How does a hacker crack encrypted password databases?
We recently published a post about the inherent dangers of passwords and how they are increasingly vulnerable thanks to user negligence. With so much data being safeguarded by elemental passwords, the need for a refined security layer is imperative. However, a common question we received was about how attackers actually store and share compromised passwords with each other.
Understanding ‘Salting’ and ‘Hashing’ encryption
Before we go any further, we need to understand the significance of ‘salting‘ and ‘hashing‘ techniques used by web service providers. These methods encrypt passwords and they prevent the bad guys from getting their hands on large databases of stored passwords. If these databases are recklessly stored in plain text, they become highly vulnerable and visible.
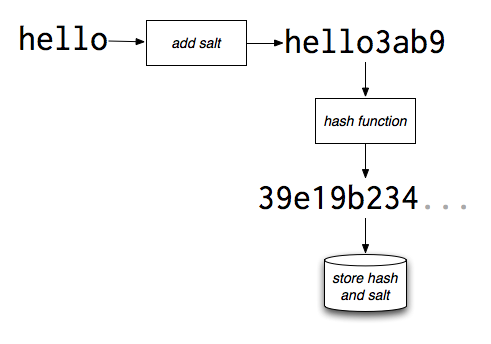
This ensures that even if an attacker gets his hands on databases, he will be unable to crack the code without considerable effort. Salting refers to the process of adding a string of characters to a password. For instance, a password like ‘hello‘ becomes ‘hello3ab9‘ after the process. Hashing refers to the process of encrypting the salted password with a key. So ‘hello3ab9‘ becomes ‘39e19b234…‘ after hashing. Providers use popular programs like MD5, SHA-1, SHA-256, SHA-384 and SHA-512 to carry out this encryption.
Methods to crack stolen passwords
Unfortunately, attackers now have their hands on these programs. As a result, hackers who have cracked certain hashes and navigated around system protection software, share the results with each other over underground forums. Here are the common tools that are utilized and shared by attackers to crack our secure passwords.
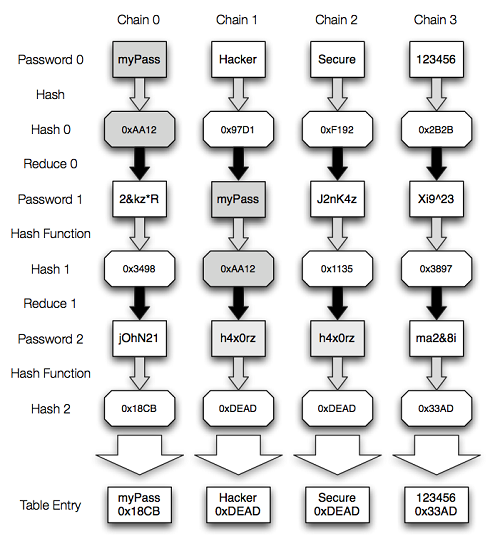
- Rainbow Table
These are tabular databases that contain hashed passwords that have been cracked. Every encryption program is targeted and the results are then shared in a “you-help-me-I-help-you” manner. Subsequently, if a hashed password is obtained by a hacker he simply runs it against the rainbow tables to see if the plain text password can be derived. This process takes him a few seconds if he has multiple tables at his disposal. His results are then recorded in the table and then shared with other hackers to complete the chain. - Dictionary Attack
In this scenario, an attacker runs an encrypted password against an existing set of words. In most cases, this list is simply derived from a dictionary. Many people use day-to-day dictionary words as their passwords and attackers are well aware of this. All they do is run the password against a list of all dictionary words and if the password is in fact a simple word, it will be cracked. This is why it is recommended that you use a combination of letters, numbers and special characters for your password. - Brute-Force Attack
Also known as an ‘exhaustive key search’, this attack is the most comprehensive and detailed trick used by hackers. They scan an encrypted password against all possible combinations including alphabets, numbers and special characters. This process is extremely lengthy so only the most dedicated and persistent attackers make use of it. But if an attacker adopts a brute-force technique then he is guaranteed to crack a password sooner or later. In order to discourage attackers from making use of this technique, it is recommended that you create passwords that are at least 8-10 characters long.
Hackers use these primary techniques, and other lesser known ones, to crack passwords once they obtain a list. After a password has been cracked, they update the list and share it with other hackers to spread the information. Password security is something that a lot of us take lightly so it is important to follow 3 rules – keep it long, use special characters and use different passwords for multiple accounts. Attackers share their resources and results with each other so we should also do the same and contribute towards raising awareness.

12 Comments
Very useful information. What I have observed that generally most of the people do not pay much attention while creating the password even though they are repeatedly warned and advised to follow minimum requirements.
clever
Good article. Well expressed.
Little curious what hackers (EXCALTY GET) from hacking & cracking website and Pwds.
some new method to secur password like encripting before using personal user.
which means even the user don,t know original input password.
then cracking it will be tedious job. trysome thing like this software.to gaurg password
Very educative and noted to use different password for multiple accounts.
Question is how to remember so many passwords unless they are noted. But I understand this is not desirable so what is solution please?
Hi Dhiren,
One option is to use an online password generator. These services provide various passwords that are hard to crack. On the other hand, you will need to at least remember the master password for the service.
Regards.
where is phishing :/ …… Its a good method too and effective a normal laymen. Its a technique where the a troller sends u a file u to open it, the file is made of a codeings which myself don’t know(i have studied Ankit Fadias Book, about ethical hacking 😛 the coding were quite complicated and boring)
And when u do u log out suddenly u say”wtf just happen” and when u say this u log in again that what all human will do and voila u password and E-mail is with him 😀 u don’t even know, if i am wrong everyone have the right to correct me in the comment and please -_- no OFFENSE against me PLEASE…
Regards
Aditya
effective on* a
the troller(no a)
sends a file to open*
voila your password is*
These are all the mistake i did i corrected it to 😛 , just don’t an expression-“man u suck at your english”
Hi Aditya,
Thanks for your valid points. Phishing is a method through which an attacker gets a password from a victim directly. In such a case the password is in plain text. In this blog post, we are talking about encrypted passwords. For instance, Gmail stores passwords of all its users in an encrypted form. If an attacker gets his hands on such a list he will need to decrypt the list to see the passwords in plain text.
Regards.
simple and nice and post 🙂
All said and done when we need scores of PW’s how is it possible to have
unique set for each login ?
emails, banks, insurance, oneline clouds, phone software list is never ending.
I did try out a pass word vault but once system crash washed everything away
along with all the PW generated by it and stored with in.
I also realised that its extremely unsafe as if somebody is able to break in there I will be facing a big shake down and will be left naked on the road.
With every ease comes danger lurking behind.
As far as I know after more than a decade of online presence, misfortune may strike if attention is drawn. Anonymity may keep one safe, just till one is discovered and found worth the efforts of hacking cracking and shoving whatever or all of it.
Thanks Alot rahul very fantastically explained such a complicated technique in a very simple manner.
Hats of you…..
And yes previously also More explanatory techniques and some more blogpost for hashing and salting functions were very well explained.
Thanks