LinkedIn Phishing Scam: Hackers target users with fake job offers

LinkedIn is a popular social networking platform that is focused on professional networking and the business community. On this platform, users are focused almost entirely on making connections and finding jobs. But things are not always as they seem. Of late, LinkedIn is emerging as one of the most popular social networking sites used by attackers for phishing attacks.
In one of the recent alleged breaches at LinkedIn, attackers claimed that “Scraped data of 500 million LinkedIn users being sold online, 2 million records leaked as proof”. In this data breach LinkedIn profiles, user IDs, email addresses, phone numbers, professional titles, job-related descriptions data were leaked. It is suspected that attackers use this data and harvest user credentials and other personal information with phishing attacks and more. Although the official statement from LinkedIn on this data is that “This was not a LinkedIn data breach, and no private member account data from LinkedIn was included in what we’ve been able to review.”
While analysing such LinkedIn messages or emails, we observed that attackers are spear-phishing the victims with tiny or shorten URLs using the job description or details listed on the target’s LinkedIn profile. When the unsuspecting victim clicks on the URL, the victim is redirected to phishing links and then to a fake Microsoft 0-365 login to harvest the credentials. In some cases, attacks have used links that download banking malware or backdoors on the victim’s machine.
Detailed flow diagram
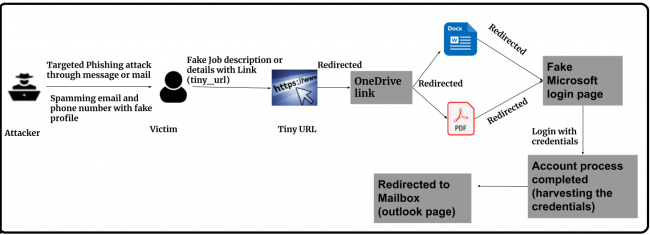
Fig 1. Flow Diagram
Sample Spam LinkedIn Message
Here is a sample LinkedIn message, which looks like a job offering message with a malicious link.
“Hi there, I hope you are doing well! We have a personal project from a client I am presently taking on. It is still in the initial stages of follow-up. From your profile, we see your competencies could be useful. Kindly access this proposal via the link below and advice. (tinyurl[.]com[/]ndependentConsultantInTelecom) We look forward to your prompt and positive response. Kind Regards, Independent Consultant in Telecom and IT Services Industry”
While analyzing URL “tinyurl[.]com/LeaderatCiscoSystems” redirected to a hardcoded one-drive link ->
25AEBC3DBC26A975%21120&parId=25AEBC3DBC26A975%21119&o=OneUp”
This link is then downloaded as a PDF file.
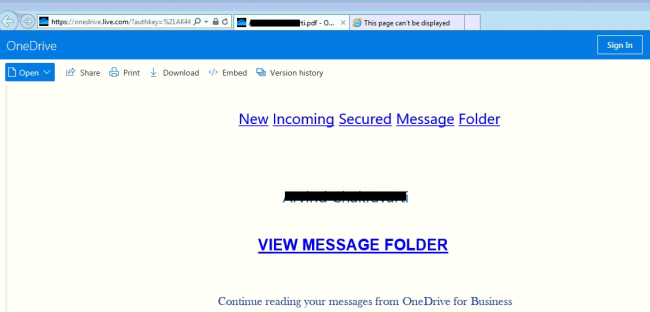
Fig 2. PDF file
Once we open the PDF file, it shows “view message folder” as a clickable link. Upon click, it redirects to
https[:]//motemoat[.]net/proposal/owa/index.php, which further redirects to a long URL as given below:
6+wpkp&90w&=a~a=&+$p0.php?login=&.verify?service=mail&data:text/html;js6/main.jsp?sid=CAgbePXXjcVpfthPNgXXCcgDQZImqqTE&df=webmail126#module=welcome.WelcomeModule
%7C%7B%7D=default<mplcache=2&emr=1&osid=1#identifier”
The above URL shows a fake Microsoft login page as below –
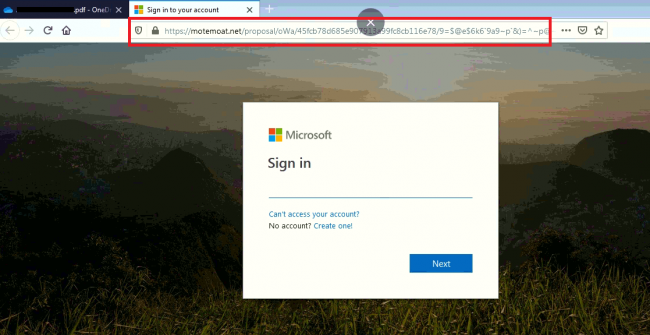
Fig 3. Fake Microsoft Login Page
After adding credentials the first time, it shows an incorrect account or password.
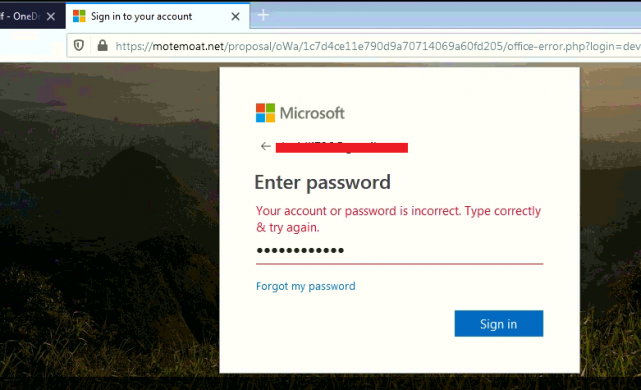
Fig 4– Showing incorrect account or password.
