First Node.js-based Ransomware : Nodera

Recently while threat hunting, Quick Heal Security Labs came across an unusual Node.js framework based on Nodera ransomware. The use of the Node.js framework is not seen commonly across malware families. However, the latest development by threat actors reveals nasty and one-of-its-kind ransomware being created, one that uses the Node.js framework, which enables it to infect Windows-based OS.
Node.js is an open-source, cross-platform, JavaScript run-time environment that executes JavaScript code outside of a browser. It is built on the V8 JavaScript engine. V8 is Google’s open-source high-performance JavaScript and WebAssembly engine, written in C++. It is used in Chrome and in Node.js, among others. It implements ECMAScript and WebAssembly, and runs on Windows 7 or later, macOS 10.12+, and Linux systems that use x64, IA-32, ARM, or MIPS processors. V8 can run standalone or can be embedded into any C++ application.
Interestingly, users can easily get infected by this Nodera ransomware while browsing online, either by clicking on a malicious HTA file or when served as a malvertisement.
Analysis Details :
The sample received in our lab was a VBS script that has multiple embedded js scripts. On execution, it creates a directory “GFp0JAk” at location “%userprofile%\AppData\Local\”.
It also creates a sub-directory “node_modules” for storing Node.js libraries required to execute the JS payload. Finally, for the execution of those scripts, it requires node.exe, which will be downloaded from the below URL.
https://nodejs.org/download/release/latest-v8.x/win-x86/node.exe
Downloaded node.exe is stored as GFp0JAk.exe at “%userprofile%\AppData\Local\GFp0JAk”.
It further creates 3 different registry keys, “Microsoft Office”, “Startup”, and “Windows” at “HKCU\Software\Microsoft\Windows\CurrentVersion\Run\” to make its persistence in the system.
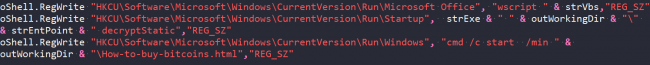
Fig 1: Registry Entry
It then drops some required libraries such as fs.js, graceful-fs.js, legacy-streams.js, package.json, polyfills.js at “%userprofile%\AppData\Local\GFp0JAk\node_modules\” and also the malicious JS “lLT8PCI.js” at “%userprofile%\AppData\Local\GFp0JAk\”.
Once all required modules are in place, it checks for “%userprofile%\AppData\Local\GFp0JAk\GFp0JAk.exe”. If it is present, it will start executing the script by invoking
oShell.Run(strExe & ” ” & outWorkingDir & “\” & strEntPoint, 0, true)
where strExe = “%userprofile%\AppData\Local\GFp0JAk\GFp0JAk.exe”
outWorkingDir = ”%userprofile%\AppData\Local\GFp0JAk\”
strEntPoint = “%userprofile%\AppData\Local\GFp0JAk\lLT8PCI.js”
The actual payload is the “lLT8PCI.js” script which performs all ransomware related activities.
In this script, for every user-defined function, the author has used Async-Await Generators and Promises. These two are the most powerful concepts of the Node.js framework. Defining any function prefix with Async keywords allows synchronously writing asynchronous code. The return value from the asynchronous function is called the promise, which checks for the completion status of a given function.
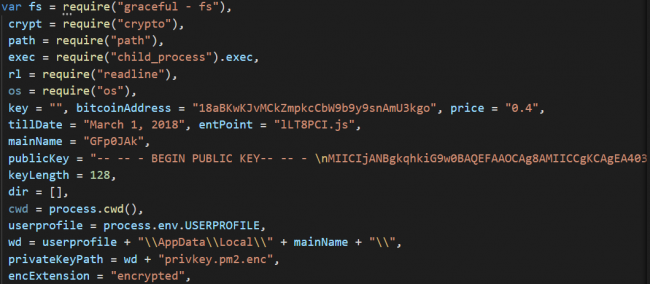
Fig 2: Initialization of variables and Public key
JS script starts with the initialization of some variables like “bitcoinAddress” and its price. Also, it embeds the RSA public key of 4096 bit in PEM format, as shown in Fig 2.
Fig 3: Functions used in the script
Initially, it checks for admin rights in “%WinDir%” by trying to create a file with name format {randomname_of_len_4}.{randomname_of_len_2}. “generateKey” function is used to generate random file name and extension.
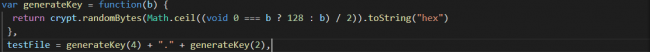
Fig 4: Generate file name and extension
Next, it invokes the scan function, which enumerates all the drives present in the system and creates a list. Only for the “C:” drive it has made some exclusion. It considers only the directories which contain user-specific files.
