BEWARE: Fake Applications are Disguised as Legitimate Ones

In the world of cybercrime, the tactics used by threat actors are constantly evolving, but upon close analysis of multiple instances, the modus operandi remains the same – i.e. exploitation of current events, trending news, government websites, and even legitimate applications of trusted organizations to dupe unsuspecting users.
By using the names and logos of trusted applications, scammers can easily lure people into downloading and installing malicious fake apps on their devices.
As cyber criminals are getting more creative and sophisticated in their social engineering techniques, it’s crucial for individuals and businesses to stay vigilant, and be aware of these potential threats. Not only that, it is also important to protect ourselves and our devices from these threat agents who are continuously looking for new avenues to target their victims and collect sensitive information for their own malicious purposes.
At Quick Heal Security Labs we actively monitor Cybersecurity news and other forums so that we stay abreast of the latest trends and threats. The intent is to ensure the complete digital safety & security of our customers. This is why we have taken our time to go through the recent advisory published by the Indian Railway Catering and Tourism Corporation (IRCTC), about the IRCTC fake apps. Read on to understand more about the Fake Application menace as we analyze the threat in detail.
The Fake IRCTC app portrays itself as the legitimate IRCTC app but is in reality a full-fledged spyware that spies on victims with ease.
This fake app Spyware is able to perform the following actions:
- Steal Facebook and Google account credentials.
- Use accessibility to extract codes from Google Authenticator.
- Track GPS and network location.
- Use the Camera API to record and send videos.
- Gather Installed Applications’ Information on the mobile device.
- Send all collected information to a C2 server, after which it can obfuscate to hide the host.
The Fake IRCTC App: How it Works

Fig 01. Fake App in the name of IRCTC.
When we click on the application icon to launch, it continuously shows us this screen, as given below.
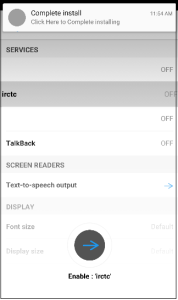
Fig 02. Continuously shows this screen.
The fake app then tries to obtain the following permissions on a mobile device:-
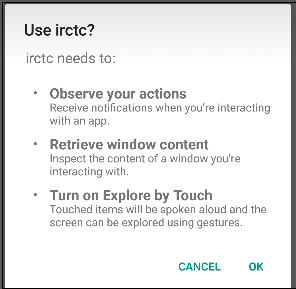
Fig 03. Fake app trying to get permissions on the infected device
Behind the scenes, this malware performs a number of malicious activities simultaneously, like stealing location and installed application data

Fig 04. Taking Installed Applications Information.
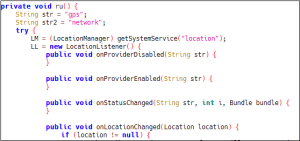
Fig 05. Taking Location Information
One of the features of this spyware is the ability to steal Facebook credentials:-
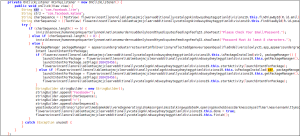
Fig 06. Social Media Credentials Stealing.
IRCTC ADVISORY:
It has been reported that a malicious Android application (irctcconnect.apk) hosted on a phishing website (https://irctc.creditmobile.site) is being circulated over instant messaging platforms e.g., WhatsApp, Telegram, etc.
This android app (APK file) is malicious and infects the mobile device. These fraudsters are sending phishing links at mass level and insisting users to download this android application, impersonating IRCTC officials to trick victims into revealing their sensitive net banking credentials like UPI details, credit/debit card information etc.
In view of this, you are advised that please do not install this application and keep yourself safe from such fraudsters.
Always download IRCTC’s authorized ‘IRCTC Rail Connect’ mobile app from Google Play Store or Apple Store.
Please note that IRCTC does not call its users/customers for their PIN, OTP, Password, Credit/Debit Card Details, Net Banking password or UPI details.
Warm Regards,
IRCTC
Quick Heal Detection:
Quick Heal is able to detect such malicious applications with variants of “Android.SpyNote.GEN.”
Indicator of Compromises (IOCs):
45c154af52c65087161b8d87e212435a
c01566f5feb7244ed4805e2855ebdc400
c77435e6e77152d24e86eb75e1f04d75
It is recommended that all mobile users should install a trusted Anti Virus like “Quick Heal Mobile Security for Android” to mitigate such threats and stay protected. Our antivirus software restricts users from downloading malicious applications on their mobile devices.
CONCLUSION:
As illustrated above, malware authors lure users by using icons of legitimate applications. These SpyNote applications can cause much harm to the infected devices. Users should be aware of such ongoing cyber scams and refrain from downloading and installing applications from untrusted sources.
TIPS TO STAY SAFE:
- Download applications only from trusted sources like Google Play Store.
- Do not click on any links received through messages or any other social media platforms as they may be intentionally or inadvertently pointing to malicious sites.
- Read the pop-up messages you get from the Android system before accepting or allowing any new permissions.
- Be extremely cautious about what applications you download on your phone, as malware authors can easily spoof the original applications’ names, icons, and developer details.
- For enhanced protection of your phone, always use a good antivirus like Quick Heal Mobile Security for Android.
No Comments, Be The First!