Expiro: Old Virus Poses a New Challenge

A recent virus infection faced by some users was swiftly detected as being caused by Expiro. We have conducted an in-depth investigation and analysis on the intricacies of Expiro and what makes it such a potent threat. This article lays out our analysis and understanding of the matter from our Security Research Lab and offers a detailed explanation on the necessary steps forward for those impacted.
Let’s begin.
About Expiro
Expiro is a file infector virus that damages and infects application files from users’ system by appending its virus code to the PE (executable) files.
Source
The infection vector for Expiro is observed to be from following sources: –
- Cracked or patched version of softwares
- Drive-by-download: Download of a file after visiting an infected website
- Dropped by some other malware
- USB drives
- Malvertising campaigns etc.
Expiro infects both 32-bit and 64-bit executable files. The new variant of Expiro is a type of “Appender” virus, that infects files by inserting virus code at the end of the file – specifically, at the end of the last section of executable file.
Behavioural Analysis:
Upon execution, Expiro adds the below-mentioned file to the system. The file is encrypted and contains stolen browser certificates and passwords.
- %AppData%\<random_hex_values>.bin
- Eg: %AppData%\60ca123a243237b7.bin
To make sure only one instance of Expiro is running onto infected system, below mutexes are created:
- \BaseNameObjects\SM0:<self_pid>:WilStagig_02
- \BaseNameObjects\Multiarch.m0yv-<random_hex_values>-inf
- \BaseNameObjects\Multiarch.m0yv-<random_hex_values>b7f3f232-b
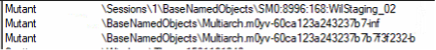
Fig-1: Mutex added by Expiro
Expiro then connects with remote servers and receives commands to execute on the infected systems.
File infection process:
While earlier variants of Expiro were patching a fixed pattern of codes at the start of entry point, this code can further jump to the last section containing actual virus codes.
Therefore, the recent variant of Expiro is patching a call in the executable section that further jumps to last section, at an offset where the malicious virus code is present.
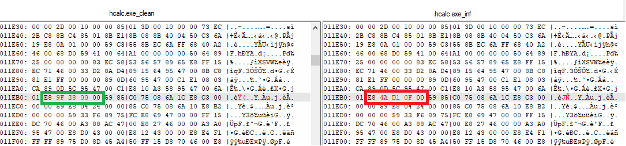
Fig – 2: Version of same file before and after Call patching
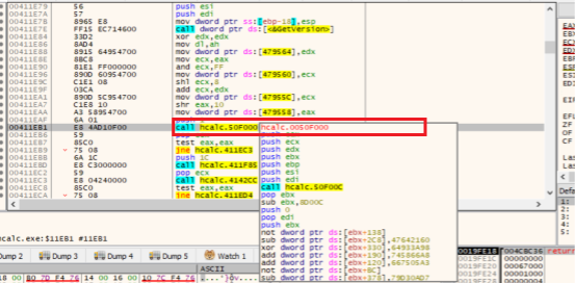
Fig-3: Patched call further jumps to last section having virus code
The code to calculate and select which Call to patch is highly obfuscated. After the Call is decided, it is overwritten by the offset of the virus code. Once the offset is written, it is difficult to restore the original offset.
The appended virus code is kept in an encrypted fashion. Decryption routine for this encrypted code uses combination of lengthy arithmetic and logical operations, making the decryption complex.
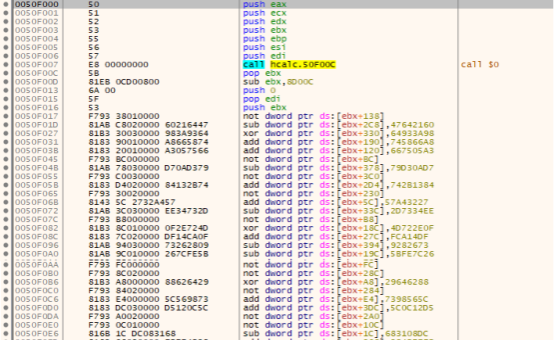
Fig 4: Part of a routine that decrypts Expiro code
The code is decrypted at runtime. Decrypted code contains a compressed buffer which decompresses at runtime. This decompressed buffer is again decrypted by implementing ChaCha and custom algorithms.
Upon analysing multiple files of this variant, we found that the decompressed buffer for most of the infected files remains same and the wrapper keeps changing. After successful decompression and decryption, the infected application is launched and that starts infecting other executables present in the system. The infection process is implemented in such a manner that the infected application works just as a normal one would, without the user’s knowledge of the application being infected.
What makes the restoration of files infected by Expiro challenging?
Due to the use of obfuscated call patching routine and encrypted virus code data, it is challenging to clean infected code with complete accuracy thereby leaving the executables at a high risk of instability.
After the call is patched, original addresses are encrypted with multiple layers followed by compression. Decompression and decryption of these addresses happens during run-time in memory. Calculation of these clean addresses and restoring it back is tricky and may result in corruption of the original file.
How Expiro operates
Once the system is infected with Expiro, it possesses worm like capabilities, where it checks for network mapped drives and infects executable files present in mapped network drives as well. This results in spreading the infection across the network.
Expiro connects to remote malicious CNC servers and acts as a backdoor by sending system information and receiving commands from remote servers.
