It’s surprising to see how quickly attackers make use of new vulnerabilities in malware campaigns. Microsoft recently patched…
Tips
CVE-2019-11815: Experts discovered a privilege escalation vulnerability in the Linux Kernel
Red Hat engineers and experts discovered a memory corruption vulnerability in Linux kernel, which is basically a flaw…
Stay alert when planning your travels this holiday season
Planning a trip this holiday season? While, you spend a considerable amount of time shuffling money on online…
Beware of the Armage Ransomware – the File Destroyer!
In July last week, Quick Heal Security Labs detected a new ransomware called Armage. It appends ‘.Armage’ extension…
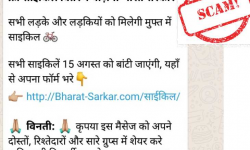
Beware of the ‘Free Cycle Distribution Yojana’ WhatsApp message. It’s fake!
As India’s Independence Day (15th of August) approaches, messages about free distribution schemes are doing the rounds on…
6 reasons why your computer is slower than a snail
Is your computer slowing down? Do you find it easier to move a mountain than multitasking on your…
Twitter bug attack: All you need to know & ways to fight such attacks
One company with a turnover of $2.44bn 330 million users 500 million tweets per day What does it…
Got a new Android phone this summer? Here are 6 tips to take good care of it!
Planning to get a new Android phone, or already got one recently? Then you must totally follow these…
8 tips to avoid a spyware attack
Spyware refers to software that spy on your Internet browsing activities, record keystrokes, and collect almost any type…
The A-Z dictionary of cybersecurity terms
Whether you are a normal user or a tech-guru, being aware of the computer security threats will help…