Simple security tips to avoid Twitter phishing scams
Twitter is a great platform for sharing news, opinions and links. Created in 2006, Twitter has more than 500 million active users today and generates more than 350 million tweets every single day. This has naturally led to several phishing attacks over the microblogging platform. The fact that links are instantly published on a large scale over Twitter makes it a viable attack ground for malicious parties.
Phishing scams over Twitter
Such scams are a common occurrence over Twitter and they manifest themselves in the form of Direct Messages (DM) from someone a user is following. Usually, accounts that have a large number of followers are targeted because their reach spreads to a wider base.
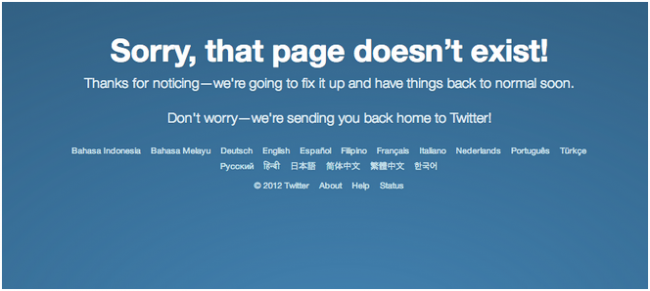
A victim receives a DM with a common message like “LOL is that you?” or “Someone is spreading nasty blogs about you.” This is accompanied by a shortened link that takes the victim to a page that looks something like this.
The victim is then taken to a fake Twitter log in page where he enters his Twitter ID and password and hands it over to the attacker unknowingly. This further highlights the dangers of passwords today.
How to avoid Twitter phishing scams?
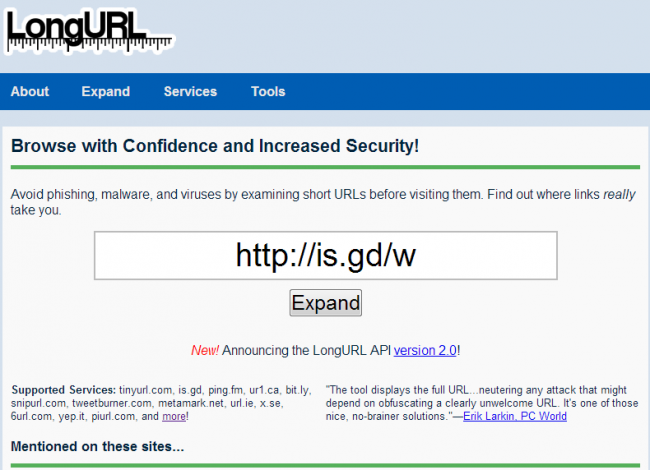
The most important thing is to not fall for such scams. Use a URL expander like ‘LongURL’ to check the true identity of a shortened link before you click on it.
Additionally, it is advisable to use a strong password for Twitter in the first place. Do not share your Twitter ID and password with third parties and do ensure that you are on the legitimate Twitter website when you log in. These tips on how to avoid the phishing trap will also be helpful. Also ensure that your OS and system protection software are completely patched and updated. To receive updates from Twitter Security regarding safety updates you can follow @safety and @spam.
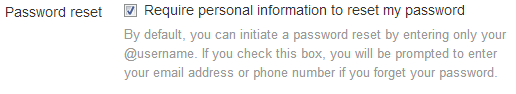
The best preventive measure you can take is to enable the option that requires you to enter a phone number or email address in order to reset the password. For this, click on the gears button in the top-right corner when you are signed in and select Settings. Now check the box next to the Password Reset option. Click on Save Changes and enter your password to confirm. This ensures that if the account password needs to be changed, either an email address or phone number will be required.
To associate your mobile number with your account click on the gears button in the top-right corner when you sign in, click on Settings, select Mobile from the list on the left side, enter your phone number and service provider and click on Activate Phone.
I fell for a Twitter phishing scam. Now what?
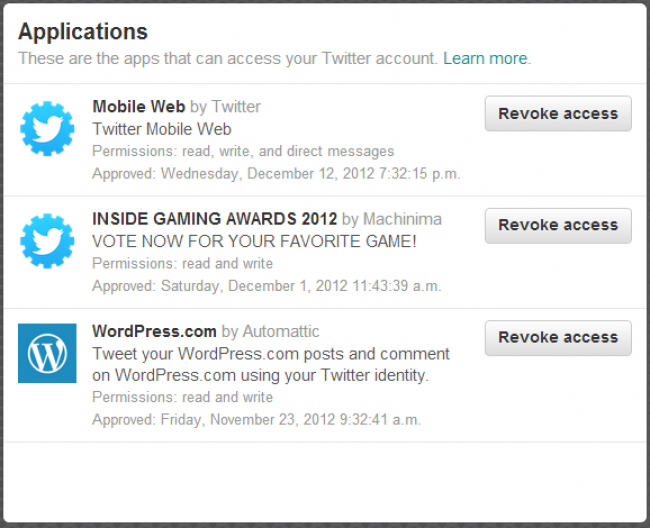
The first thing you should do is change the password immediately. Next, delete all the bogus tweets that were sent out during the time period when the account was compromised. Lastly, revoke connections to all third-party applications that are integrated with your Twitter account.
To revoke access click on Apps when you enter the Settings page. Click on Revoke access for the services you wish to revoke.
Some people have also complained about fake emails that appear to be from Twitter. These emails usually inform the receiver about a password reset or some other security update. Such emails should be treated with extreme caution to ascertain if they are genuine or not. You should be aware that Twitter never sends attachments by email nor does it request passwords via email. These are signs that an email could potentially be fake. If you receive a fake email that claims to be from Twitter, forward it to spoof@twitter.com.
Twitter phishing scams have become very common over the last year or so. With this in mind, it is necessary to be aware of all the precautions mentioned here. Phishers take advantage of the fact that people pay very little attention to what they are actually clicking on so take some extra seconds to have a second look. With the right awareness, such phishing scams can be avoided completely.

2 Comments
this is a nice guideline by quick heal. I appreciate you.Nicely informed.
Thanks alot rahul,
I am very regular user of twitter,thanks for generating the awareness and suggesting/advising the security tips and cautiousness
Really thanks