Some attackers consciously keep their CnC servers unavailable at most times and bring them up only periodically.
Risks posed by Expiro
Having the ability to communicate with a remote CnC server, Expiro possesses capabilities to accept commands from its controller and execute them on the infected systems.
With successful commands delivered to victims, Expiro can:
– Install other malwares (like keyloggers, spywares, ransomware etc.)
– Steal and upload sensitive information
– Disable security software from the systems
– Hijack servers
– Establish itself to act at a later point in time
How to identify If the system or network is infected with Expiro
The Expiro Malware family is an “appender”, hence the residual symptoms of Expiro Malware is not unique. If your system is infected with Expiro you may see common symptoms as following:-
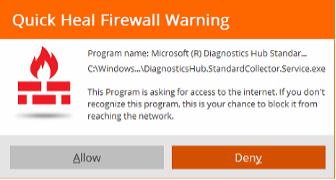
1.Quick Heal firewall shows a pop-up:
2. Application crashes
Customer installed applications may crash or exit frequently while you are working on them.
This can be confirmed by looking at the logs captured by Windows Operating system / Windows Application Event logs.
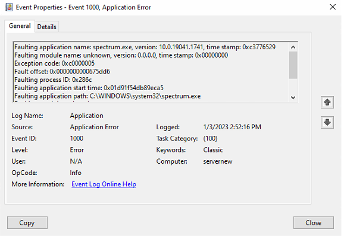
How to check Windows Application Event Logs?
- On Search bar, type “Event Viewer” and select the Event Viewer desktop app.
- In Event Viewer, expand Windows Logsfolder, and select the Application event log.
3.Quick Heal AV shows detection as below.
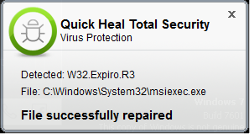
In case you are observing any of above symptoms in your system or within your intra-network then there is a high possibility that your system or network is infected with Expiro malware. In this case, we strongly recommend you to follow these steps:
- Protect all the machined in the network with Quick Heal / Seqrite Antivirus and make sure the Antivirus is updated with the latest virus definition date.
- System Scan: Perform full system scan on all nodes.
Note: If possible, scan all the Endpoints in an isolated mode – i.e. the system should not be connected to any network.
Once the scanning has been successfully completed you can check the Scan reports.
Steps to take if your system is infected
1) If Personal Application is infected
If an application is infected then it needs to be reinstalled from the Application Vendor’s website or by downloading it from a trusted source. You may restore your apps from a backup only after performing a complete scan of the backup and after ensuring it’s clean and safe.
Note: Please do not reinstall any applications until they are scanned and confirmed to be clean. Before installing a fresh copy of the application, scan the complete system to make sure that Expiro isn’t present on the machine; else the newly downloaded applications and installable may get infected again.
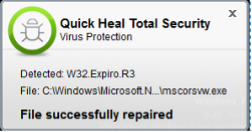
2) If the Operating system applications are infected
Expiro can infect Operating systems files such as Windows Installer Service [C:\Windows\system32\msiexec.exe] or system drive where Operating system has been installed. Refer the following screenshot: –
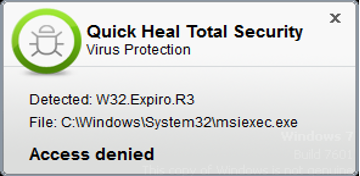
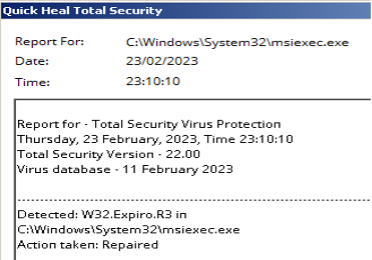
In such cases if the OS files are infected, then the safest option is to contact your IT admin to re-build the Operating system.
Note: The persistence of the Expiro Infection can be traceable via Antivirus Scan reports. By looking at the reports you will be able to bifurcate which drive, or application is infected.
Before connecting the system to a network, it’s important to validate the sanity of the system as well as the network. Connecting a fresh and cleaned system to a network which has Expiro infector hidden on any device may again infect this fresh system.
Quick Heal Detections
Quick Heal provides protection against all known variants of Expiro and detects it with the following signatures: –
- Expiro.R3
- Expiro.S28986130
- Expiro.S28994724
- SMB/Expiro.Infector!AR.47445
Steps to stay safe from this infection
- Avoid downloading and installing patched or cracked versions of any software.
- Install software only from genuine and trusted sources.
- Avoid websites that show unnecessary pop-ups or advertisements.
- Use USB Drives with extra cautions. Disable the Auto-Run function in your computer.
- Do not click on links or download attachments received in unknown, unwanted or unexpected emails.
- Always keep a secure backup of your important data – in a separate or unconnected device
- Keep your browsers, Operating System, and other software such as Adobe, Java, Antivirus, etc., up to date.
- Use a reliable antivirus software that puts layers of defense between your computer and malware threats.
- Make it a habit to read end-user license agreements and additional components installed by any software.
Subject Matter Experts:
Prashil Moon
Rumana Siddiqui
Ravi Gidwani
Parag Patil
Azam Raza

No Comments, Be The First!