Infostealer Campaign detected in the wild

Quick Heal Threat Research Lab has recently observed an active cybercrime campaign designed to steal user info. The campaign has been noticed to make use of three keyloggers (malicious software that records information entered by a user on their computer keyboard) iSpy logger, Predator logger and Knight Logger. These software are easily available on the Internet and can be used for keylogging, stealing passwords and capturing screenshots.
In May 2016, Quick Heal detected an attack related to this campaign, on the computers of multiple users. The attack uses spear phishing emails with attachments of malicious Microsoft Office documents (RTF). These documents are loaded with codes that exploit the CVE-RTF-2012-0158 vulnerability. When the receiver opens any of these RTF documents, a keylogger component is dropped on the computer, which then does rest of the job.
Infection Vector
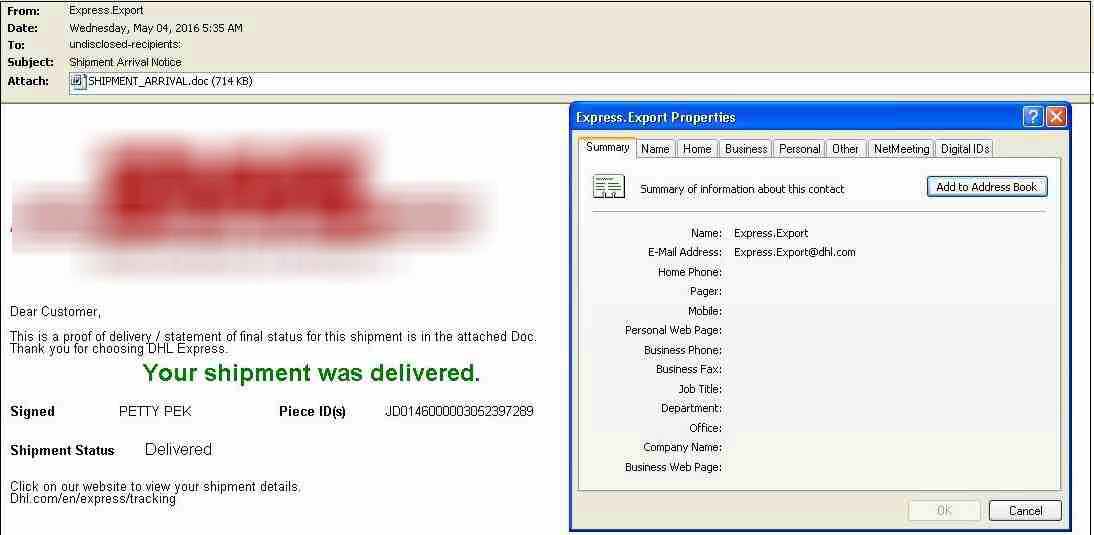
The user receives an email about the arrival of a shipment. The email carries a malicious attachment containing the code to exploit the CVE-RTF-2012-0158 vulnerability. Once the document is opened, one of the software (iSpy, Predator, Knight Logger) is dropped on the victim’s computer.
Below is what the email looks like.
Download this PDF to read the full report
Security measures to take
- Avoid clicking on links or downloading attachments in emails sent from unwanted, unexpected or unknown sources.
- Update your Operating system, and programs like Microsoft Office, Adobe Reader, Java, etc.
- Avoid saving passwords for email clients, online accounts in browsers and FTP servers.
ACKNOWLEDGEMENT
Subject Matter Expert
• Sagar Daundkar (Threat Research & Response Team, Quick Heal)


No Comments, Be The First!