Ficker – An Info-Stealer Malware that tricks people to get their passwords

Credential stealer malware is the most prevalent types of malware used in cyber-attacks. We have seen a lot of new stealer malware in the wild. The main objective of all credential stealer malware is to collect all confidential and sensitive information like user credentials and financial information.
Ficker Stealer is a family of information-stealing malware that emerged in 2020. Its capabilities include stealing sensitive information such as passwords, web browser passwords, cryptocurrency wallets, FTP client information, credentials stored by Windows Credential Manager, and session information from various chat and email clients.
Malware uses different techniques to get entry into a victim’s computer, like malicious email attachments, malicious online advertisements, social engineering etc. The infection process starts when Illegal activation tools (“cracks”) can be downloaded/installed instead of activating the licensed product. These phishing emails or malicious document downloaded are having a file attachment that contains macros to run the malware in the system. Recently we have seen that Hancitor malware also deliver Ficker Stealer.
At the time of analysis, the initial attack vector was unknown, but the attack chain was traced, through the malicious XLSM file that will be analyzed below. Quick Heal Security labs believe that the initial infection vector for this malware is an email with a malicious attachment.
XLSM File Analysis
The malicious document embedded with macro is not the usual VBA macro – it is XLS Macro. On clicking on Enable Editing, an embedded macro code will be activated, used by malware to download the malicious file.
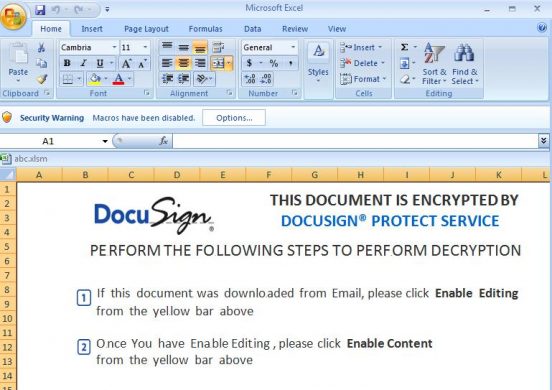
Fig 1: Malicious document asks users to enable a macro.
This malware uses OOXML format-based MS Excel file, which has the XLM macro sheets present in the “macro sheets” folder. This malware uses different folder and file name to store macro sheet that is suspicious. The macro sheet name is “proton.bin” as shown in the below image.
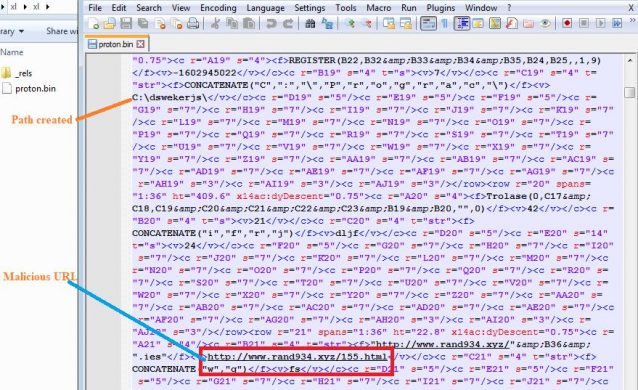
Fig 2. Malicious file Proton.bin in xlsm
Engines that checks for macro sheets, especially inside the “macro sheets” folder may fail to identify these files as XLM based Macro files. We investigated very carefully inside the “workbook.xml.rels” file and found the complete path of the file name “xl\proton.bin” for the macro sheet.
At the first look, workbook.xml.rels seems clean, and nothing related to malicious filename was found because malware authors have put its code in workbook.xml.rels at the end of the page and put blanks in between to evade the regular AV scans. By looking at the line number in the image below it can easily be understood.
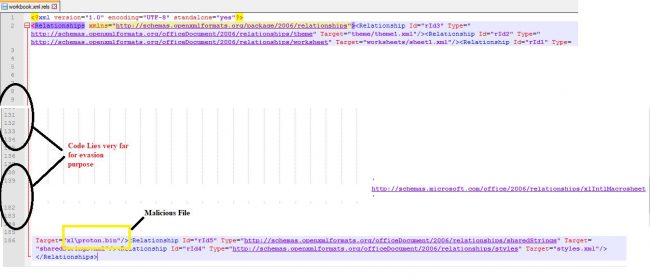
Fig 3. Evasion shows in File
This sample contains one hidden macro sheet which enables macro execution as soon as the file is opened. The font size of the content is kept small so that it will not be easily readable.
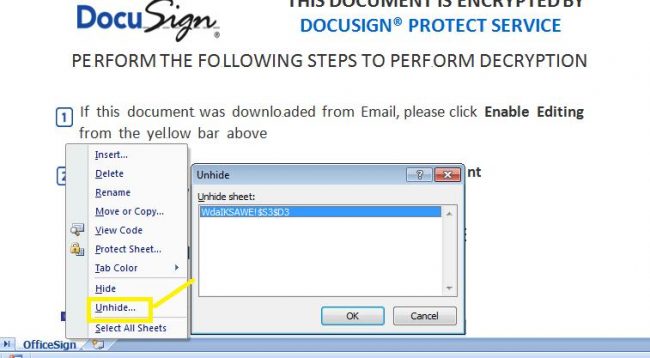
Fig 4. Hidden Sheet in XLSM
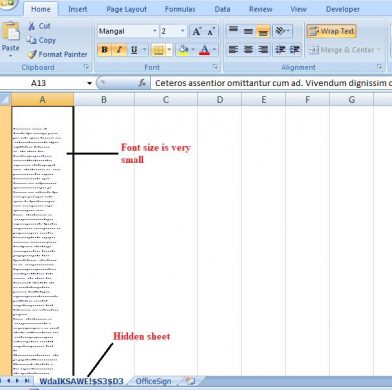
Fig 5. Hidden Sheet content
The malware creates a folder “C:\dswekerjs\dljffsrd\“, where it downloads the malicious file “ServApi.exe”.
