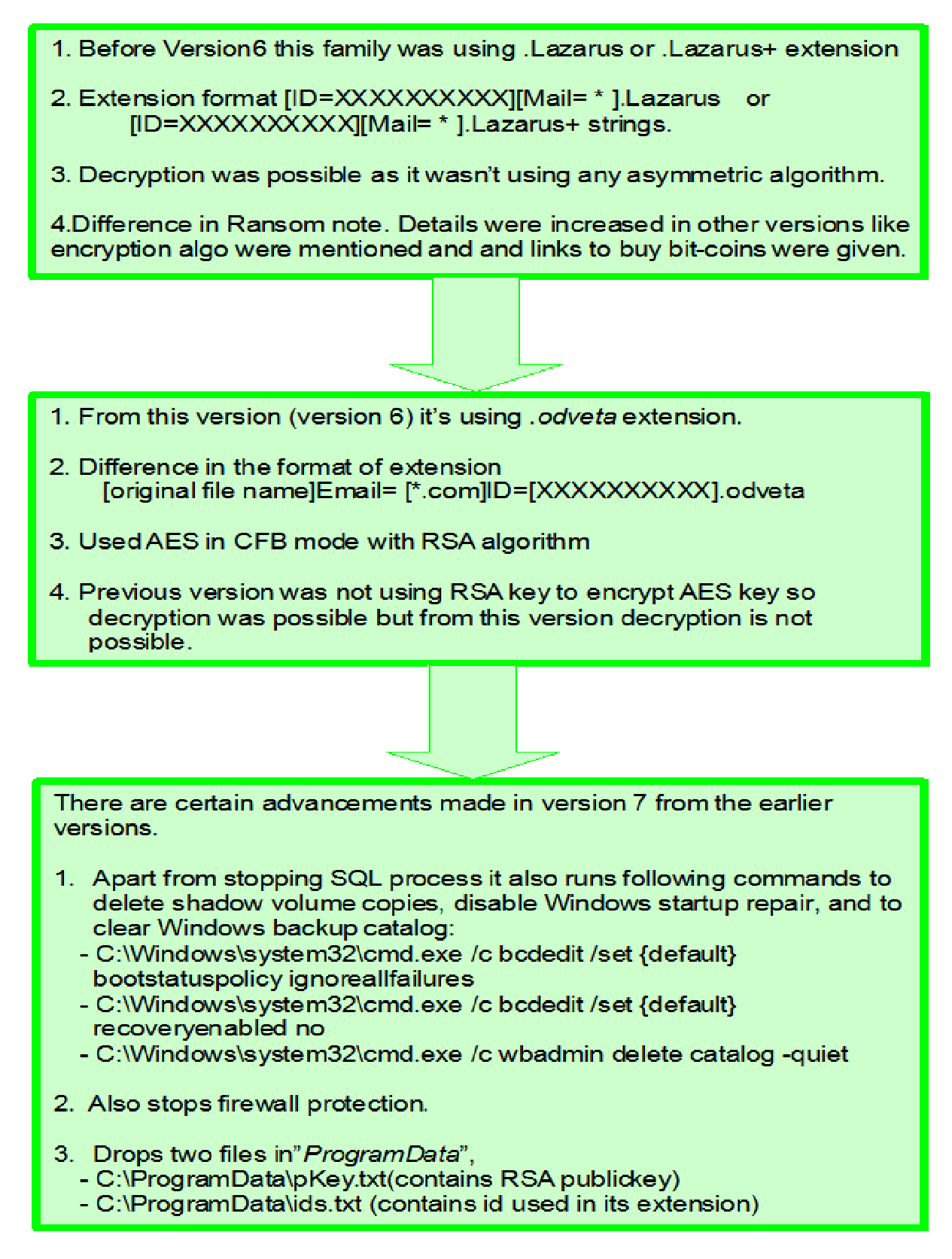
Analysis of Ouroboros version 7
In this version, CnC ( 80.82.69.52 ) was live , so we were able to perform network analysis.
Before it establishes the connection, it checks for ids.txt, if it is already present in ProgramData then it skips the connection and does the encryption with an offline key.
But if ids.txt is not present, it connects with CnC and resolves the public address of the host, same as in version 6.
After resolving public address of the host, it generates RSA key, not using any kind of library for its generation but it has implemented the whole algorithm and has locally generated the public and private key.
Following is the part where the key gets generated.
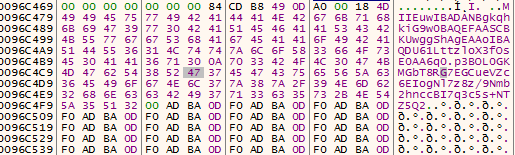
Fig.12 Private key locally generated
After forming a private key, it sends the same to CnC and gives the response as “Active”.
