Alert! Wormable Android malware is spreading through social media applications

Autoreply is a convenient feature through which users can send a custom message as an automatic reply for unanswered incoming email, SMS, WhatsApp messages, and more. There are many applications on Google Play Store which offers such functionality.
We have recently noticed malicious applications which are abusing this particular functionality.

Fig 1. Content used for spreading malware
Fig 1 highlights samples of messages used by attackers to lure users into installing malicious apps. In many cases, these messages come from a trusted contact (who is already infected). As a result, users are likely to consider the message legitimate and follow the mentioned steps. In this case, the message asks users to open a web link and download an application. To lure users further, the website displays lucrative offers such as Free Netflix, watch Free IPL, New feature in WhatsApp. (Refer Fig.2)

Fig.2 Application hosting site
We recently analyzed two applications that are spreading through this mechanism – “WhatsApp Pink” and “Online stream.”

Fig.3 Icons
Once installed, these applications ask for notification access. After getting the permission, the application hides its icon from the users.
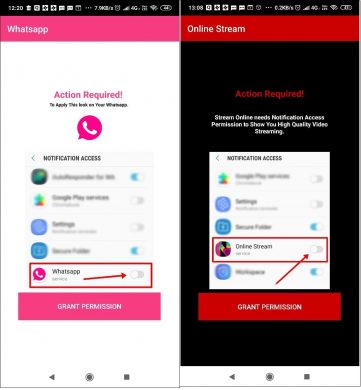
Fig.4 Asking Notification access
These applications maintain a list they target for auto-replies of apps such as Facebook, Instagram, WhatsApp, Twitter, Telegram, Skype, Viber, etc. Till now, we have seen two variants of lists (refer to Fig.5). These applications have another string array that has text messages with a link to download the applications. One of the message strings is selected at random at runtime.
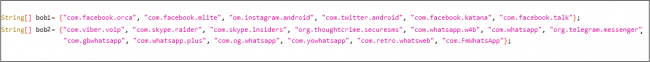
Fig.5 Target List
After getting notification access, whenever a new notification is received, the callback function onNotificationPosted gets called. In this method, the package name of the application is checked.
There is an additional check for Android notification direct reply action (The direct reply action, introduced in Android 7.0 (API level 24)), allowing users to enter text directly into the notification.
![]()
Fig. 6 onNotificationPosted function callback
In onNotificationPosted by accessing this action, instead of user input, this malware populates an intent with its own text data using RemoteInput.addResultsToIntent method.
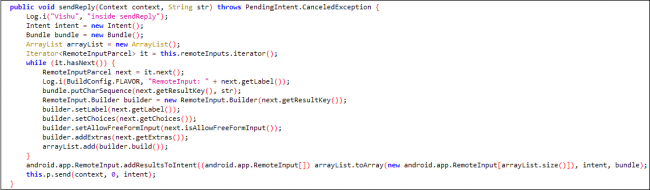
Fig.7 Sending the message
Same actor Behind these two variants:
Quick Heal has collected 6 samples of the WhatsApp Pink application and 4 samples of the Online stream application. All these applications are signed with the same certificate. That likely means that the same malware author (or authors) is behind these malicious applications.
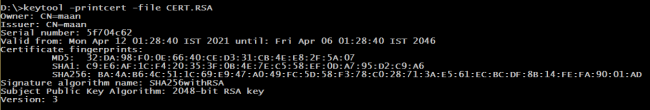
Fig. 8 Certificate Information
For now, these applications have functionalities of hiding icon, monitoring notifications, and autoreply. In future, they may develop a new variant and add more malicious functionality.
| IOC | Hosting sites |
| a8a687abf84271d181358374666b4f1b | h**p://pinkapp[.]xyz/?whatsapp |
| e1870d613d54239e8fb5f09b6a4e880d | h**p://lookpink[.]xyz/?whatsapp |
| d13d3eeaf8db5515577cc9b390fefbc9 | h**p://colorpink[.]xyz/?whatsapp |
| 9a902d186c948e72af6b269862c27055 | h**p://pinklook[.]profileviewz[.]com/WhatsappPink.apk h**p://whatsapp[.]profileviewz[.]com/WhatsappPink.apk |
| 90cfcde60b6cd57a2e9b2047cff51fb7 | h**p://whatsapp[.]wwwy[.]xyz/WhatsappPink.apk |
| 2ca849e5913aa3fd47db7b381db6ad24 | h**p://looknew[.]xyz/?whatsapp |
| 00d45a3846a90d7bd0d021447101efb6 3fa23903a9fa6f7d504f99e272c0d997 |
h**p://streamapp[.]club/?netflix |
| 2f0b61ef74e87b0aea52871d1bb4efb0 | h**p://mobilestream[.]club/?netflix |
| E1af660c6c71ad191749755aa057aef7 | h**p://profilelist[.]xyz/?livestream |
Follow the below guidelines to stay safe:
- Always download applications from legitimate sources like Google Play and App Store as these stores are relatively safe.
- Don’t click on unknown links shared on social media platforms, even if shared by your trusted contacts.
- If you have clicked on such shared link and installed the application, uninstall it by going to Settings >> Application list >> search for the application name (for these two variants, search Online stream and WhatsApp (Pink icon) and uninstall the application)
- Be extremely cautious about what applications you download on your phone.
- For enhanced protection of your phone, always use a good antivirus like Quick Heal Mobile Security for Android.



No Comments, Be The First!