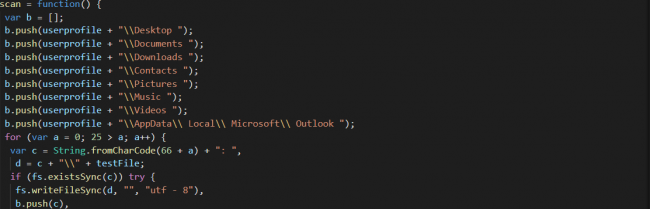
Fig 5: Targeted Directories
It will generate a file with the name “{randomname_of_len_6}.key”, which is used to store RSA encrypted AES-256 key. The AES key is generated by using the “generateKey” function.
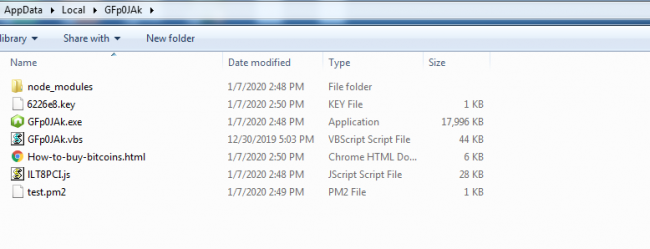
Fig 6: All Modules
Before encrypting the files, it kills the process as shown in the below fig and deletes volume shadow copy.
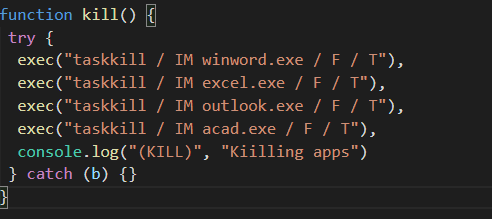
Fig 7: Process Killing
After encrypting a file, it appends the extension “.encrypted”.
Then it drops two files :
“%userprofile%\AppData\Local\GFp0JAk\“How-to-buy-bitcoins.html”
“%userprofile%\Desktop\Decrypt-your-files.bat”.
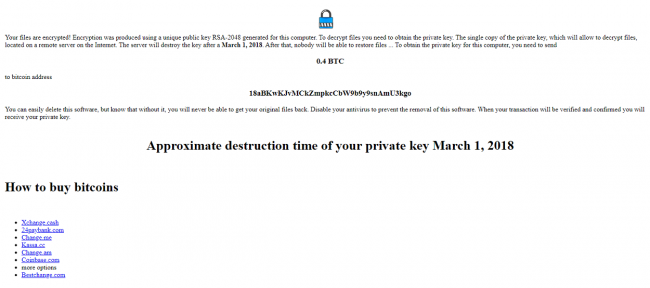
Fig 8: Ransom Note – How-to-buy-bitcoins.html
The HTML file is a ransomware note and batch file containing the command to execute the same JS script with the parameter “decryptStatic”, which invokes the decryption routine.
Fig 9: Encrypted Files
This ransomware seems to be in the development phase and has some flaws, as mentioned below:
- It mentions the RSA public key of the 2048 bit in the ransom note, although the public key embedded in the script is 4096 bits.
- Hard code destruction time of Private Key “March 1 2018”.
- There is no communication channel mentioned in the ransom note to receive the private key.
Although it seems to be written by an amateur developer, it is an interesting work, and the probability of it becoming popular in the future is quite high.
How Quick Heal protects its users from such attacks :
Quick Heal products are built with the following multi-layered security that helps counter such attacks.
- Anti-Ransomware
Specially designed to counter ransomware attacks. This feature detects ransomware by tracking its execution sequence.
- Firewall
Blocks malicious attempts to breach network connections.
- IDS/IPS
Detects RDP brute force attempts and blocks the remote attacker IP for a defined period.
- Virus Protection
Online virus protection service detects the known variants of the ransomware.
- Behaviour-based Detection System
Tracks the activity of executable files and blocks malicious files.
- Back-up and Restore
Helps you take regular backups of your data and restore it whenever needed.
IoCs :
7265C1FB74EB9EA3CD98358475620CE54B9033421BA042957135BDEFD078B366 53A95C9126BE8262AFB0821DA4D7137E6C8A4D9B363F91298249CA134D394BF4
Detection name :
VBS.NoderaRansom.36592
JS.NoderaRansom.36593


2 Comments
Hello,
You pointed that right in the beginning of the infection node.exe is downloaded and installed. Is this installation automatic or does it demand a kind of confirmation?
If there is a confirmation to be responded, it’s likely all the infection could be stopped by that point.
No, the downloaded file(Node.exe) is not an installer, it is a standalone executable and it provides the run time environment for the execution of Node js script.