After adding again, it shows the message “Your account process is completed,” here we can suspect that account credentials information gathering activity happens.
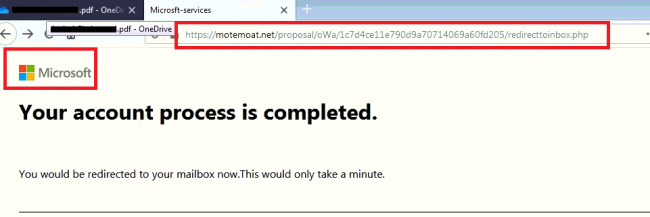
Fig. 5 – Account Completed
Further, this redirected to the legitimate outlook page.
The same PDF file has one more URL, which is the hyperlink to the word “Message” “https[:]//good354la354dsaporrpe.org/proposal/oWa/index.php”.
Another URL we analyzed “tinyurl[.]com/ndependentConsultantInTelecom” This URL to redirects to a one drive link.
parId=25AEBC3DBC26A975%21123&o=OneUp”
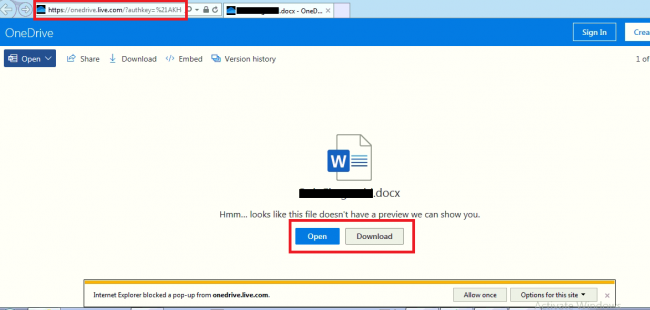
Fig. 6 – Document File
This link is also alive and downloads a doc file.
Once the DOCX. the file is opened, it shows a link with the text “view message folder”. This link redirects to
https[:]//motemoat[.]net/proposal/owa/index.php.
On more URLs is a hyperlink to the word “Message” “https[:]//good354la354dsaporrpe.org/proposal/oWa/index.php”.
This URL is also down as of now. It’s the same as the one found in the earlier PDF file variant.
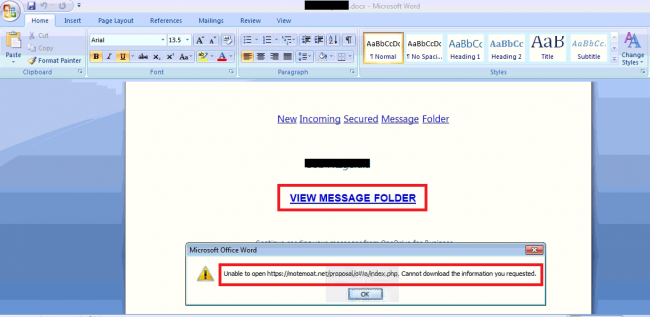
Fig.7 – Embedded link on the text
About the URLs and their respective domains
1. “https[:]//motemoat[.]net/proposal/oWa/index.php”
- I.P:162.241.71.191
- Domain Name: MOTEMOAT.NET
- Admin City: Scottsdale
- Admin Country: US
- Admin Email: 77a661c69ce7e338s@domainsbyproxy.com
- Admin State/Province: Arizona
- Creation Date: 2015-03-01T20:05:14Z
- Updated Date: 2021-03-02T08:14:32Z
- Name Server: NS39.DOMAINCONTROL.COM
- Registrant Country: US
2. “https[:]//good354la354dsaporrpe[.]org/proposal/oWa/index.php”
- I.P :162.241.71.191 (same as above domain)
- Domain Name: GOOD354LA354DSAPORRPE.ORG
- Creation Date: 2021-04-30T01:56:00Z
- Updated Date: 2021-05-04T08:44:08Z
- Name Server: NS01.ONE.COM
- Registrant Country: GB
- Registrar URL: http://www.ascio.com
- Registrar: Ascio Technologies, Inc. Danmark – Filial af Ascio technologies, Inc. USA
Tips to spot phishing attempts
- Verify the Message or sender’s account details, email IDs, name, etc., as possibly some known LinkedIn connection’s account, may have been hacked or credentials stolen and account misused.
- Be aware of fake 0-365 links as it is used for credentials harvesting. Always check the URLs/domain in the links and the page. If it looks mismatched with the original, avoid visiting and putting any credentials on such phishing pages.
- Scan attachment files coming through the message or email even if it is coming from a trusted user.
- Any open document shared on LinkedIn should never ask for 0365 or mail credentials as both have no relation.
- Even if the scam and phishing emails don’t ask you to avoid getting suspected immediately, they may still try to target the legitimate LinkedIn users’ credentials harvesting.
- Message Content & Email format: Carefully read the nature of the email, intention, check grammatical errors & visual style, and verify email signature.
- The most recent LinkedIn-themed spam campaigns may differ, but their purpose remains the same, so keep your account secure with a strong password.

No Comments, Be The First!