Worm.Gamarue – What it is and How does it Evolve?
Another popular malware whose mode of transport is removable drives, is known as worm.gamarue. This malware is also designed to communicate with a remote server to report its infection and download arbitrary files. These downloaded files are detected as Worm.Gamarue.B by Quick Heal.
Primary Analysis:
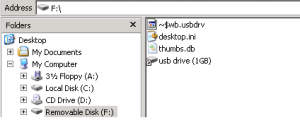
When USB drive shortcut is opened, .dll file which is present in the same directory (root directory), is executed. It is also used to update Thumbs.db present in the same directory, if internet connection is available. Thumbs.db, in turn, is used to create TrustedInstaller.exe.
Fig.1: Snapshot of infected removable drive
This TrustedInstaller.exe is dropped in a new directory in the root drive. Newly created directory would be named as either C:temp or C:MSI .
Components Used for Malware Execution:
Clean File Scenario:
1. USB Drive (.lnk): Removable drive shortcut icon to open respective drive.
Fig.2: Clean drive shortcut icon
2. desktop.ini: This is a hidden file used to customize and adjust settings for the Windows folders in which it is present.
3. Thumbs.db: Thumbs.db files are stored in each directory that contains thumbnails on Windows systems. These files are created locally among the images, preventing system wide use of the data.
Our Case:
1. USB Drive (.lnk): This is a removable drive shortcut. If you notice, the “infected drive shortcut icon” displays a specific size (to misguide the user), whereas, the “clean drive shortcut icon” does not.
Fig.3: Infected drive shortcut icon
When the user clicks this icon in order to explore its contents, at the back end it executes *.dll file present in the root of removable drive, by executing the command which can be as follows:
“%homedrive%WINDOWSSystem32rundll32.exe _WHVX.nil, rundll32”
Here,
%homedrive%WINDOWSSystem32rundll32.exe – is a command used to execute the .dll file.
_WHVX.nil – is the name of .dll file which varies.
Rundll32 – is the name of the export function in above .dll file.
2. *.dll: It is used to decrypt code in Destop.ini and execute the decrypted code.
3. Desktop.ini: The code contained in desktop.ini first tries to download an updated copy of Thumbs.db, replacing the existing file in the USB drive if internet connection is available.
4. Thumbs.db: This is actually an encrypted PE file, which upon decryption, gets copied into TrustedInstaller.exe.
Evolution & Modification:
*.dll uses desktop.ini to download TrustedInstaller.exe.
EVOLUTION STAGE 1
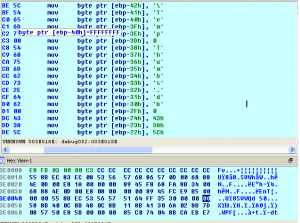
Initially *.dll & desktop.ini file used to be readable.
Desktop.ini was present in Unicode form.
Fig.4: Stage 1 desktop.ini file
EVOLUTION STAGE 2
Later, Dependency information in *.dll & downloaded information in desktop.ini became encrypted.
Fig.5: Stage 2 dll file
Fig.6: Stage 2 desktop.ini file
EVOLUTION STAGE 3
Earlier files (desktop.ini & .dll) were obscured so that decryption could not be easily traced.
Fig.7: Stage 3 dll file
Fig.8: Stage 3 desktop.ini file
Technical Details:
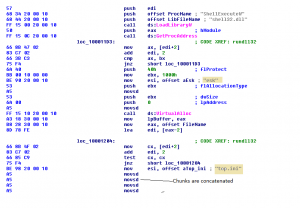
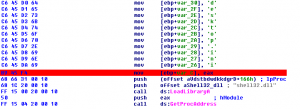
Dll file is executed with the help of rundll32.exe
1. Shellexecute is used to open desktop.ini file by passing its handle.
2. This desktop.ini file is read in memory for further process.
3. This desktop.ini is decrypted if it is in encrypted form using decryption loop which is present in .dll file.
4. Desktop.ini contains the code to check internet connection status. Depending on the connection status, it will either download latest thumbs.db or use currently present thumbs.db. This thumbs.db contains TrustedInstaller.exe in encrypted form. Domains from which the file is downloaded may change.
We have gone through various domains from where it is downloaded. Some of the domains are as follows:
hxxp://sobea.in
hxxp://m.deltaheavy.ru
hxxp://suckmycocklameavindustry.in
hxxp://thesecond.in
Fig.9: Contents of destop.ini After Decryption
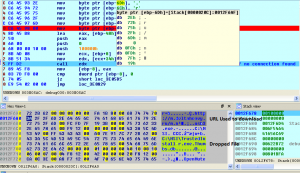
1. This Thumbs.db is in turn decrypted & copied to a newly created folder (C:temp or C:MSI) in the root directory as TrustedInstaller.exe.
2. TrustedInstaller.exe is used to infect removable drive. Removable drive contains shortcut & its (removable drive) contents are put into folder which has hidden property enabled.
3. On opening this shortcut, it runs a .dll file at back end & opens a hidden folder, so that the user finds contents of the drive without knowing that the malicious file has already been executed.
4. This dropped TrustedInstaller.exe, when runs, performs the following actions:
a) Drops another component of Worm.Gamarue.
b) Writes encrypted data to the following registry entry:
HKCUSOFTWAREe_magic
[The binary written to HKCUSOFTWAREe_magic is another encrypted version of the TrustedInstaller.exe component, which is subsequently used to infect more removable drives.]
c) Writes data into the following registry entry:
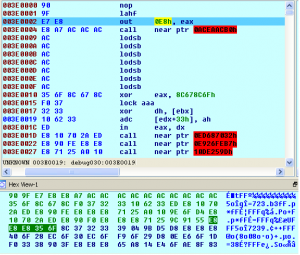
HKLMSOFTWAREMicrosoft022FF03
The data written to the registry entry HKLMSOFTWAREMicrosoft022FF03 is interesting, as it contains what looks like a ZIP header at the start, but is not actually a ZIP archive.
Fig.10: Compressed Header written to the registry entry HKLMSOFTWAREMicrosoft022FF03
The data is encrypted; after decryption it turns out to be a compressed executable code.
Fig.11: Header Contents after decompression
1. Dropped file from TrustedInstaller.exe runs the system file %System%wuauclt.exe and injects code into that process. This injected code reads the data from the registry entry HKLMSOFTWAREMicrosoft022FF03, decrypts it using a 32-byte key stored within the code, and decompresses it using the widely available aPLib compression library.
2. The result is the worm’s spreading component: A DLL which checks for removable drives and infects them. At no point is this component written to disk, which makes it difficult to remove the infection.
3. Coming to the end of the cycle, if a removable drive is found, it is infected/re-infected with the encrypted data read from the registry entry HKCUSOFTWAREe_magic and written to the file “Thumbs.db“, and the flat binary file with 32bit code is written to “desktop.ini“, together with the loader DLL and a shortcut.
Every time a malware or its strain gets detected, it evolves and steps up its game. And this process continues. We will keep you posted as we come up with further findings on such malwares and others.
Blog post acknowledgment – Quick Heal Threat Research and Response Team.
No Comments, Be The First!