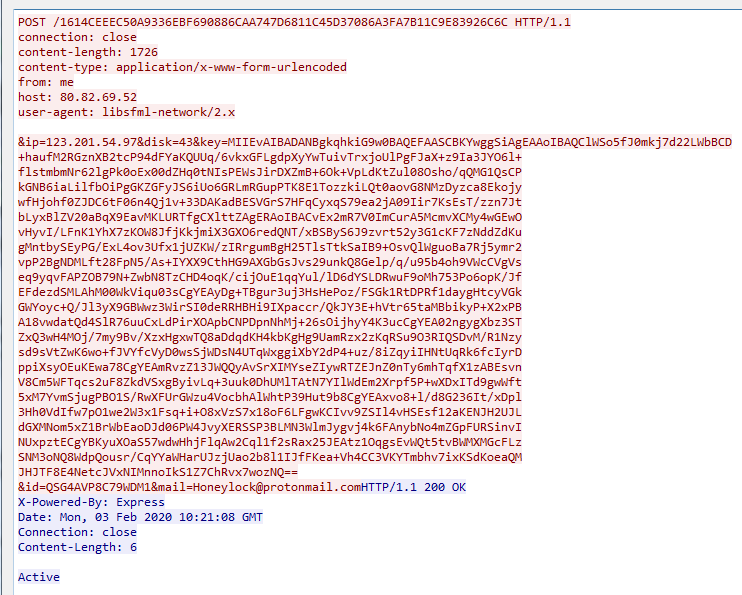
Fig.13 Private key send over CnC
Ransom Note in Version 7
After encryption, it drops info.txt and uiapp.exe in C:\ProgramData and deletes the pKey.exe.Uiapp.exe is the .Net file is created in order to drop the ransom note.
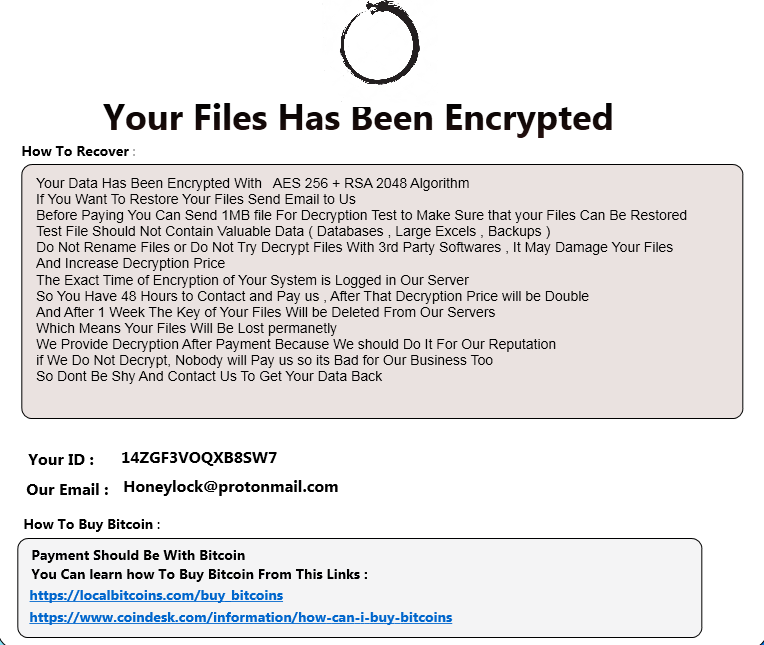
Fig.14 Ransom note Version 7
Quick Heal provides multilevel protection for this family. It detects and deletes it in real-time scenario as well as in behaviour base detection and ARW module.
Conclusion
Ransomwares are now not only using packers but also using libraries as well as different instruction set to make the analysis difficult. And noticing that other ransomwares (LockerGoga) have also used similar techniques, we can say that this trend will be followed in the future.
IOCs
Version6:
1E73E78E60E3A2255C37D7181ADF16E6
1EA66E610493B9DB3F5AA6DA82CA2CE7
560EE81F4250138CE063FEC3F387690C
B316DB79241100B0E86C11352DD169A0
6330639300E22E956CC50CCBD4FD027E
Version7:
117C3707F4D8DB004A0E7EF86350612B
15F32A4EE7B75AEFA308866B4BD79539
Subject Matter Expert
Manisha Prajapati, Pooja Birajdar | Quick Heal Security Labs


No Comments, Be The First!