Celebrity Photo Hack, Ice Bucket Malware, and Other IT Security News
The past few days in the world of Internet was mostly about the hoo-ha created over the major hack of celebrity personal photos. Let us read about this and other interesting IT security news.
Personal Photos of Jennifer Lawrence, and other A-List Celebrities Hacked
August 31, 2014 was a day full of shock and stir in the world of Internet. Over 200 photos, mostly intimate, of most A-list celebrities were leaked online. A hacker who goes by the name ‘original guy’ seems to have mastered this incident. Our CTO, Mr. Sanjay Katkar has shared his thoughts about how users can avoid such incidents by following just 3 safety measures. Read the post here.
Beware of Ice Bucket Challenge Emails, Links, and Social Media Posts
The Ice Bucket Challenge is a popular fundraising activity to support the fight against amyotrophic sclerosis (ALS). The campaign has been a great success since its inception. And this makes it a very attractive money-making proposition for online scammers. Scammers have started tricking people into downloading links embedded in emails related to this campaign. Clicking these links downloads a nasty malware on the victim’s computer. Know more about this here.
The Great Target Hack Might Have Been Accomplished in a Mere 11 Steps
Remember the great Target hack that occurred in early January this year? Well, if you are an IT security enthusiast, then you might want to know how the hackers did it. Would you believe if we say, ‘Just 11 steps?’ If no, then you can read all about how 70 million customers were hacked and 40 million credit/debit cards were stolen in just 11 steps, here.
Android Users Vulnerable to Man-in-the-Middle Attack
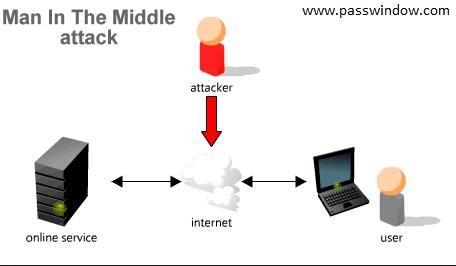
Those of you who still believe that Android is a a less favorite target of hackers, then here’s an update from the Computer Emergency Response (CERT) that might lay things into perspective. According to CERT, about 350 Android apps that are easily available in Google Play are vulnerable to man-in-the-middle attacks. These attacks allow hackers to intercept the flow of data between two legitimate parties. Having gathered the information, the attacker can manipulate or exploit the information for unscrupulous benefits. Know more about this here.



No Comments, Be The First!