Do you find it convenient to shop and bank online using mobile payment apps? Most would have ‘yes’…
Archives by Date
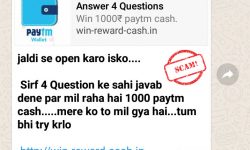
Beware of the new WhatsApp message scam that promises Rs. 1000/- Paytm cash!
WhatsApp currently has over 200 million monthly active users in India. No wonder it has become a popular…
An in-depth analysis of a new, emerging “.url” malware campaign – by Quick Heal Security Labs
Last week, we had blogged about the emergence of a new attack vector ‘.url’ which is used to…
An analysis of the Zenis ransomware by Quick Heal Security Labs
Quick Heal Security Labs has come across a new ransomware that goes by the name ‘Zenis’. The ransomware…
How cyber smart are you? Take this cybersecurity quiz to find out!
Get Started! Your Score: Your Ranking:
The A-Z dictionary of cybersecurity terms
Whether you are a normal user or a tech-guru, being aware of the computer security threats will help…
Email campaign using .url extensions to abuse Internet Explorer vulnerabilities (CVE-2016-3353)
In the wild, malspam campaigns are a major medium to spread malware. Previously, we have written about such…
A free guide to 7 computer viruses you should know about
Computer viruses are nasty little programs that are designed to lay waste to your computer. Some destroy files…
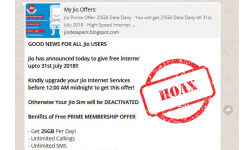
Do not fall for the WhatsApp message about Jio Prime Offer. It’s a hoax!
A message about a Jio Prime offer is circulating among WhatsApp users. Do not fall for it because…
Chinese, Russian hackers counting on Apache Struts vulnerabilities – a report by Quick Heal Security Labs
Apache Struts is an open-source CMS based on MVC framework for developing Java EE Web Applications. Apache Struts has been widely…