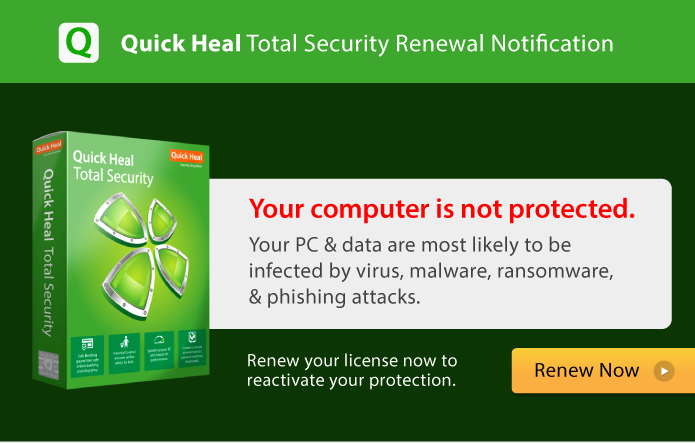
You are at your computer, engaged in some important work and suddenly a message pops up on the…
Archives by Date
Beware of getting scammed during Black Friday & Cyber Monday SALE!!
As holiday shoppers gear up for a shopping spree on Black Friday and Cyber Monday, it’s important…
Teaching kids the good, the bad and the ugly of the Internet
This children’s day let’s talk about one of the most relevant topics for kids these days- the Internet! Children…
This Diwali gift your kids online safety with parental control
Diwali holidays are just round the corner and your kids might have already received their holiday assignments. But,…
Obfuscated Equation Editor Exploit (CVE-2017-11882) spreading Hawkeye Keylogger
Cyber-attacks through phishing emails are increasing and generally, attackers use DOC embedded macros to infiltrate victim’s machine. Recently…