Intelligent Firewall: Deciding the Fate of Your Enterprise Security
Is your enterprise Firewall blocking all potentially damaging traffic at the perimeter? Or are certain groups within the organization being given the permission to add exceptions to the Firewall list? Studies have shown that although Firewalls are implemented and configured by IT departments, many organizations actually face data breaches and loss due to ever expanding exception lists.
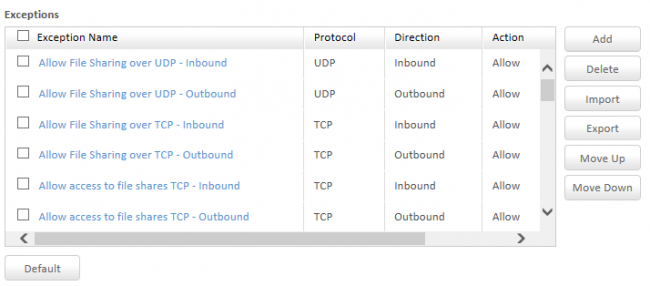
The benefit of providing exception lists for Firewalls and other advanced security settings in enterprise security products like Quick Heal Endpoint Security 5.3, is that certain high privilege groups can be given access to applications and traffic that everyone should not be allowed to access. However, when IT security policies at organizations are lax and flexible, exception lists become ever growing and overall security suffers as a result.
While IT managers take all necessary steps to deploy Firewalls as part of their enterprise solutions, it becomes redundant when a majority of apps and traffic are allowed through the exception list.
One major workaround to solve this is to strictly define and adhere to IT security compliance policies within your organization. Network security is as strong as its weakest link and human error or negligence is often the cause behind a majority of data breaches and network loopholes. To safeguard against this, structured employee training and retraining is absolutely essential.
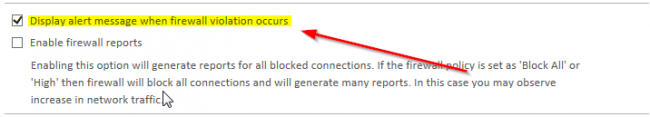
Moreover, we also recommend that you set up alert messages that notify your IT department as soon as a Firewall violation occurs. This enables your IT force to act as soon as possible with regards to any potential threats that may disrupt the operations of your network.
What to keep in mind while configuring Firewalls:
- Keep in mind the interactions of individual users with Web 2.0 applications. Certain people would require access to a part of an online service, but not the whole package. For instance, Google News would be harmless, but Hangouts would need to be blocked for users.
- Configuring Firewalls and associated settings should be accomplished within a few clicks. If it takes longer than that, then the process needs to be shortened. Quick Heal’s EPS 5.3 settings dashboard allows you to customize your Firewall settings with a few simple clicks.
- Make full use of the Firewall along with other embedded features like IDS/IPS, Group Policy Management, Application Control and more. Using a Firewall in isolation is not recommended and only when the entire system works in conjunction internally, can complete IT security be achieved.
- Define and adhere to clear Firewall rules that distinguish traffic based on IP addresses, domain names, protocols, ports and even keywords. Without the proper setup of Firewall rules, IT compliance policies cannot be maintained.
Click here to learn more about Quick Heal Endpoint Security 5.3 for your enterprise.
With Quick Heal’s Intelligent Firewall at your disposal, you can block all unauthorized access to and from your business network. Incoming traffic and outgoing traffic can be monitored and regulated centrally and customization rules can also be set at varying degrees like low, medium or high. However, every Firewall and enterprise security solution also needs human intervention from time to time so that any loopholes can be avoided. With the right measures in place, your enterprise network can be made almost unbreakable.


No Comments, Be The First!