Phishers using custom 404 Not Found error page to steal Microsoft credentials

In the latest of its kind phishing attacks, phishers have been found to use custom 404 Not Found error pages to run phishing campaign. This unusual phishing campaign is basically aimed at tricking unsuspecting victims into sharing their Microsoft login credentials.
A 404 Not Found page is typically an indication that you have landed on a broken or dead link, while trying to access a URL that does not exist. Interestingly, the 404 Not Found page can easily be customized to show a custom error page, which in this case happens to be a legitimate looking Microsoft sign-in page.
How does 404 Not Found phishing campaign work?
What attackers basically do is, they register a domain and configure the 404 Not Found page to display a malicious page containing fake Microsoft sign-in form. This custom HTML page gets displayed every time your browser triggers the 404 Not Found error.
The aim is to steal the Microsoft credentials of unsuspecting victims. So, as soon as you enter your details including your Microsoft email address, Skype name and phone number, all of these get sent to a phishing URL.
This also allows phishers to create virtually unlimited phishing landing pages to redirect their victims, that too by registering a single domain.
How to identify a phishing Microsoft sign-in landing page?
The malicious 404 Not Found page used by phishers to trick victims, is camouflaged to look exactly like the original Microsoft account login page, which makes it all the more easy to trick people into entering their Microsoft login credentials. Every link on this malicious page down to the smallest details like footer links, are made to direct to legitimate Microsoft login forms, to make endless unsuspecting victims fall prey to this phishing campaign.
So, then how do you identify that you have landed on a phishing Microsoft login page?
A legitimate Microsoft sign-in page will usually have a “Sign-in options” link visible just above the Next button.
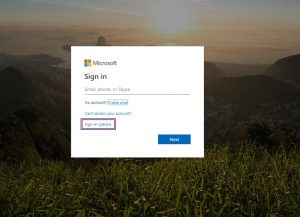
As against this, a phishing Microsoft sign-in page has this link completely missing along with the cookies notification usually visible at the top of the page. There is also a visible difference in the order in which the account access details appear on the form.
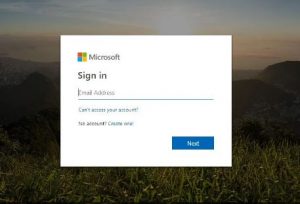
This is just one of the many ways in which phishers can create malicious landing pages via custom 404 Not Found page. There are reports of other self-hosted services that can be used to create these custom 404.html pages to trick unsuspecting victims.
So, as a precautionary measure, it is advisable to keep your eyes wide open and look through necessary details, especially when entering your details using any form. Remember that anything that looks too good to be true, is an indication that it requires double-check!!
No Comments, Be The First!