Classic lies you should not let a cyber criminal use on you
Cyber criminals can devise various ways to get what they want from you. Manipulating people into carrying out certain actions or giving away confidential information is known as Social Engineering. And this is a rampant form of exploitation. Why? If you can get access to anything you want just by deceiving someone, why waste time creating a highly technical and sophisticated hack?
So, how exactly do cybercriminals execute social engineering tricks or lies?
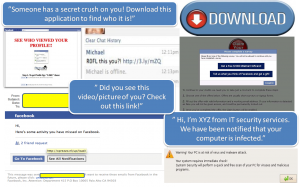
- Advertisements and Emails – These usually grab attention with their subject lines or body text.
- Phishing – Cybercriminals pose as genuine entities (a renowned bank or finance institution etc.) in order to extract confidential information through emails.
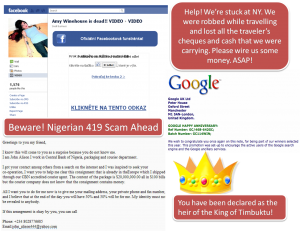
- Hoaxes – Typically known as the 419 scam, hoaxes are something that cyber criminals use to extract money or sensitive details. In this case, a cybercriminal would hack into accounts and message the person’s friends claiming to be trapped in a foreign country with no money. Other tricks/lies might include a question that piques the user’s interest and then directs them to a fake login screen. Criminals may be looking for your account information in order to send spam or to pull off a 419 scam.
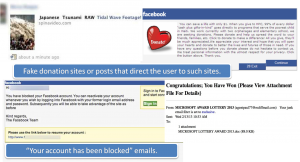
- Some of the hoaxes also include cashing on a panic attack or a recent endemic or natural calamity. For example, fake Japan Tsunami posts that came up everywhere on Facebook and Twitter after the calamity. The goal is to cheat individuals into submitting donations for relief efforts. People who end up donating to these sites often find their credit card information and money stolen.The classic ‘Your account has been deactivated or blocked’ or ‘You have won a lottery’ emails also fall into this category.
- Shoulder Surfing – Looking over someone’s shoulder and writing down Logins or ATM PINs.
- Tailgating – “Sneakers” use the ‘I’m late and in a hurry. Please let me in.’ phrase to create urgency and or physically follow someone into a restricted access area.
Businesses small and big or individuals, almost everyone is a target of these scams and social engineering tricks. Keep yourself updated and aware of such threats and risks. One of the best ways to avoid online tomfoolery is to install a good security software that warns, detects and blocks malicious sites or malware execution.

72 Comments
Hi,
Thanks for a great article.
Wow really gr8 info regarding “Cyber Criminals” and how to identify this crimes.
Rally thank you so much.
The article will be very helpful in detecting cyber crimes…Thank You so much for informing about all this….
how can i learn cyber crime course from u…………..is their any chance of that…i m not great in studies but i can try…
Thank u for giving awareness regarding cyber crime
Great information about cyber-criminal.
Thank you very much for sharing this with us.
hope you will always share your knowledge with us.
A must read for all the quick heal users, unfortunately they rarely see the message which pop up. Just worried about the day when a infected QH pop up a hacker message :). Difficult to happen but not impossible.
thnx 4 this information
how exactly do cybercriminals execute social engineering tricks or lies?
Hi Bharat
We have addressed your question in this post.
Regards,
very informational tips
Thanks soumya and Quick heal for the great article about cyber crimes. Thanks a lot.
prasad
oh good to share the information, thanks you might from orissa.I have little knowledge of computer facing lot of problems in my office
Hi Amitabh
Please contact our tech support at https://quickheal.co.in/submitticket.asp or at 0-927-22-33-000.
Regards,
THIS IS HIGHLY INFORMATIVE & USEFUL. WE SHOULD STOP FLAUNTING OUR PROSPERITY IN THE MANNER OUR NEW GENERATIONS DO. THEY SHOULD ALWAYS BE ON GUARD
nice
ciber criminal should punish strongly. International rule should made accordingly
these kind of warning r very useful for us to be a3ert nd careful in future. thks
What about our cyber laws? Why are these people not prosecuted? Pity, should do something.
Indeed a nice and informative article about cyber crime. But most of the times we fail to identify fake sites looking as similar to original sites like banks. Please do write the articles on how to identify such sites. Thanks Soumya and QH team for this eye-opener.
thankssssssssss……
Great information about cyber-criminal
Thank you very much for sharing this with us
hope you will always share your knowledge with us
That’s really educative. It’s really useful and protective. Thanks.
