Ramnit Malware: Improvising its weapons

Ramnit was introduced as a worm into the cyber world during the end of 2010. In these few years, researchers at Quick heal Labs have observed a drastic change in the components of this malware. Malware authors of this family are continuously upgrading to adapt to the changing needs of the market. An interesting trait to be noted here is, while updating the malware, its authors stay consistent with their own core components and behavior.
This paper aims to study and present the malware’s infection vector, behavior, workflow, and various components. The paper also discusses some important security measures to be taken against the malware.
Infection Vector
Earlier version of ramnit used removable drives to spread its infection. With newer techniques, its authors started spreading the malware by embedding in other malware in an encrypted form. Some common techniques used by ramnit to spread its infection include:
- USB drives
- Other malware
- Exploit kits
- URL spoofing
- Bundled applications
Download this report for a complete analysis on the components used by Ramnit.
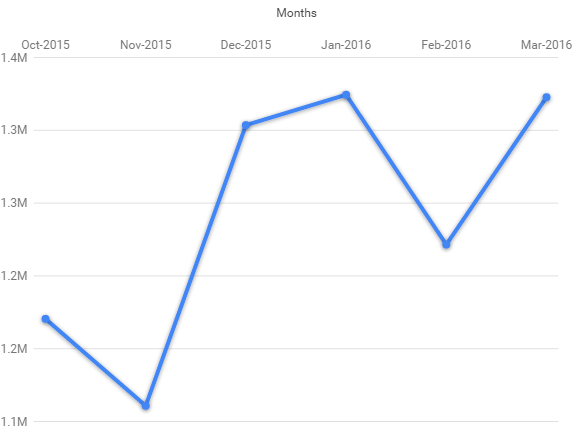
Statistics: VBScript Injection
The below chart represents the statistics of the infected VBScript detection at Quick Heal for the last six months.
Security Measures
- Use genuine operating systems and ensure that they are patched with the latest security updates. This will prevent hackers from exploiting security vulnerabilities.
- All software must be up-to-date.
- Virus database must be up-to-date.
- Be careful while using removable drives.
How Quick Heal helps
Quick Heal Total Security helps counter this threat with the following security features:
- Memory Scan
- Drive Scan
- Safe Banking
- Network Protection
- Boot Time Scan
- Network Drive Scan
Appendix:
Registry Key Deleted
HKLM\SYSTEM\ControlSet001\Control\SafeBoot
HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot
HKLM\SYSTEM\ControlSet001\Control\SafeBoot\AlternateShell: “cmd.exe”
The purpose of deleting these keys is disabling the starting of computer in safe boot mode.
Registry Key Added
HKLM\SYSTEM\ControlSet001\Services\Micorsoft Windows Service
HKLM\SYSTEM\CurrentControlSet\Services\Micorsoft Windows Service
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_MICORSOFT_WINDOWS_SERVICE
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_MICORSOFT_WINDOWS_SERVICE
With help of these, it registers the driver component as a windows service.
Registry values modified
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones
HKU\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
Commands and Response:
While traversing memory of process we get some interesting commands:
| Response Code | Response Received |
| 150 | Data connection accepted |
| 150 | Opening data connection |
| 200 | Port command successful |
| 227 | Entering Passive Mode |
| 250 | CWD command successful |
| 250 | File executed successfully |
| 266 | ABOR command successful |
| 350 | File exists. Ready for destination name |
| 350 | REST supported. Ready to resume at byte offset |
| 425 | Can’t open data connection |
| 426 | Cannot retrieve. Failed. Aborting |
| 451 | Failed: Cannot build data connection |
| 451 | Requested action aborted: local error |
| 500 | Syntax error, command unrecognized |
| 501 | Syntax error in parameters or arguments |
| 503 | Bad sequence of commands |
| 550 | No port specified. |
FTP Commands:
| Response Code | Response Received |
| 150 | Data connection accepted |
| 150 | Opening data connection |
| 200 | NOOP ok |
| 200 | Port command successful |
| 200 | Type set to %c |
| 211 | Status: undefined |
| 214 | Help id disabled |
| 215 | UNIX Type: L8 |
| 220 | 220 RMNetwork FTP |
| 221 | Bye! |
| 226 | Transfer ok |
| 227 | Entering Passive Mode |
| 230 | User logged in, proceed |
| 250 | CWD command successful |
| 250 | Directory removed |
| 250 | File deleted successfully |
| 250 | File executed successfully |
| 250 | File renamed successfully |
| 257 | %s is current directory |
| 257 | directory created |
| 266 | ABOR command successful |
| 331 | Password required for %s |
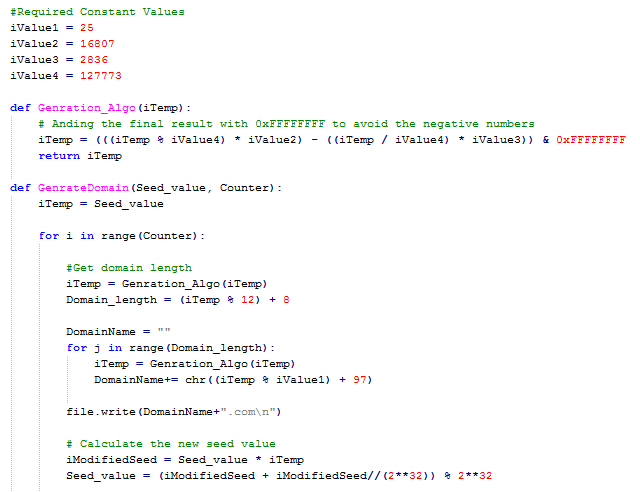
Ramnit DGA Implementation:
Domain generated with DGA (Initial Seed: 0x606D35BF)
| jrkaxdlkvhgsiyknhw.com | iddfmolfvrdoeyxou.com | mxudiunvxecbgpdhhc.com |
| eesbmknaxr.com | mshsflwekk.com | ioeccgcbxxcxsrqjy.com |
| jkrehcrgib.com | gqrtykjc.com | arjxjuvppvrmxbpueg.com |
| apthdsknufgxporcvvn.com | ikcnskrruwrkilcxdip.com | icowvgucyvl.com |
| pexddmcvuxqrksvvv.com | tgjmrxkqp.com | lffkkbfpqxbyxeaxsvr.com |
| wrjjpqbbyofxtexwri.com | wccshmrmeqk.com | xvjnpdppk.com |
| pokparydnggdwik.com | txvxlbrbtrvttwtty.com | archxhobmrdiqal.com |
ACKNOWLEDGEMENT
Subject Matter Expert:
- Swapnil Patil (Threat Research & Response Team, Quick Heal)
2 Comments
Help
Hi,
How may we help you?
Regards,