Url used for downloading the payload is “http[:]//www[.]rand934[.]xyz/155.html“
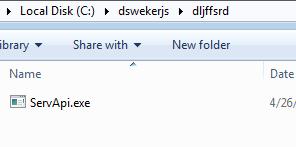
Fig 6. File downloaded by malware
Payload Analysis
During static analysis, we observed that the wrapper firstly calls “VirtualAlloc” to allocate memory so that it decrypts the actual payload in the memory. Malware uses two decryption loops as shown below.
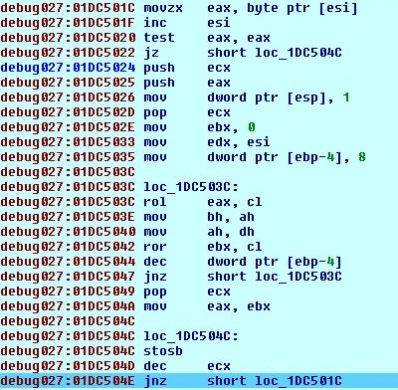
Fig 7. Decryption loop 1
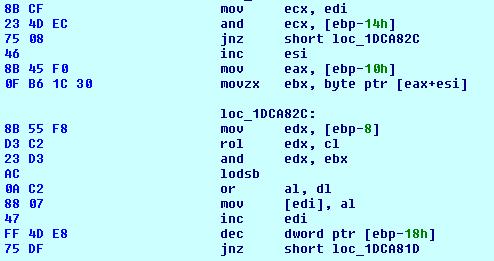
Fig 8. Decryption Loop 2
Malware decrypts the actual payload in memory which is kept obfuscated. It copies 0x158C bytes to a new location, which is kept at the lower part of decrypted buffer and then copies the remaining part of the new PE file in it.
Now the decrypted payload is executed. Firstly, it checks for internet connection if an internet connection is not found then it calls the sleep() function in the loop. If an internet connection is found, then it continues the execution.
Mutex created by the malware is “serhershesrhsfesrf”, mutex name is kept encrypted by the malware. The below image shows mutex created by malware:
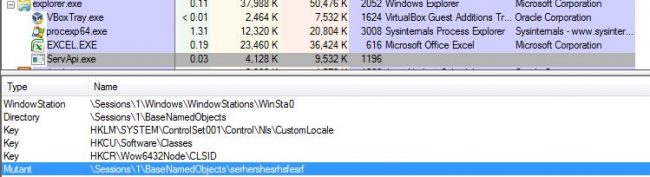
Fig 9. Mutex created by malware
The malware calls the function “GetUserDefaultLocaleName” which retrieves the locale name of the computer, and it will not execute if the following country codes are found:
ru-RU – Russia
ua-UA – Ukraine
kk-KZ – Kazakhstan
uz-UZ – Uzbekistan
hy-AM – Armenia
be-BY – Belarus
az-AZ – Azerbaijan
The malware calls the function “URLDownloadToFile()” and uses the URL “http://api.ipify.org/?format=xml” to get the external IP address of the device. It downloads the information from the web service and saves it to the file C:\ProgramData\kaosdma.txt.
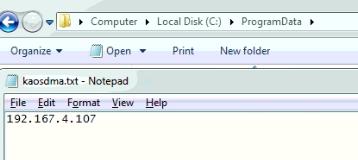
Fig 10. File created by malware
C2 used by the malware is “185.215.113.109:80”. C2 are the command centres from where malware receives its commands. They are also used to collect and store stolen data. Malware establishes a TCP connection using port 80. Malware uses the following sequence of APIs for communication.
Getaddrinfo()->connect()->send()->recv()->closesocket()
It enumerates running processes using Process32First() and process32Next(). It also collects information stored in files using FindFirstFileW() and FindNextFileW(). It collects all information in a buffer and then encrypt the buffer using simple XOR function and then send the data to the server.
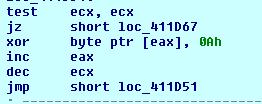
Fig 11.Loop for encryption
It tries to steal Crypto-Wallets, harvest and steal Bitcoin Wallet information, try to harvest and steal Putty / WinSCP information (sessions, passwords, etc.), and harvest and steal browser information (history, passwords, etc.) and steal Instant Messenger accounts or passwords, etc.
Stolen data can be used widely to gain unauthorized access to email accounts, bank accounts, and other online sources. This stolen personal information can harm the user mentally as well as financially. Ficker malware variants are successfully detected by Quick Heal products.
Conclusion
In the era of Ransomware, Infostealer malware is an equally popular attack vector used by attackers. We advise our users to avoid accessing suspicious websites/emails and keep their antivirus software up-to-date to prevent their systems from being infected by such complex malware. Quick Heal with its advanced detection technology, has been consistently monitoring & blocking these complex malware and malicious sites.
IOCs
8F442E8D149E52D4C038C377CEC1C32E (EXE)
B2989544E53D3BA2E0A2DDED1BF16524 (DOC)

No Comments, Be The First!