Why is Network Security Important for SMEs
As technology is soaring to new heights, malware authors are getting more sophisticated in creating nastier malware to target businesses. Large enterprises take adequate measures to secure their network. This, however, is not usually the case with small and medium-sized businesses – a fact that is exploited by hackers. SMEs are no longer the less-preferred targets for hackers. In fact, such businesses are used as a lasso by hackers to bring down bigger organizations.
This post puts forth some points to help you understand the importance of network security, its business benefits, and how neglecting it can uproot your stand in the market.
Network Security – A Basic Overview
Every enterprise network is vulnerable to threats such as unauthorized access, data breach, modification, and exploitation. An IT infrastructure that secures the network from such threats is called network security.
Network security is an amalgam of policies and procedures that are put into place to reinforce and secure the usability and integrity of the network and its associated resources.
Why is Network Security Required
This question can be answered by the fact that cyber threats are proliferating at an exponential rate. The present day security threat to any enterprise IT has surpassed its ancestors by light years. Cyber threats of today are multi-faceted, sneakier, and technologically more advanced. Some of the most common types of threats to network security include:
Advanced Persistent Threats (APTs)
APTs are threats that keep a low-profile to stay hidden, and are highly persistent in their attacks. Such attacks are slow but recurring in nature. They may stay hidden in the compromised network and wait for the right moment to strike.
Adware and Spyware
Spyware are software that secretly steals sensitive information from the victim’s computer. Adware are software that display unwanted advertisements on the compromised machine. Sometimes, adware are classified as a type of spyware because they track user’s personal information and send it to a third party without the user’s knowledge.
Human Error
Unarguably, the weakest link in IT security is the human element. One phishing email, one unaware user and one click is all it takes for a hacker to take down the entire network of an organization.
Zero-day Attacks
An attacker’s attempt to exploit a known but still unpatched security vulnerability is known as a zero-day attack. It is also known as a zero-day exploit.
Denial of Service Attacks (DoS)
DoS attacks are classified as one of the most critical types of targeted attacks against enterprise IT network. Such attacks are crafted to flood a targeted network by useless traffic (more requests than the server can handle), so that it becomes unavailable or inaccessible to its intended users.
Man-in-the-Middle Attack
Such attacks are deployed by an attacker to intercept information that takes place between computers in the targeted network. With such attacks, the attacker can monitor, record, and even control the relay of communication.
What Network Security Covers?
When we speak of network security, we are referring to a solution that offers multiple layers of protection. This is to ensure that if one layer is down, other layers are still there to stop an attacker from advancing any further. In other words, the more the layers of security, the lesser the opportunity for attackers to get in and out of the network.
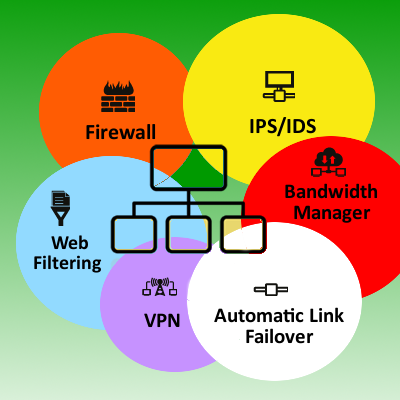
Mostly, the following components should make up for the network security solution of an enterprise:
Firewall – to prevent unauthorized access to the corporate network.
IDS and IPS – Intrusion prevention system and intrusion detection system to shield unpatched application in a network from getting exploited by an attacker.
Virtual Private Network – to provide a secure tunnel for remote access.
Bandwidth manager – to allocate bandwidth depending on the need of an application or user.
Web Filtering – to filter out inappropriate or suspicious websites that can jeopardize productivity or risk a malware attack.
Automatic Link Failover – to manage multiple ISP lines so that the enterprise network does not suffer from any Internet down time.
See also: Why a Simple Antivirus Isn’t Enough for Small and Midsize Businesses
The repercussions of a cyber attack on an enterprise network can be huge. It may not only lead to paralyzed operations, disgruntled customers, but also expensive lawsuits. Above all, it might mar the company’s reputation to an extent that is beyond repair.
Adopting a simple yet easy to deploy network security solution like the Quick Heal UTM can keep your enterprise network shielded from threats such as the ones discussed above, and reinforce the business’s reputation. Request for a free demo of Quick Heal UTM.
3 Comments
hi.
i work as an it administrator in a small office with 1 server 13 n computing devices and 10 computers on our server we use quickheal antivirus pro 2014 i want to deploy utm and before i deploy it i want to try it out so can uu please give me the download link i had contacted for a request for a demo atlist 10 days before but have not got any responce
Hi Austin,
Thank you for your interest in Quick Heal UTM. We apologize for not responding to your request. We request you to kindly visit the following link and provide a few basic details. Our team will get in touch with you for the demo.
https://bit.ly/1bvyRqB
Also, we have forwarded your grievance to the department concerned.
Regards,
Thanks……….