Robin Hood Ransomware ‘GOODWILL’ Forces Victim for Charity

Goodwill Ransomware, identified by CloudSEK researchers in March 2022, is known to promote social justice on the internet. It is known to encrypt documents, databases, videos, or photos after it infects the whole system. The files become inaccessible for the victims, where Robinhood’ Goodwill’ asks the victim to donate for socially driven activities to get their files back. For example: ‘Goodwill Ransomware forces victims to donate new clothes to the homeless, provide financial assistance to the poor, and many more. They then ask victims to post it online.
However, a few more ransomware have other motives to force victims to do some act to retrieve their infected files. Quick heal published a blog about Sarbloh Ransomware related to the Farmer Protests and was not demanding any ransom. Similarly, Goodwill ransomware acts as a Robin Hood and forces victims to help the poor. Let us look into more detail about this ransomware and how the attacker gets hold of the files in the system.
Technical Analysis
Let us analyse the hash (MD5: cea1cb418a313bdc8e67dbd6b9ea05ad). This is a .NET Compiled file. This executable is packed with Fody; hence we can see only the main routine.
We can also observe references to Costura.
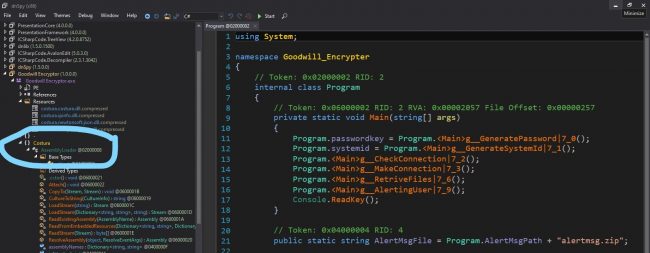
Fig 1: Costura References
This Costura is a plugin for Fody that allows the developers to embed all the dependencies in the form of resources packed inside the final dotNET executable.
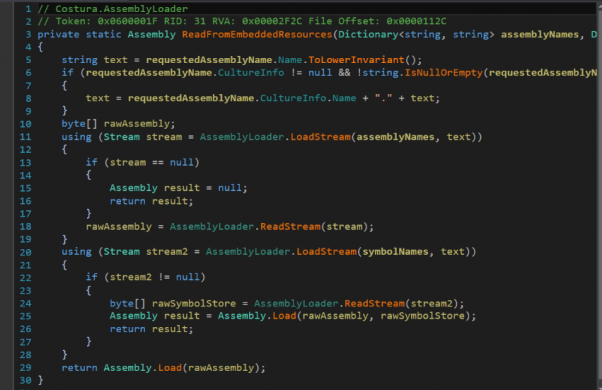
Fig2: Plugin
It can be seen in the above image how the embedded dependencies are fetched and unpacked.
Upon execution it connects to URL hxxp[:]//9855-13-235-50-147.ngrok[.]io/alertmsg[.]zip and downloads alertmsg.zip file into location: C:\Users\Public\Windows\Ui
All the content related to Ransom notes and encryption information is in the zip file. This executable coordinates with the contents of the zip. It encrypts the files with the extension “.gdwill.”
To recover the files, 3 activities need to be performed as shown below:
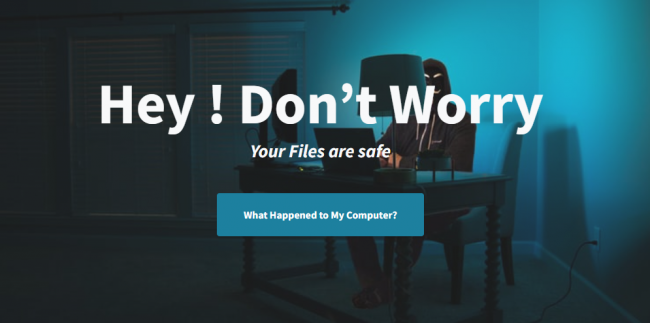
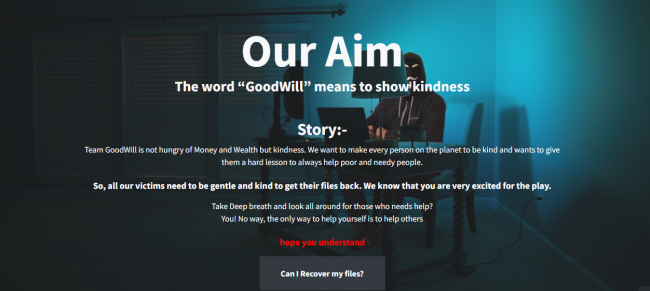
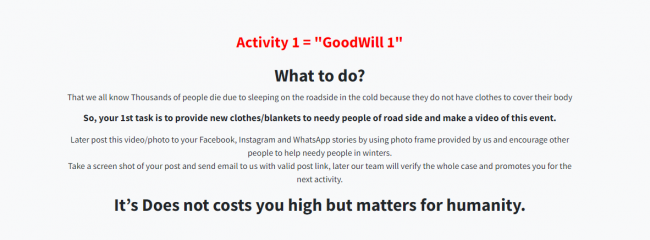
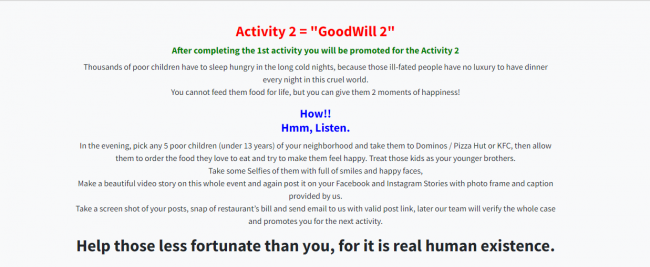
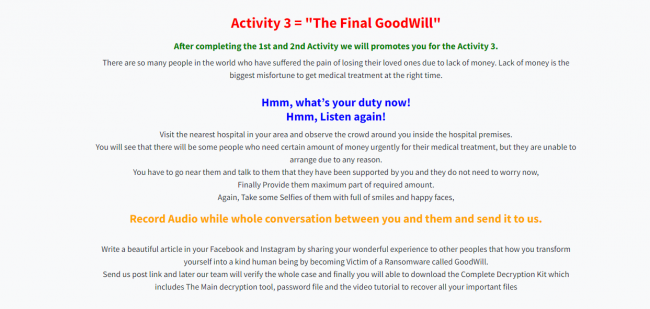
Fig 3: Ransom note
After completing all the given activities, the details must be sent to the email in the below format:

