Quick Heal detects malware misusing the fame of Patanjali’s Kimbho app
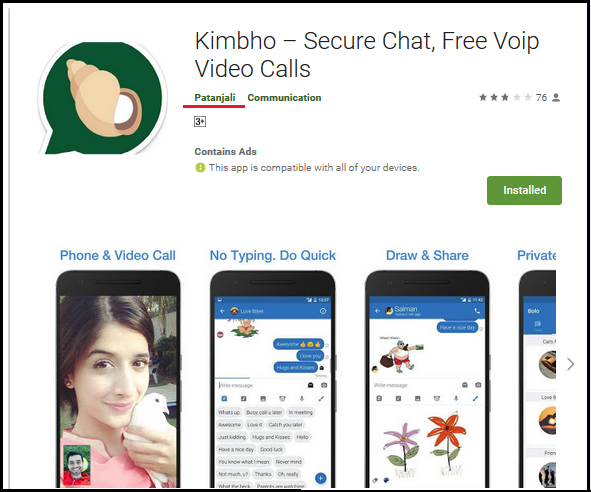
When Patanjali’s Kimbho app came to Google Play Store, it made some headlines on the Internet, newspapers, TVs, etc. It had 1.5 lakh downloads in just 3 hours. Kimbho app was designed for socializing, messaging and sharing videos, images, etc., same as what the WhatsApp and Facebook app do. However, due to some security issues, they removed the app from the Play Store.
Although the original Kimbho app was removed, it left a scope for cyber criminals to publish a fake and malicious version of the app on Google Play Store. Quick Heal Security Labs has spotted a malware that exactly looks like the Kimbho app. It attacks users by hiding and showing ads after certain intervals of time. This malware was downloaded from Google Play Store for more than 1000 times before it was removed.

Fig 1. A fake version of the Kimbho app on Google Play
Is it fake or genuine?
The developer‘s name and website mentioned in the additional information part on Google Play makes the app look like it is the genuine app from Patanjali.
We analyzed the digital certificates of the genuine and the fake apps and found that they are not the same.

Fig 2. Fake developer name
In the original Kimbho app, there was a verification error while opening a user account because the server was down. Here, it has been updated as that Verification Error Fix. After analysis, we got to know that whatever updated on Google Play is contradicting with our analysis.
Here are some user reviews which are also contradicting with the information given on Google Play.

Fig 3. Review of users
Analysis of fake and malicious version of Kimbho app
App Name: Kimbho – Secure Chat, Free Voip Video Calls
Package Name: com.bolo.chating
MD5: f6682f8d3a5de26266146f0830776286
Size: 4.11MB
On installation, it displays the icon of Kimbho app. When a user clicks on it, it hides and runs ad services in the background. This makes it difficult for the user to know if or not the app has been installed.


Fig 4. After it hides, it uses the icon of Google Play Store.
After hiding the malware uses the logo and name of Google Play Store to confuse the user. The fake Play Store can be uninstalled as it is not an inbuilt app. Thereafter, it starts showing ads after a timespan of 10-15 minutes. These are unwanted ads, shown in between other applications interfering with the user‘s activity.
This malicious app only takes advantage of the popularity of Kimbho app to earn money by displaying ads.


Fig 6. Ads shown by the malware
How to stay safe from fake mobile apps
1. Check an app’s description before you download it.
2. Check the app developer’s name and their website. If the name sounds strange or odd, you have reasons to suspect it.
3. Go through the reviews and ratings of the app. But, note that these can be faked too.
4. Avoid downloading apps from third-party app stores.
5. Use a reliable mobile antivirus that can prevent fake and malicious apps from getting installed on your phone.

No Comments, Be The First!