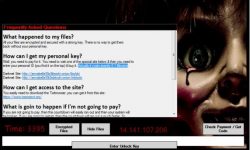
Ransomware is becoming one of the most perilous cyberattack methods and also the most habitual techniques for cybercriminals…
8 tips to avoid a spyware attack
Spyware refers to software that spy on your Internet browsing activities, record keystrokes, and collect almost any type…
An in-depth analysis of a new, emerging “.url” malware campaign – by Quick Heal Security Labs
Last week, we had blogged about the emergence of a new attack vector ‘.url’ which is used to…
A free guide to 7 computer viruses you should know about
Computer viruses are nasty little programs that are designed to lay waste to your computer. Some destroy files…
The Runner: a key component of the SamSam ransomware campaign – An analysis by Quick Heal Security Labs
In Jan 2018, Greenfield, Indiana-based Hancock Health (healthcare network) was attacked by SamSam ransomware. It encrypted the files…
IcedID – a new sophisticated banking Trojan: a technical analysis by Quick Heal Security Labs
IcedID is a new player in the banking Trojan family. It has a modular architecture and capable of…
A Report by Quick Heal Labs on Password Stealing Malware
Almost every computer user has more than one account for social networking sites, email accounts, bank accounts, online…
Security Vulnerabilities for Android and iOS Hit An All-time High in 2015
Quick Heal hopes it has been a good year for you. But, has it been a good year…
5 Common Myths that Stop People from Using an Antivirus
While this may seem like a bit of an odd subject to venture into, in this blog post…
FIFA World Cup malware threats – Don’t ‘Risk Everything’!
With the FIFA World Cup well and truly underway now, hackers and spam artists are having a field…