Phishing Scam Alert: Domain Name Expiration Notices stealing data through phishing site

Have you received an email notification that your domain is about to expire? Most website owners have. But do you pay close attention to who it is from and the renewal fee? If not, you may be throwing money away to a scammer.
Quick Heal Security Labs has recently come across a phishing scam related to domain names. And we want to give some insights on ways to identify the scam and protect yourself from falling victim.
Security researchers say expired domains can put data at risk. Hackers use expired domains to steal credit card data or contact information. Or they may target email accounts linked to the domain to scam clients and steal company secrets.
What is Phishing?
Phishing is a fraudulent attempt to obtain sensitive information such as usernames, passwords, and payment information by disguising oneself as a trustworthy entity in an electronic communication.
In other words, phishing is a type of online scam where criminals or attackers send an email that appears to be from a legitimate source or company and ask you to provide sensitive information.
There is a new phishing attack going on, which you need to be aware of a recent phishing email out there, the ‘Domain Name Expiration Scam.’ The target of this scam is to trick people with fake Domain Name Expiration to steal sensitive payment information from consumers or make payments to them.
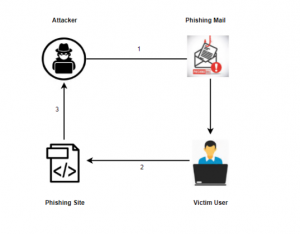 Fig. 1 Phishing attack flow
Fig. 1 Phishing attack flow
We observed a phishing mail attack during our analysis. The victim received multiple phishing emails on his registered mail from different Mail IDs. In the mail, attackers mentioned “Domain Services Expiration Date.” Attackers send fake Domain services expiration notices to the user. This date is not a correct expiration date.
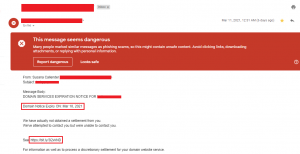
Fig.2 Phishing Email
In the above mail, shortened malicious URL is embedded which leads to a phishing attack.
https[:]//bit.ly/3l2vkND
This bitly URL redirects the user to another phishing website-
URL: https[:]//webdomainsrvcs.com
Information about the above URL and their respective:
URL: https[:]//webdomainsrvcs.com
- IP: 105.65.125
- Server Type: Apache
- Country: Russia
- City: Moscow
- ISP: HOSTKEY B.V.
- Organization: LLC Server v arendy (hostkey.ru)
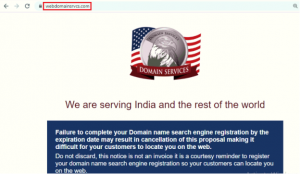
Fig.3 Phishing Site
This redirected website asks the victim to fill in some basic information like Domain name, Email address, Phone Number, and Digital signature, as shown below.
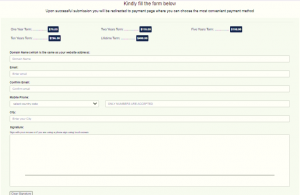
Fig.4 User Info page
After submitting details in the given form and clicking on submit button, it redirects to a page that will show some plans for domain renewal.
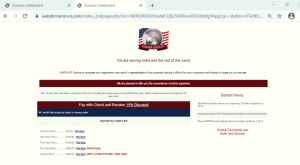
Fig.5: Domain renewal plans
After clicking on PAY NOW on any of the plans this page redirects the user to the payment page (PayPal).
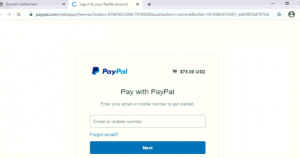
Fig.6: Payment page
VT Graph
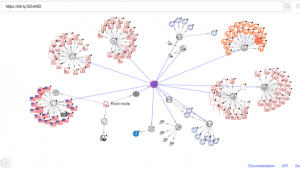
Fig.7 VT Graph
Here, we can see the Root node https[:]//bit.ly/3l2vkND is communicating with the malicious files.
How Can We Catch and Avoid Falling for these types of Phishing Scams?
- Validate Links and Attachment: Don’t click and open any Link and attachments attached in Mail validate it, then open it.
- Set up Auto-renewal: Use domain name auto-renewal services. So, you can ignore all renewal mails, which might be Phishing mail.
- Use Registrar’s website: Renew your domain name through the official registrar’s website only.
- Registration information: Use Domain privacy protection. It’s worth it.
IOCs:
Short URLs: These Shorten bit.ly URLs redirect to the below given malicious URLs.
- https[:]//bit.ly/3l2vkND
- https[:]//bit.ly/38sIQVM
- https[:]//bit.ly/2PSyhVH
- https[:]//bit.ly/3raUDj5
- https[:]//bit.ly/3qDXcc6
- https[:]//bit.ly/38tbshO
- https[:]//bit.ly/3pNezHb
Malicious URLs:
- http[:]//domainsrvcsexpiry.com/
- https[:]//domainsrvcsexpiry.com/03/09/2021be
- http[:]//domainsrvcsexpiry.com/03/09/2021bj/
- https[:]//domainsrvcsexpiry.com/03/09/2021ae
- http[:]//domainsrvcsexpiry.com/03/09/2021ab
No Comments, Be The First!