Hi..!!..utmost thanks for even-full info….
keep on going…
hope forever………
Thank you very much for sharing this Gr8 information about cyber-criminal.
with us.
hope you will always share your knowledge with us.
hi,
thank you very much for this info.
good job
keep up the gud work.
gud luck
Hi, good piece of info thanx a ton
regards bye tc.
hey! thanks great stuff,thanks for the warning on all these kind of Cyber Criminals!
once again thank u soooo much,great advice!really helps!
Great information about cyber-criminal.
Thank you very much for sharing this with us.
hope you will always share your knowledge with us.
please send me informations every time thank you
I hesitate to click on the pop ups but not so when it is from Quickheal. Good information.
Thanks for the article.
hi, thanks for publishing regarding the cyber crimes. yes, i do get mails from many years and sms every week. anybody who gets these type of mails / sms’s should be very much careful and not to share his / her personal details to unknown person. yet many people fall on this trap. once again thanks for sharing this message.
Thanks for suggestion
Nice, Very informative information.
Hi
Thanks for information through great and Helpful Article.
Thanks
Hi Thank u for help through Great Article
Thanks
Good information……………
An useful Article on Cyber Crime…………..Must read.
Thanks Soumya for posting.
what actually a hoax is…?
does an antivirus program provides protection against hoaxes..?
Hi Nitish
Hoaxes as described in the article are tricks, these websites and emails are designed to trick you into disclosing personal information such as bank account details, passwords or credit card numbers.
The key here is to be aware and learn more about such fake websites and emails. And yes, a multilayered security software also helps you in staying safe online.
Regards,
Is there anywhere to complain (For eg email id of cyber police etc.) if we receive phishing or specific mails for e.g. I got an urgent message on my mobile to mail someone as they posed to be my prospective client. This way they replied back to me and I could not identify the same as spam.
Regards,
Thanks! The internet is an ocean of predators,safety and privacy is always a problem. Keep up this good work.
This is a nice and informative article about law of cyber crime. But most of the times we fail to identify fake sites looking as similar to original sites like govt/ banks. Please do write the articles on how to identify such fake sites. Thanks Soumya
Hi Mr. Sharma
Thank you for your suggestion.
Regards,
Thanks. This information is very helpful,keep updating us please.
Nice information !
Good effort to make people aware. Please keep it up. Also pleased to see that queries raised are also attended. Thanx.
Great & useful information about cyber-crime. Thanks a lot.
thanx 4 telling me….
Hi
thanks for information.
Regard
jitender
Thanks ma’am, it was informative. Good job.
what is the best way to recognize fake mails
thanx for giving information about cyber criminal and thanx for given protection
Thanks Soumya. I am visiting my daughter’s family in the US. I have been watching TV advertisements on Identity thefts & how some people have lost all their bank balances. This is one reason why I am not into net banking.
I am told even some International banks of American origin have lost billions due to fraudulent transfer of funds. What is even more scaring is that your bank balance will not reveal the transfer till it is too late ! Could you advise as to how this theft can be avoided.
Is there a sure way of sending all such emails in Spam and deleting them without bothering about them any further?
Thanks. This information is very helpful,keep updating us please.
Good efforts to make people aware. keep it up.
Hi! Great efforts to make people aware. keep it up. Thanks & Good Luck.
WOW!
Really nice and informative. I didn’t know about these kinds of cyber-crime before!!
My Antivirus software is not update when internet connection. please arrenge to repair whom path is missing. I do not know about it.
Hello Mr. Pradhan
Have you tried contacting our tech support yet? Please submit a ticket at https://quickheal.co.in/submitticket.asp or you can reach them at 0-927-22-33-000.
Regards,
This information is very helpful,keep updating us please.
KNOWLEDGE SHARED IS WELL APPRECIATED. THANK YOU.
Thanks . This information is very helpful , keep updating us please.
Thanks soumya,
For sharing fantastic article with detailed summary of various attacks.
when we are downloading something some unwanted things usually come to the screen, are they linked to such type of cyber-criminals. thanks for this article
Yes they are linked.
Hi,
Thank you so much for your concern. God bless you always. Amen.
for personal use
A lot of thanks for sending the information.