Fig 4: Email Format
The ransomware attackers ask the victims to provide convincing evidence for the activities to prove it done. After which, the person orchestrating this threat will provide a decryption tool to recover the stolen files. Let us look at how the threat actors hack and encrypt the files via the given below snapshot.
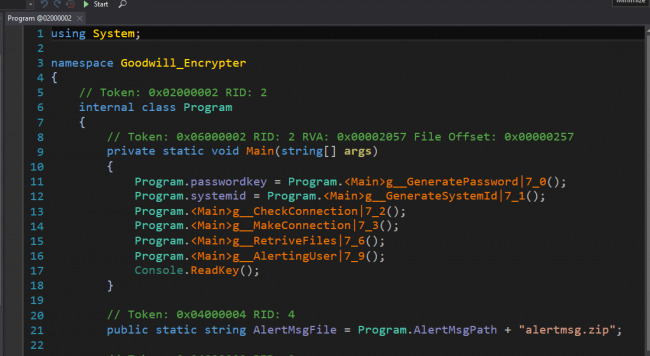
Fig 6: Encryption
Encryption Process
1.GeneratePassword: A password is randomly generated and then base64 encoded. The SHA256 of this base64 encoded data which later forms the key for encryption (AES)
2. GenerateSystemId: SystemID of the victim’s machine is obtained
3. CheckConnection: Pings google.com and checks if the internet is working
4. MakeConnection: Uploads the password and SystemID to the server along with location and IP
5.RetrieveFiles: AES Encryption is done on files with extension with a key generated in Step1 .pptx,.docx,.xlsx,.txt,.pdf,.500,.jpeg,.jpg,.png
6. AlertingUser: Launches index.html(containing ransom note) via launch.bat present in the alertmsg.zip
![]()
Fig 7: Batch file for alert
This malware also sleeps for a few seconds to bypass the analysis.
At last, it was found that this ransomware was derived from an Open-source Jasmin Encryptor, which can be found on https://github.com/codesiddhant/Jasmin-Ransomware.
How do we prevent such kinds of attacks?
To keep ourselves secure from such attacks, follow the great saying “Prevention is better than Cure”! The infection vector is usually in the form of mails, so do not open attachments from an untrusted sender. Do not enable macros in the Doc received mainly from correspondences. Avoid clicking on unverified links and those in spam emails. Keep your software and antivirus updated. Always remember to back up your data so that you can recover it even in case of a ransomware attack.
Conclusion
In the content above, we have looked into how Goodwill Ransom is related to Open-source Jasmin. It has modified the open-source for, e.g., In Jasmin, files are encrypted with the “.jasmin” extension, whereas GoodWill files are encrypted with “.gdwill.” In Jasmin, hosted points to localhost, whereas Goodwill points to external C2. This ransomware was unique because of its charitable nature instead of demanding money. The strings present in the file, such as “Error h bhaiyya,” seems that the routes of this hack were generated in India.
Indicators of compromise (IOC)
- cea1cb418a313bdc8e67dbd6b9ea05ad
QuickHeal Protection
Trojan.YakbeexMSIL.ZZ4



No Comments, Be The First!