CVE-2019-0708 – A Critical “Wormable” Remote Code Execution Vulnerability in Windows RDP

This is an important security advisory related to a recently patched Critical remote code execution vulnerability in Microsoft Windows Remote Desktop Service (RDP). The vulnerability is identified as “CVE-2019-0708 – Remote Desktop Services Remote Code Execution Vulnerability”.
MSRC blog mentions
This vulnerability is pre-authentication and requires no user interaction. In other words, the vulnerability is ‘wormable’, meaning that any future malware that exploits this vulnerability could propagate from one vulnerable computer to another vulnerable computer in a similar way as the WannaCry malware spread across the globe in 2017. While we have observed no exploitation of this vulnerability, it is highly likely that malicious actors will write an exploit for this vulnerability and incorporate it into their malware.
This vulnerability is a special case, as Microsoft went out of the way to patch this vulnerability in Windows 2003 and Windows XP as well, which have reached End of Support quite a long time ago.
Why this vulnerability is so Critical?
- It’s a pre-auth vulnerability, meaning it doesn’t require any authentication. Attackers just need network access of vulnerable target to exploit it.
- On successful exploitation, attackers can execute any arbitrary code on the target system and eventually take full control of it.
- Given the ‘wormable’ nature of this vulnerability, once a host is infected, it can infect other vulnerable hosts in the same network really fast.
- Microsoft went out of the way to patch it for older Windows versions, which have reached End of Support already.
- The vulnerability can be exploited over RDP port 3389. A simple search on www[.]shodan[.]io shows that there are close to 4 million hosts with RDP port open to Internet.
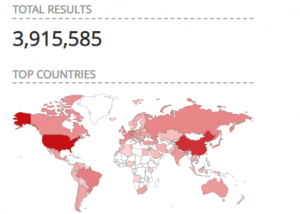
Fig. 1 – Shodan results showing Hosts with RDP port open to Internet
What should you do?
As per the Microsoft advisory and other online sources, this vulnerability is NOT actively getting exploited in the wild at the time of releasing this blog. Still, considering the business risk, we would like to urge users to patch their systems immediately, if they have any of the following affected Windows versions in use:
– Microsoft Windows 7 SP1
– Windows Server 2008 SP2
– Windows Server 2008 R2 – SP1
– Windows XP (All Versions)
– Windows Server 2003 SP2
If one cannot apply the Security Updates provided by Microsoft immediately, they should consider disabling the Remote Desktop Services on the vulnerable hosts until official patches are applied.
Our threat research team is actively monitoring this threat and we will keep updating this post accordingly.
Content Courtesy:
Pavan Thorat Security Labs
No Comments, Be The First!