Quick Heal Terminator (UTM) – Improve Productivity with Content Filtering
As per an insightful study conducted by Google India, around 57% of SMEs in the country proactively use their website as a sales channel. Using the Internet for accessing email is highly prevalent, but around 71% of enterprises also use the ‘World Wide Web’ to search for suppliers and vendors. A significantly large number also use the Internet for online listings, online advertisements and for generating business leads, amongst other things.
This wide proliferation of the Internet for business comes with its own set of perils. These SMEs, which are around 40 million in number, are mostly unprepared for Internet-based attacks and also face a general lack of awareness with regards to network security. This puts them in the high-risk category. They are susceptible to attacks by sophisticated hackers who use advanced infiltration techniques and social engineering methods. All this makes SMEs vulnerable to hacking, cracking, phishing, viruses, worms etc. As a result, it is imperative that SMEs monitor and control web content access.
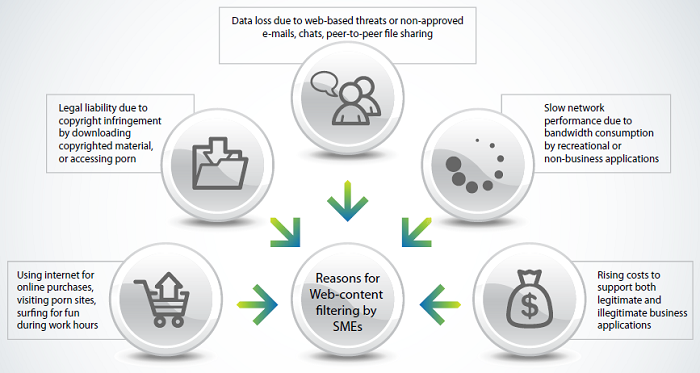
Sources of major threats to networks
While analyzing the various channels through which security threats can gain entry into a business network, we have found a few common avenues of content risks to be consistent across organizations of all sizes. These attack vectors can be placed in the following categories:
- Data loss due to web-based threats or non-approved emails, chats and P2P file sharing programs
- Legal liability due to copyright infringement by downloading copyrighted material or copying Intellectual Property of other entities
- Using the Internet for personal online shopping, visiting illicit websites (like adult sites or gambling sites) or surfing for fun during work hours
- Slow network performance due to bandwidth consumption by recreational or non-business applications
- Rising maintenance costs to support both legitimate and illegitimate business applications
Traditional methods of ‘Content Filtering’ are now outdated
The widespread usage of the Internet over the years has brought hordes of side-effects and security threats along with it. New and complex attacks continue to wreak havoc on unprepared systems and networks. Traditional ‘Content Filtering’ has operated under the basis that the content is manually or heuristically analyzed, and then it is either blocked or allowed. The source of this content, or other relevant criteria, is not taken into consideration.
This method is useful as it prevents users from viewing inappropriate websites, but it is not enough. This ‘URL Filtering’ method only blocks websites, or certain sections of websites by categorization, storage of databases of categorized URLs and by filtering the URLs based on this categorization.
Initially this process was carried out manually, and slowly it evolved into a heuristic process. However, this is not enough as many times legitimate sites are also blocked and malicious content is allowed to pass through. While these traditional methods have been good in the past, the need for Content Filtering today is far more pressing and intensive.
Quick Heal Terminator (UTM) has a novel solution
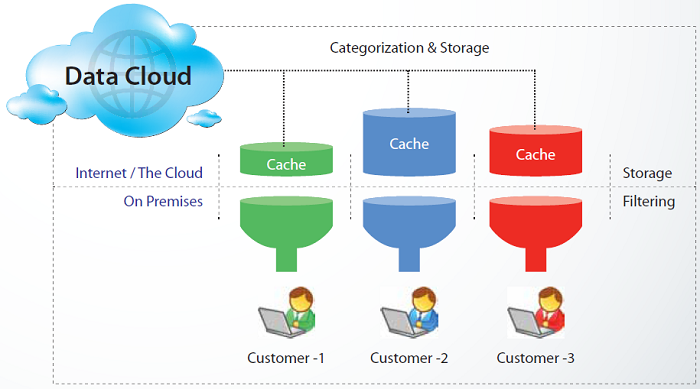
The solution that Quick Heal Terminator provides to this pressing issue is known as ‘Data Cloud URL Filtering’. Since new websites and pages are being added to the Internet every day at a fervent pace, locally managed databases and heuristic engines cannot serve this vast size and the unique specific needs of individual users anymore.
Quick Heal Terminator’s innovative and cutting-edge approach to content filtering seamlessly transfers the database of allowed and blocked websites and categories into the cloud. This advanced technology is known as ‘Data Cloud URL Filtering’ and it provides a more flexible, comprehensive and accurate form of URL filtering technology since it does not rely on limited resources of local storage.
Noteworthy benefits of Data Cloud URL Filtering
The advantages of Data Cloud URL Filtering are manifold and they benefit an enterprise in several different ways. Effective and timely coverage of databases is provided every few minutes by scanning almost a third of global Internet traffic. These updates are directly sourced from automated web crawling and classification techniques, combined with manual classification from professional researchers. Data from thousands of globally deployed Quick Heal UTM appliances is also delivered to classify uncategorized or unsafe URLs.
Unused domains and websites are periodically phased out, and if there is a mistake in URL categorization, correction requests are promptly responded to. Moreover, the database is cached at the user’s end so the response time is instantaneous.
A wide variety and extremely large number of URL categories and a comprehensive URL database is provided by this method. This database contains close to hundreds of millions of the most relevant websites. This large silo of data grants granularity to the user to block specific sections of a website. With this functionality, the user gets a highly customized experience which is very specific to his network security needs and operational scale.
With the use of this technology, Quick Heal ensures that enterprise users get up-to-date protection against all types of viruses and Internet attacks. At the same time, optimal performance is also guaranteed along with faster detection, lesser resource utilization and secure output. Accuracy and real-time compliance with the company’s Internet usage policy is also maintained.
Quick Heal Terminator also combines the best of both worlds by offering a combination of list-based URL Filtering and real-time Cloud URL Filtering. For instance, a user can unblock a particular URL (using list-based URL Filtering) even if the category of the URL is blocked through Data Cloud URL Filtering.
Salient features of Quick Heal Terminator (UTM)
With business growth, SMEs often face massive challenges in terms of maintaining network security without restricting Internet usage and hampering productivity. They need a solution that empowers employees and boosts their productivity while also securing the network and protecting sensitive data.
With that end goal in mind, Quick Heal Content Filtering offers benefits such as effective accuracy and coverage, faster performance and ease of use. These features are available in a comprehensive Quick Heal Terminator (UTM) appliance without compromising on other network security benefits such as Firewall, Gateway Antivirus, IDS/IPS, Gateway Mail Protection, Load Balancing, VPN, Bandwidth Management and more.
SMEs have very specific needs of ensuring foolproof network security. Quick Heal Terminator helps meet all these needs through one easy to use solution without having to deploy multiple solutions for each specific security requirement.
You can also learn more about Quick Heal Terminator (UTM) by visiting this link.
Or, you can also view our UTM whitepapers by visiting this link.

![2014-09-04 14_56_36-QHUTM_2014_new [Compatibility Mode] - Microsoft PowerPoint (Product Activation F](https://blogs.quickheal.com/wp-content/uploads/2014/09/2014-09-04-14_56_36-QHUTM_2014_new-Compatibility-Mode-Microsoft-PowerPoint-Product-Activation-F.png)
No Comments, Be The First!